GSEC Exam Questions - Online Test
GSEC Premium VCE File

150 Lectures, 20 Hours

It is impossible to pass GIAC GSEC exam without any help in the short term. Come to Pass4sure soon and find the most advanced, correct and guaranteed GIAC GSEC practice questions. You will get a surprising result by our Up to date GIAC Security Essentials Certification practice guides.
Free demo questions for GIAC GSEC Exam Dumps Below:
NEW QUESTION 1
Why would someone use port 80 for deployment of unauthorized services?
- A. Google will detect the service listing on port 80 and post a link, so that people all over the world will surf to the rogue servic
- B. If someone were to randomly browse to the rogue port 80 service they could be compromise
- C. This is a technique commonly used to perform a denial of service on the local web serve
- D. HTTP traffic is usually allowed outbound to port 80 through the firewall in most environment
Answer: D
NEW QUESTION 2
Which of the following terms refers to the process in which headers and trailers are added around user data?
- A. Encapsulation
- B. Authentication
- C. Authorization
- D. Encryption
Answer: A
NEW QUESTION 3
Analyze the screenshot below. What is the purpose of this message?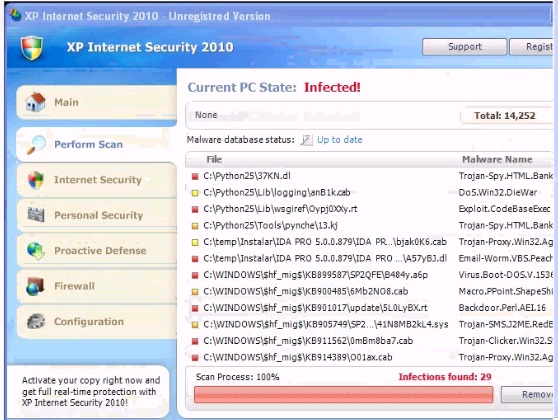
- A. To gather non-specific vulnerability information
- B. To get the user to download malicious software
- C. To test the browser plugins for compatibility
- D. To alert the user to infected software on the compute
Answer: D
NEW QUESTION 4
In addition to securing the operating system of production honey pot hosts, what is recommended to prevent the honey pots from assuming the identities of production systems that could result in the denial of service for legitimate users?
- A. Deploy the honey pot hosts as physically close as possible to production system
- B. Deploy the honey pot hosts in an unused part of your address spac
- C. Deploy the honey pot hosts to only respond to attack
- D. Deploy the honey pot hosts on used address spac
Answer: B
NEW QUESTION 5
Which choice best describes the line below?
alert tcp any any -> 192.168.1.0/24 80 (content: /cgi-bin/test.cgi"; msg: "Attempted
CGI-BIN Access!!";)
- A. Tcpdump filter
- B. IP tables rule
- C. Wire shark filter
- D. Snort rule
Answer: D
NEW QUESTION 6
What is SSL primarily used to protect you against?
- A. Session modification
- B. SQL injection
- C. Third-patty sniffing
- D. Cross site scripting
Answer: C
NEW QUESTION 7
Which of the following statements about IPSec are true?
Each correct answer represents a complete solution. Choose two.
- A. It uses Internet Protocol (IP) for data integrit
- B. It uses Authentication Header (AH) for data integrit
- C. It uses Password Authentication Protocol (PAP) for user authenticatio
- D. It uses Encapsulating Security Payload (ESP) for data confidentialit
Answer: BD
NEW QUESTION 8
You work as a Network Administrator for NetTech Inc. When you enter http://66.111.64.227 in the browser's address bar, you are able to access the site. But, you are unable to access the site when you enter http://www.uCertify.com. What is the most likely cause?
- A. DNS entry is not available for the host nam
- B. The site's Web server is offlin
- C. The site's Web server has heavy traffi
- D. WINS server has no NetBIOS name entry for the serve
Answer: A
NEW QUESTION 9
Your organization has broken its network into several sections/segments, which are separated by firewalls, ACLs and VLANs. The purpose is to defend segments of the network from potential attacks that originate in a different segment or that attempt to spread across segments.
This style of defense-in-depth protection is best described as which of the following?
- A. Uniform protection
- B. Protected enclaves
- C. Vector-oriented
- D. Information-centric
Answer: B
NEW QUESTION 10
Which of the following protocols implements VPN using IPSec?
- A. SLIP
- B. PPP
- C. L2TP
- D. PPTP
Answer: C
NEW QUESTION 11
The following three steps belong to the chain of custody for federal rules of evidence. What additional step is recommended between steps 2 and 3?
STEP 1 - Take notes: who, what, where, when and record serial numbers of machine(s) in question.
STEP 2 - Do a binary backup if data is being collected.
STEP 3 - Deliver collected evidence to law enforcement officials.
- A. Rebuild the original hard drive from scratch, and sign and seal the good backup in a plastic ba
- B. Conduct a forensic analysis of all evidence collected BEFORE starting the chain of custod
- C. Take photographs of all persons who have had access to the compute
- D. Check the backup integrity using a checksum utility like MD5, and sign and seal each piece of collected evidence in a plastic ba
Answer: D
NEW QUESTION 12
Which of the following is a backup strategy?
- A. Differential
- B. Integrational
- C. Recursive
- D. Supplemental
Answer: A
NEW QUESTION 13
What defensive measure could have been taken that would have protected the confidentiality of files that were divulged by systems that were compromised by malware?
- A. Ingress filtering at the host level
- B. Monitoring for abnormal traffic flow
- C. Installing file integrity monitoring software
- D. Encrypting the files locally when not in use
Answer: D
NEW QUESTION 14
Which of the following systems acts as a NAT device when utilizing VMware in NAT mode?
- A. Guest system
- B. Local gateway
- C. Host system
- D. Virtual system
Answer: D
NEW QUESTION 15
Which of the following works at the network layer and hides the local area network IP address and topology?
- A. Network address translation (NAT)
- B. Hub
- C. MAC address
- D. Network interface card (NIC)
Answer: A
NEW QUESTION 16
What is the name of the registry key that is used to manage remote registry share permissions for the whole registry?
- A. regkey
- B. regmng
- C. winreg
- D. rrsreg
Answer: C
NEW QUESTION 17
Which port category does the port 110 fall into?
- A. Well known port
- B. Dynamic port
- C. Private port
- D. Application port
Answer: A
NEW QUESTION 18
Which of the following attack vectors are addressed by Xinetd and TCP Wrappers?
- A. Outsider attack from network
- B. Outsider attack from a telephone
- C. Insider attack from local network
- D. Attack from previously installed malicious code
- E. A and B
- F. A and C
- G. B and D
- H. C and D
Answer: B
NEW QUESTION 19
Which of the following radio frequencies is used by the IEEE 802.11a wireless network?
- A. 3.7 GHz
- B. 7.0 GHz
- C. 2.4 GHz
- D. 5.0 GHz
Answer: D
NEW QUESTION 20
......
P.S. Easily pass GSEC Exam with 279 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com GSEC Dumps: https://www.dumps-hub.com/GSEC-dumps.html (279 New Questions)
- What Exact GCIA Testing Bible Is
- Top Tips Of Rebirth GSNA Exam Question
- Validated GIAC GISF Practice Question Online
- All About Download GCIH Preparation Labs
- All About Actual GSNA Study Guides
- Avant-garde GIAC Certified Incident Handler GCIH Exam Prep
- Leading GIAC Systems And Network Auditor GSNA Braindumps
- The Secret Of GIAC GSEC Exam Prep
- A Review Of 100% Correct GCIA Exam Prep
- What 100% Guarantee GSEC Practice Question Is

