GSNA Exam Questions - Online Test
GSNA Premium VCE File

150 Lectures, 20 Hours

we provide Verified GIAC GSNA exam question which are the best for clearing GSNA test, and to get certified by GIAC GIAC Systems and Network Auditor. The GSNA Questions & Answers covers all the knowledge points of the real GSNA exam. Crack your GIAC GSNA Exam with latest dumps, guaranteed!
Online GIAC GSNA free dumps demo Below:
NEW QUESTION 1
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to see the list of the filesystems mounted automatically at startup by the mount -a command in the /etc/rc startup file. Which of the following Unix configuration files can you use to accomplish the task?
- A. /etc/named.conf
- B. /etc/groups
- C. /etc/mtab
- D. /etc/fstab
Answer: D
Explanation:
In Unix, the /etc/fstab file is used by system administrators to list the filesystems that are mounted automatically at startup by the mount –a command (in /etc/rc or its equivalent startup file). Answer C is incorrect. In Unix, the /etc/mtab file contains a list of the currently mounted file systems. This is set up by the boot scripts and updated by the mount command. Answer A is incorrect. In Unix, the /etc/named.conf file is used for domain name servers. Answer B is incorrect. In Unix, the /etc/groups file contains passwords to let a user join a group.
NEW QUESTION 2
George works as an office assistant in Soft Well Inc. The company uses the Windows Vista operating system. He wants to disable a program running on a computer. Which of the following Windows Defender tools will he use to accomplish the task?
- A. Allowed items
- B. Quarantined items
- C. Options
- D. Software Explorer
Answer: D
Explanation:
Software Explorer is used to remove, enable, or disable a program running on a computer. Answer A is incorrect. Allowed items contains a list of all the programs that a user has chosen not to monitor with Windows Defender. Answer C is incorrect. Options is used to choose how Windows Defender should monitor all the programs running on a computer. Answer B is incorrect. Quarantined items is used to remove or restore a program blocked by Windows Defender.
NEW QUESTION 3
Which of the following types of servers are dedicated to provide resources to hosts on the network? (Choose three)
- A. Web servers
- B. Monitoring servers
- C. Mail servers
- D. Default gateway servers
- E. Print servers
Answer: ACE
Explanation:
Following types of servers are dedicated to provide resources to other hosts on the network: Mail servers Print servers Web servers Default gateway does not provide resources to hosts on the network. Monitoring server is not a type of server.
NEW QUESTION 4
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to print the super block and block the group information for the filesystem present on a system. Which of the following Unix commands can you use to accomplish the task?
- A. e2fsck
- B. dump
- C. dumpe2fs
- D. e2label
Answer: C
Explanation:
In Unix, the dumpe2fs command dumps the filesystem superblock and blocks the group information. Answer B is incorrect. In Unix, the dump command is used to back up an ext2 filesystem. Answer A is incorrect. The e2fsck command is used to check the second extended file system (E2FS) of a Linux computer. Syntax: e2fsck [options]
<device> Where, <device> is the file name of a mounted storage device (for example,
/dev/hda1). Several options are used with the e2fsck command. Following is a list of some important options: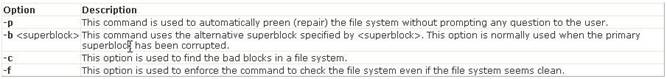
Answer D is incorrect. In Unix, the e2label command is used to change the label of an ext2 filesystem.
NEW QUESTION 5
Mark works as a Web Developer for XYZ CORP. He is developing a Web site for the company. The Manager of the company requires Mark to use tables instead of frames in the Web site. What is the major advantage that a table-structured Web site has over a frame-structured Web site?
- A. Easy maintenance
- B. Speed
- C. Better navigation
- D. Capability of being bookmarked or added to the Favorites folder
Answer: D
Explanation:
The major advantage that a table-structured Web site has over a frame- structured Web site is that users can bookmark the pages of a table- structured Web site, whereas pages of a frame-structured Web site cannot be bookmarked or added to the Favorites folder. Non-frame Web sites also give better results with search engines. Better navigation: Web pages can be divided into multiple frames and each frame can display a separate Web page. It helps in providing better and consistent navigation. Easy maintenance: Fixed elements, such as a navigation link and company logo page, can be created once and used with all the other pages. Therefore, any change in these pages is required to be made only once.
NEW QUESTION 6
Sam works as a Network Administrator for Blue Well Inc. All client computers in the company run the Windows Vista operating. Sam creates a new user account. He wants to create a temporary password for the new user such that the user is forced to change his password when he logs on for the first time. Which of the following options will he choose to accomplish the task?
- A. User cannot change password
- B. Delete temporary password at next logon
- C. User must change password at next logon
- D. Password never expires
Answer: C
Explanation:
Enabling the user must change password at next logon option will make the given password a temporary password. Enabling this option forces a user to change his existing password at next logon. Answer B is incorrect. There is no such option in Windows Vist Answer D is incorrect. This option sets the password to never expire. Answer A is incorrect. This option sets the existing password as a permanent password for the user. Only administrators can change the password of the user.
