GCIH Exam Questions - Online Test
GCIH Premium VCE File

150 Lectures, 20 Hours

Your success in GIAC GCIH is our sole target and we develop all our GCIH braindumps in a way that facilitates the attainment of this target. Not only is our GCIH study material the best you can find, it is also the most detailed and the most updated. GCIH Practice Exams for GIAC GCIH are written to the highest standards of technical accuracy.
Check GCIH free dumps before getting the full version:
NEW QUESTION 1
CORRECT TEXT
Fill in the blank with the appropriate word.
StackGuard (as used by Immunix), ssp/ProPolice (as used by OpenBSD), and Microsoft's /GS option use ______ defense against buffer overflow attacks.
- A.
Answer: canary
NEW QUESTION 2
Which of the following tools can be used as penetration tools in the Information system auditing process?
Each correct answer represents a complete solution. Choose two.
- A. Nmap
- B. Snort
- C. SARA
- D. Nessus
Answer: CD
NEW QUESTION 3
Adam, a malicious hacker purposely sends fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65,536 bytes. On the basis of above information, which of the following types of attack is Adam attempting to perform?
- A. Fraggle attack
- B. Ping of death attack
- C. SYN Flood attack
- D. Land attack
Answer: B
NEW QUESTION 4
An attacker sends a large number of packets to a target computer that causes denial of service.
Which of the following type of attacks is this?
- A. Spoofing
- B. Snooping
- C. Phishing
- D. Flooding
Answer: D
NEW QUESTION 5
Jason, a Malicious Hacker, is a student of Baker university. He wants to perform remote hacking on the server of DataSoft Inc. to hone his hacking skills. The company has a Windows-based network. Jason successfully enters the target system remotely by using the advantage of vulnerability. He places a Trojan to maintain future access and then disconnects the remote session. The employees of the company complain to Mark, who works as a Professional Ethical Hacker for DataSoft Inc., that some computers are very slow. Mark diagnoses the network and finds that some irrelevant log files and signs of Trojans are present on the computers. He suspects that a malicious hacker has accessed the network. Mark takes the help from Forensic Investigators and catches Jason.
Which of the following mistakes made by Jason helped the Forensic Investigators catch him?
- A. Jason did not perform a vulnerability assessment.
- B. Jason did not perform OS fingerprinting.
- C. Jason did not perform foot printing.
- D. Jason did not perform covering tracks.
- E. Jason did not perform port scanning.
Answer: D
NEW QUESTION 6
A user is sending a large number of protocol packets to a network in order to saturate its resources and to disrupt connections to prevent communications between services. Which type of attack is this?
- A. Vulnerability attack
- B. Impersonation attack
- C. Social Engineering attack
- D. Denial-of-Service attack
Answer: D
NEW QUESTION 7
Which of the following is a computer worm that caused a denial of service on some Internet hosts and dramatically slowed down general Internet traffic?
- A. Klez
- B. Code red
- C. SQL Slammer
- D. Beast
Answer: C
NEW QUESTION 8
Adam works as a sales manager for Umbrella Inc. He wants to download software from the Internet. As the software comes from a site in his untrusted zone, Adam wants to ensure that the downloaded software has not been Trojaned. Which of the following options would indicate the best course of action for Adam?
- A. Compare the file size of the software with the one given on the Website.
- B. Compare the version of the software with the one published on the distribution media.
- C. Compare the file's virus signature with the one published on the distribution.
- D. Compare the file's MD5 signature with the one published on the distribution media.
Answer: D
NEW QUESTION 9
You are hired as a Database Administrator for Jennifer Shopping Cart Inc. You monitor the server health through the System Monitor and found that there is a sudden increase in the number of logins.
A case study is provided in the exhibit. Which of the following types of attack has occurred? (Click the Exhibit button on the toolbar to see the case study.)
- A. Injection
- B. Virus
- C. Worm
- D. Denial-of-service
Answer: D
NEW QUESTION 10
You execute the following netcat command:
c:\target\nc -1 -p 53 -d -e cmd.exe
What action do you want to perform by issuing the above command?
- A. Listen the incoming data and performing port scanning
- B. Capture data on port 53 and performing banner grabbing
- C. Capture data on port 53 and delete the remote shell
- D. Listen the incoming traffic on port 53 and execute the remote shell
Answer: D
NEW QUESTION 11
Choose the correct actions performed during the Eradication step of the incident handling process.
