GSEC Exam Questions - Online Test
GSEC Premium VCE File

150 Lectures, 20 Hours

We provide real GSEC exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass GIAC GSEC Exam quickly & easily. The GSEC PDF type is available for reading and printing. You can print more and practice many times. With the help of our GIAC GSEC dumps pdf and vce product and material, you can easily pass the GSEC exam.
GIAC GSEC Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
The Return on Investment (ROI) measurement used in Information Technology and Information Security fields is typically calculated with which formula?
- A. ROI = (gain - expenditure)/(expenditure) X 100%
- B. ROI = (gain + expenditure)/(expenditure) X 100%
- C. ROI = (loss + expenditure)/(expenditure) X 100%
- D. ROI = (loss - expenditure)/(expenditure) X 100%
Answer: A
NEW QUESTION 2
What is the function of the TTL (Time to Live) field in IPv4 and the Hop Limit field in IPv6 In an IP Packet header?
- A. These fields are decremented each time a packet is retransmitted to minimize the possibility of routing loop
- B. These fields are initialized to an initial value to prevent packet fragmentation and fragmentation attack
- C. These fields are recalculated based on the required time for a packet to arrive at its destinatio
- D. These fields are incremented each time a packet is transmitted to indicate the number of routers that an IP packet has traverse
Answer: A
NEW QUESTION 3
On which of the following OSI model layers does IPSec operate? A. Physical layer
- A. Network layer
- B. Data-link layer
- C. Session layer
Answer: B
NEW QUESTION 4
Which of the following protocols describes the operation of security In H.323? A. H.239
- A. H.245
- B. H.235
- C. H.225
Answer: C
NEW QUESTION 5
An employee is currently logged into the corporate web server, without permission. You log into the web server as 'admin" and look for the employee's username: "dmaul" using the "who" command. This is what you get back: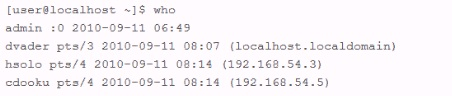
- A. The contents of the /var/log/messages file has been altered
- B. The contents of the bash history file has been altered
- C. The contents of the utmp file has been altered
- D. The contents of the http logs have been altered
Answer: B
NEW QUESTION 6
A US case involving malicious code is brought to trial. An employee had opened a helpdesk ticket to report specific instances of strange behavior on her system. The IT helpdesk representative collected information by interviewing the user and escalated the ticket to the system administrators. As the user had regulated and sensitive data on her computer, the system administrators had the hard drive sent to the company's forensic consultant for analysis and configured a new hard drive for the user. Based on the recommendations from the forensic consultant and the company's legal department, the CEO decided to prosecute the author of the malicious code. During the court case, which of the following would be able to provide direct evidence?
- A. The IT helpdesk representative
- B. The company CEO
- C. The user of the infected system
- D. The system administrator who removed the hard drive
Answer: C
NEW QUESTION 7
An employee attempting to use your wireless portal reports receiving the error shown below. Which scenario is occurring?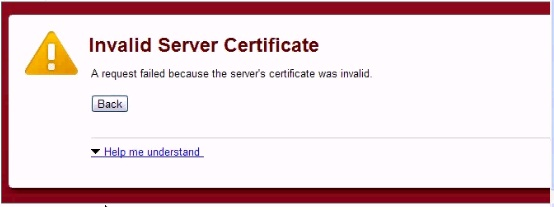
- A. A denial-of-service attack is preventing a response from the porta
- B. Another access point is deauthenticating legitimate client
- C. The encrypted data is being intercepted and decrypte
- D. Another access point is attempting to intercept the dat
Answer: D
NEW QUESTION 8
Which of the following languages enable programmers to store cookies on client computers? Each correct answer represents a complete solution. Choose two.
- A. DHTML
- B. Perl
- C. HTML
- D. JavaScript
Answer: BD
NEW QUESTION 9
When you log into your Windows desktop what information does your Security Access Token (SAT) contain?
- A. The Security ID numbers (SIDs) of all the groups to which you belong
- B. A list of cached authentications
- C. A list of your domain privileges
- D. The Security ID numbers (SIDs) of all authenticated local users
Answer: C
NEW QUESTION 10
Why are false positives such a problem with IPS technology?
- A. File integrity is not guarantee
- B. Malicious code can get into the networ
- C. Legitimate services are not delivere
- D. Rules are often misinterprete
Answer: D
NEW QUESTION 11
Which of the following Linux commands can change both the username and group name a file belongs to?
- A. chown
- B. chgrp
- C. chmod
- D. newgrp
Answer: B
NEW QUESTION 12
For most organizations, which of the following should be the highest priority when it comes to physical security concerns?
- A. Controlling ingress and egress
- B. Controlling access to workstations
- C. Ensuring employee safety
- D. Controlling access to servers
- E. Protecting physical assets
Answer: C
NEW QUESTION 13
What would the following IP tables command do?
IP tables -I INPUT -s 99.23.45.1/32 -j DROP
- A. Drop all packets from the source address
- B. Input all packers to the source address
- C. Log all packets to or from the specified address
- D. Drop all packets to the specified address
Answer: A
NEW QUESTION 14
Which of the following is a standard Unix command that would most likely be used to copy raw file system data for later forensic analysis?
- A. dd
- B. backup
- C. cp
- D. gzip
Answer: A
NEW QUESTION 15
You have implemented a firewall on the company's network for blocking unauthorized network connections. Which of the following types of security control is implemented in this case?
- A. Detective
- B. Preventive
- C. Directive
- D. Corrective
Answer: B
NEW QUESTION 16
CORRECT TEXT
Fill in the blank with the correct answer to complete the statement below.
The permission is the minimum required permission that is necessary for a user to enter a directory and list its contents.
- A.
Answer: Read
NEW QUESTION 17
You work as a Network Administrator for NetTech Inc. The company wants to encrypt its e-mails. Which of the following will you use to accomplish this?
- A. PPTP
- B. IPSec
- C. PGP
- D. NTFS
Answer: C
NEW QUESTION 18
Which Defense-in-Depth model involves identifying various means by which threats can become manifest and providing security mechanisms to shut them down?
- A. Vector-oriented
- B. Uniform protection
- C. Information centric defense
- D. Protected enclaves
Answer: A
NEW QUESTION 19
Which of the following services resolves host name to IP Address?
- A. Computer Browser
- B. DHCP
- C. DNS
- D. WINS
Answer: C
NEW QUESTION 20
......
Recommend!! Get the Full GSEC dumps in VCE and PDF From Thedumpscentre.com, Welcome to Download: https://www.thedumpscentre.com/GSEC-dumps/ (New 279 Q&As Version)
- All About Actual GSNA Study Guides
- Top Tips Of Rebirth GSNA Exam Question
- Leading GIAC Systems And Network Auditor GSNA Braindumps
- Renew GIAC Certified Incident Handler GCIH Samples
- How Many Questions Of GCIA Exam Question
- Validated GIAC GISF Practice Question Online
- A Review Of 100% Correct GCIA Exam Prep
- Improve GIAC Certified Intrusion Analyst GCIA Actual Test
- Far Out GIAC Security Essentials Certification GSEC Question
- All About 100% Correct GSEC Braindump