NEW QUESTION 7
Which of the following tools can be used by a user to hide his identity?
- A. War dialer
- B. IPchains
- C. Proxy server
- D. Rootkit
- E. Anonymizer
Answer: BCE
Explanation:
A user can hide his identity using any firewall (such as IPChains), a proxy server, or an anonymizer.
NEW QUESTION 8
You have just installed a Windows 2003 server. What action should you take regarding the default shares?
- A. Disable them only if this is a domain server.
- B. Disable them.
- C. Make them hidden shares.
- D. Leave them, as they are needed for Windows Server operations.
Answer: B
Explanation:
Default shares should be disabled, unless they are absolutely needed. They pose a significant security risk by providing a way for an intruder to enter your machine. Answer A is incorrect. Whether this is a domain server, a DHCP server, a file server, or database server does not change the issue with shared drives/folders. Answer C is incorrect. They cannot be hidden. Shared folders are, by definition, not hidden but rather available to users on the network. Answer D is incorrect. These are not necessary for Windows Server operations.
NEW QUESTION 9
Which of the following are attributes of the <TABLE> tag? (Choose three)
- A. BORDER
- B. ALIGN
- C. TD
- D. WIDTH
Answer: ABD
Explanation:
The WIDTH attribute of the <TABLE> tag is used to set the width of a table. Width can be specified in pixels and percentage. For example, if a table of the same width as that of the parent object has to be created, the WIDTH attribute must be set to 100%. The ALIGN attribute aligns the table within the text flow. By default alignment is set to left. The BORDER attribute of the <TABLE> tag is used to set the width of the table border. Answer C is incorrect. <TD> is not an attribute of the <TABLE> tag. It is a tag used to specify cells in a table.
NEW QUESTION 10
Anonymizers are the services that help make a user's own Web surfing anonymous. An anonymizer removes all the identifying information from a user's computer while the user surfs the Internet. It ensures the privacy of the user in this manner. After the user anonymizes a Web access with an anonymizer prefix, every subsequent link selected is also automatically accessed anonymously. Which of the following are limitations of anonymizers?
- A. ActiveX controls
- B. Plugins
- C. Secure protocols
- D. Java applications
- E. JavaScript
Answer: ABCDE
Explanation:
Anonymizers have the following limitations: 1.HTTPS: Secure protocols such as 'https:' cannot be properly anonymized, as the browser needs to access the site directly to properly maintain the secure encryption. 2.Plugins: If an accessed site invokes a third-party plugin, there is no guarantee of an established independent direct connection from the user computer to a remote site. 3.Java: Any Java application accessed through an anonymizer will not be able to bypass the Java security wall. 4.ActiveX: ActiveX applications have almost unlimited access to the user's computer system. 5.JavaScript: The JavaScript scripting language is disabled with URL-based anonymizers.
NEW QUESTION 11
Which of the following wireless security standards supported by Windows Vista provides the highest level of security?
- A. WPA-EAP
- B. WEP
- C. WPA-PSK
- D. WPA2
Answer: D
Explanation:
WPA2 is an updated version of WPA. This standard is also known as IEEE 802.11i. WPA2 offers enhanced protection to wireless networks than WPA and WEP standards. It is also available as WPA2-PSK and WPA2-EAP for home and enterprise environment respectively. Answer B is incorrect. than WEP (Wired Equivalent Protection).
Windows Vista supports both WPA-PSK and WPA-EAP. Each of these is described as follows: WPA-PSK: PSK stands for Preshared key. This standard is meant for home environment. WPA-PSK requires a user to enter an 8- character to 63-character passphrase into a wireless client. The WPA converts the passphrase into a 256-bit key. WPA-EAP: EAP stands for Extensible Authentication Protocol. This standard relies on a back-end server that runs Remote Authentication Dial-In User Service for user authentication. Note: Windows Vista supports a user to use a smart card to connect to a WPA-EAP protected network.
NEW QUESTION 12
You run the wc -c file1.txt command. If this command displays any error message, you want to store the error message in the error.txt file. Which of the following commands will you use to accomplish the task?
- A. wc -c file1.txt >>error.txt
- B. wc -c file1.txt 1>error.txt
- C. wc -c file1.txt 2>error.txt
- D. wc -c file1.txt >error.txt
Answer: C
Explanation:
According to the scenario, you will use the wc -c file1.txt 2>error.txt command to accomplish the task. The 2> operator is an error redirector, which, while running a command, redirects the error (if it exists) on the specified file. Answer B, D are incorrect. The > or 1> redirector can be used to redirect the output of the wc -c file1.txt file to the error.txt file; however, you want to write the errors in the error.txt file, not the whole output. Answer A is incorrect. The >> operator will redirect the output of the command in the same manner as the > or 1> operator. Although the >> operator will not overwrite the error.txt file, it will append the error.txt file.
NEW QUESTION 13
Which of the following statements about the <web-resource-collection> element are true?
- A. It has <web-resource-name> as one of its sub-elements.
- B. If there is no <http-method> sub-element, no HTTP method will be constrained.
- C. It can have at the most one <url-pattern> sub-element.