Solution:
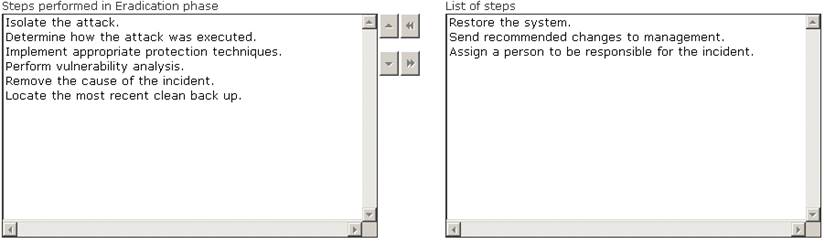
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He establishes a connection to a target host running a Web service with netcat and sends a bad html request in order to retrieve information about the service on the host.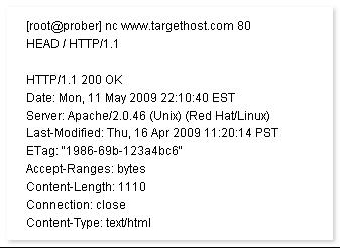
Which of the following attacks is John using?
- A. Sniffing
- B. Eavesdropping
- C. War driving
- D. Banner grabbing
Answer: D
NEW QUESTION 13
Many organizations create network maps of their network system to visualize the network and understand the relationship between the end devices and the transport layer that provide services.
Which of the following are the techniques used for network mapping by large organizations?
Each correct answer represents a complete solution. Choose three.
- A. Packet crafting
- B. Route analytics
- C. SNMP-based approaches
- D. Active Probing
Answer: BCD
NEW QUESTION 14
Which of the following applications automatically calculates cryptographic hashes of all key system files that are to be monitored for modifications?
- A. Tripwire
- B. TCPView
- C. PrcView
- D. Inzider
Answer: A
NEW QUESTION 15
Adam works as a Network administrator for Umbrella Inc. He noticed that an ICMP ECHO requests is coming from some suspected outside sources. Adam suspects that some malicious hacker is trying to perform ping sweep attack on the network of the company. To stop this malicious activity, Adam blocks the ICMP ECHO request from any outside sources.
What will be the effect of the action taken by Adam?
- A. Network turns completely immune from the ping sweep attacks.
- B. Network is still vulnerable to ping sweep attack.
- C. Network is protected from the ping sweep attack until the next reboot of the server.
- D. Network is now vulnerable to Ping of death attack.
Answer: B
NEW QUESTION 16
Which of the following malicious code can have more than one type of trigger, multiple task capabilities, and can replicate itself in more than one manner?
- A. Macro virus
- B. Blended threat
- C. Trojan
- D. Boot sector virus
Answer: B
NEW QUESTION 17
Which of the following statements about a Trojan horse are true?
Each correct answer represents a complete solution. Choose two.
- A. It is a macro or script that attaches itself to a file or template.
- B. The writers of a Trojan horse can use it later to gain unauthorized access to a computer.
- C. It is a malicious software program code that resembles another normal program.
- D. It infects the boot record on hard disks and floppy disks.
Answer: BC
NEW QUESTION 18
In which of the following scanning methods do Windows operating systems send only RST packets irrespective of whether the port is open or closed?
- A. TCP FIN
- B. FTP bounce
- C. XMAS
- D. TCP SYN
Answer: A
NEW QUESTION 19
Which of the following statements about Denial-of-Service (DoS) attack are true?
Each correct answer represents a complete solution. Choose three.
- A. It disrupts services to a specific computer.
- B. It changes the configuration of the TCP/IP protocol.
- C. It saturates network resources.
- D. It disrupts connections between two computers, preventing communications between services.
Answer: ACD
NEW QUESTION 20
......
Recommend!! Get the Full GCIH dumps in VCE and PDF From DumpSolutions.com, Welcome to Download: https://www.dumpsolutions.com/GCIH-dumps/ (New 328 Q&As Version)
- All About Download GCIH Preparation Labs
- How Many Questions Of GISF Exam Prep
- Renew GIAC Certified Incident Handler GCIH Samples
- What Exact GCIA Testing Bible Is
- What 100% Guarantee GSEC Practice Question Is
- Improve GIAC Certified Intrusion Analyst GCIA Actual Test
- Leading GIAC Systems And Network Auditor GSNA Braindumps
- The Secret Of GIAC GSEC Exam Prep
- Rebirth GIAC Certified Intrusion Analyst GCIA Free Practice Questions
- Validated GIAC GISF Practice Question Online

