GCIH Exam Questions - Online Test
GCIH Premium VCE File

150 Lectures, 20 Hours

Ucertify offers free demo for GCIH exam. "GIAC Certified Incident Handler", also known as GCIH exam, is a GIAC Certification. This set of posts, Passing the GIAC GCIH exam, will help you answer those questions. The GCIH Questions & Answers covers all the knowledge points of the real exam. 100% real GIAC GCIH exams and revised by experts!
Free demo questions for GIAC GCIH Exam Dumps Below:
NEW QUESTION 1
You are the Security Consultant and have been hired to check security for a client's network. Your client has stated that he has many concerns but the most critical is the security of Web applications on their Web server. What should be your highest priority then in checking his network?
- A. Setting up IDS
- B. Port scanning
- C. Vulnerability scanning
- D. Setting up a honey pot
Answer: C
NEW QUESTION 2
Drag and drop the mapping techniques to their respective descriptions.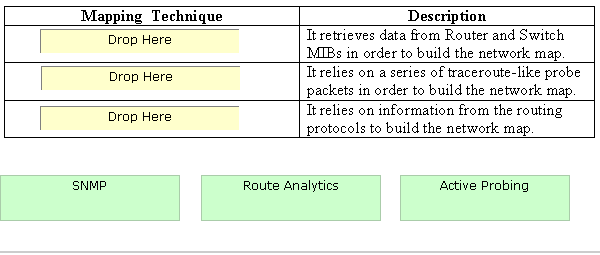
Solution:
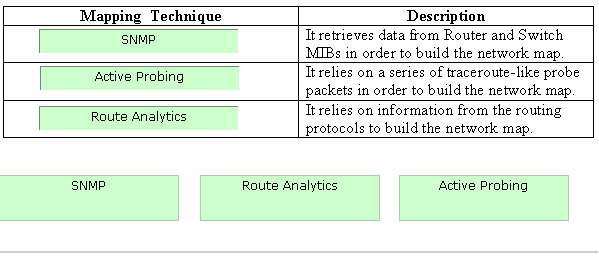
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 3
Which of the following virus is a script that attaches itself to a file or template?
- A. Boot sector
- B. Trojan horse
- C. Macro virus
- D. E-mail virus
Answer: C
NEW QUESTION 4
Firewalking is a technique that can be used to gather information about a remote network protected by a firewall. This technique can be used effectively to perform information gathering attacks. In this technique, an attacker sends a crafted packet with a TTL value that is set to expire one hop past the firewall. Which of the following are pre-requisites for an attacker to conduct firewalking?
Each correct answer represents a complete solution. Choose all that apply.
- A. An attacker should know the IP address of a host located behind the firewall.
- B. ICMP packets leaving the network should be allowed.
- C. There should be a backdoor installed on the network.
- D. An attacker should know the IP address of the last known gateway before the firewall.
Answer: ABD
NEW QUESTION 5
CORRECT TEXT
Fill in the blank with the appropriate term.
______ is a technique used to make sure that incoming packets are actually from the networks that they claim to be from.
- A.
Answer: Ingressfiltering
NEW QUESTION 6
John works as an Ethical Hacker for Exambible Inc. He wants to find out the ports that are open in Exambible's server using a port scanner. However, he does not want to establish a full TCP connection.
Which of the following scanning techniques will he use to accomplish this task?
- A. TCP FIN
- B. TCP SYN/ACK
- C. TCP SYN
- D. Xmas tree
Answer: C
NEW QUESTION 7
Which of the following protocol loggers is used to detect ping sweep?
- A. lppi
- B. pitl
- C. dpsl
- D. ippl
Answer: D
NEW QUESTION 8
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He has successfully completed the following steps of the pre- attack phase:
l Information gathering
l Determining network range
l Identifying active machines
l Finding open ports and applications
l OS fingerprinting
l Fingerprinting services
Now John wants to perform network mapping of the We-are-secure network. Which of the following tools can he use to accomplish his task?
Each correct answer represents a complete solution. Choose all that apply.
- A. Ettercap
- B. Traceroute
- C. Cheops
- D. NeoTrace
Answer: BCD
NEW QUESTION 9
Which of the following terms describes an attempt to transfer DNS zone data?
- A. Reconnaissance
- B. Encapsulation
- C. Dumpster diving
- D. Spam
Answer: A
NEW QUESTION 10
Victor works as a professional Ethical Hacker for SecureNet Inc. He wants to use Steganographic file system method to encrypt and hide some secret information. Which of the following disk spaces will he use to store this secret information?
Each correct answer represents a complete solution. Choose all that apply.
- A. Slack space
- B. Hidden partition
- C. Dumb space
- D. Unused Sectors
Answer: ABD
NEW QUESTION 11
Which of the following attacks allows an attacker to sniff data frames on a local area network (LAN) or stop the traffic altogether?
- A. Port scanning
- B. ARP spoofing
- C. Man-in-the-middle
- D. Session hijacking
Answer: B
NEW QUESTION 12
Adam works as a Security administrator for Umbrella Inc. He runs the following traceroute and notices that hops 19 and 20 both show the same IP address.
1 172.16.1.254 (172.16.1.254) 0.724 ms 3.285 ms 0.613 ms 2 ip68-98-176-1.nv.nv.cox.net
(68.98.176.1) 12.169 ms 14.958 ms 13.416 ms 3 ip68-98-176-1.nv.nv.cox.net
(68.98.176.1) 13.948 ms ip68-100-0-1.nv.nv. cox.net (68.100.0.1) 16.743 ms 16.207 ms 4 ip68- 100-0-137.nv.nv.cox.net (68.100.0.137) 17.324 ms 13.933 ms 20.938 ms 5 68.1.1.4
(68.1.1.4) 12.439 ms 220.166 ms 204.170 ms
6 so-6-0-0.gar2.wdc1.Level3.net (67.29.170.1) 16.177 ms 25.943 ms 14.104 ms 7
unknown.Level3.net (209.247.9.173) 14.227 ms 17.553 ms 15.415 ms "Exambible" - 8 so-0-1- 0.bbr1.NewYork1.level3.net (64.159.1.41) 17.063 ms 20.960 ms 19.512 ms 9 so-7-0-0.gar1.
NewYork1.Level3.net (64.159.1.182) 20.334 ms 19.440 ms 17.938 ms 10 so-4-0- 0.edge1.NewYork1.Level3.
net (209.244.17.74) 27.526 ms 18.317 ms 21.202 ms 11 uunet-level3- oc48.NewYork1.Level3.net
(209.244.160.12) 21.411 ms 19.133 ms 18.830 ms 12 0.so-6-0-0.XL1.NYC4.ALTER.NET (152.63.21.78)
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 13
Which of the following scanning tools is also a network analysis tool that sends packets with nontraditional IP stack parameters and allows the scanner to gather information from the response packets generated?
- A. Tcpview
- B. Nessus
- C. Legion
- D. HPing
Answer: D
NEW QUESTION 14
Which of the following can be used to perform session hijacking?
Each correct answer represents a complete solution. Choose all that apply.
- A. Cross-site scripting
- B. Session fixation
- C. ARP spoofing
- D. Session sidejacking
Answer: ABD
NEW QUESTION 15
Which of the following refers to applications or files that are not classified as viruses or Trojan horse programs, but can still negatively affect the performance of the computers on your network and introduce significant security risks to your organization?
- A. Hardware
- B. Grayware
- C. Firmware
- D. Melissa
Answer: B
NEW QUESTION 16
You want to add a netbus Trojan in the chess.exe game program so that you can gain remote access to a friend's computer. Which of the following tools will you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
- A. Tripwire
- B. Yet Another Binder
- C. Pretator Wrapper
- D. Beast
Answer: BC
NEW QUESTION 17
Who are the primary victims of smurf attacks on the contemporary Internet system?
- A. IRC servers are the primary victims to smurf attacks
- B. FTP servers are the primary victims to smurf attacks
- C. SMTP servers are the primary victims to smurf attacks
- D. Mail servers are the primary victims to smurf attacks
Answer: A
NEW QUESTION 18
Which of the following takes control of a session between a server and a client using TELNET, FTP, or any other non-encrypted TCP/IP utility?
- A. Dictionary attack
- B. Session Hijacking
- C. Trojan horse
- D. Social Engineering
Answer: B
NEW QUESTION 19
Which of the following statements about threats are true?
Each correct answer represents a complete solution. Choose all that apply.
- A. A threat is a weakness or lack of safeguard that can be exploited by vulnerability, thus causing harm to the information systems or networks.
- B. A threat is a potential for violation of security which exists when there is a circumstance, capability, action, or event that could breach security and cause harm.
- C. A threat is a sequence of circumstances and events that allows a human or other agent to cause an information-related misfortune by exploiting vulnerability in an IT product.
- D. A threat is any circumstance or event with the potential of causing harm to a system in the form of destruction, disclosure, modification of data, or denial of service.
Answer: BCD
NEW QUESTION 20
......
Recommend!! Get the Full GCIH dumps in VCE and PDF From Allfreedumps.com, Welcome to Download: https://www.allfreedumps.com/GCIH-dumps.html (New 328 Q&As Version)
- What Exact GCIA Testing Bible Is
- Far Out GIAC Security Essentials Certification GSEC Question
- How Many Questions Of GISF Exam Prep
- Improve GIAC Certified Intrusion Analyst GCIA Actual Test
- The Secret Of GIAC GSEC Exam Prep
- Avant-garde GIAC Certified Incident Handler GCIH Exam Prep
- A Review Of 100% Correct GCIA Exam Prep
- Leading GIAC Systems And Network Auditor GSNA Braindumps
- Highest Quality GIAC GCIH Dump Online
- Best Quality GIAC GSNA Free Demo Online