- D. It is a sub-element of the <security-constraint> element.
Answer: AD
Explanation:
The <web-resource-collection> element is a sub-element of the <security-
constraint> element and specifies the resources that will be constrained. Each <security- constraint> element should have one or more <web-resource-collection> sub-elements. The syntax of the <web-resource-collection> element is as follows: <security-constraint>
<web-resource-collection> <web-resource-name>ResourceName</web-resource-name>
<http-method>GET</http-method> <url-pattern>PatternName</url-pattern> </web- resource-collection> </security-constraint> The sub-elements of the <web-resource- collection> element are as follows: <web-resource-name>: This mandatory sub-element is the name of the Web resource collection. <description>: This is an optional sub-element that specifies a text description of the current security constraint. <http-method>: This optional sub-element specifies HTTP methods that are constrained. <url-pattern>: This sub-element specifies the URL to which the security constraint applies. There should be atleast one url-pattern element; otherwise, the <web-resource-collection> will be ignored. Answer C is incorrect. The <web-resource-collection> element can have any number of
<url-pattern> sub-elements. Answer B is incorrect. If there is no <http-method> sub- element, no HTTP methods will be allowed.
NEW QUESTION 14
Which of the following commands can be used to intercept and log the Linux kernel messages?
- A. syslogd
- B. klogd
- C. sysklogd
- D. syslog-ng
Answer: BC
Explanation:
The klogd and sysklogd commands can be used to intercept and log the Linux kernel messages.
NEW QUESTION 15
An auditor assesses the database environment before beginning the audit. This includes various key tasks that should be performed by an auditor to identify and prioritize the users, data, activities, and applications to be monitored. Which of the following tasks need to be performed by the auditor manually?
- A. Classifying data risk within the database systems
- B. Monitoring data changes and modifications to the database structure, permission and user changes, and data viewing activities
- C. Analyzing access authority
- D. Archiving, analyzing, reviewing, and reporting of audit information
Answer: AC
Explanation:
The Internal Audit Association lists the following as key components of a database audit: Create an inventory of all database systems and use classifications. This should include production and test data. Keep it up-to-date. Classify data risk within the database systems. Monitoring should be prioritized for high, medium, and low risk data. Implement an access request process that requires database owners to authorize the "roles" granted to database accounts (roles as in Role Based Access and not the native database roles). Analyze access authority. Users with higher degrees of access permission should be under higher scrutiny, and any account for which access has been suspended should be monitored to ensure access is denieA, Dttempts are identified. Assess application coverage. Determine what applications have built-in controls, and prioritize database auditing accordingly. All privileged user access must have audit priority. Legacy and custom applications are the next highest priority to consider, followed by the packaged applications. Ensure technical safeguards. Make sure access controls are set properly. Audit the activities. Monitor data changes and modifications to the database structure, permission and user changes, and data viewing activities. Consider using network-based database activity monitoring appliances instead of native database audit trails. Archive, analyze, review, and report audit information. Reports to auditors and IT managers must communicate relevant audit information, which can be analyzed and reviewed to determine if corrective action is required. Organizations that must retain audit data for long-term use should archive this information with the ability to retrieve relevant data when needed. The first five steps listed are to be performed by the auditor manually. Answer B, D are incorrect. These tasks are best achieved by using an automated solution.
NEW QUESTION 16
Which of the following is Microsoft's implementation of the file and application server for the Internet and private intranets?
- A. Internet Server Service (ISS)
- B. Internet Server (IS)
- C. WWW Server (WWWS)
- D. Internet Information Server (IIS)
Answer: D
Explanation:
Microsoft Internet Information Server (IIS) is a WeA, Bpplication server for the Internet and private intranets. IIS receives requests from users on the network using the World Wide Web (WWW) service and transmits information using the Hypertext Transport Protocol (HTTP). IIS uses Microsoft Transaction Server (MTS) to provide security, performance, and scalability with server side packages.
NEW QUESTION 17
Which TCP and UDP ports can be used to start a NULL session attack in NT and 2000 operating systems?
- A. 149 and 133
- B. 203 and 333
- C. 139 and 445
- D. 198 and 173
Answer: C
Explanation:
A null session is an anonymous connection to a freely accessible network share called IPC$ on Windows-based servers. It allows immediate read and write access with Windows NT/2000 and read-access with Windows XP and 2003. The command to be inserted at the DOS-prompt is as follows: net use \\IP address_or_host name\ipc$ "" "/user:" net use Port numbers 139 TCP and 445 UDP can be used to start a NULL session attack.
NEW QUESTION 18
......
100% Valid and Newest Version GSNA Questions & Answers shared by Thedumpscentre.com, Get Full Dumps HERE: https://www.thedumpscentre.com/GSNA-dumps/ (New 368 Q&As)
- A Review Of Guaranteed GCIH Pdf Exam
- How Many Questions Of GISF Exam Prep
- All About Actual GSNA Study Guides
- What Exact GCIA Testing Bible Is
- The Renovate Guide To GISF Exam Question
- The Secret Of GIAC GSEC Exam Prep
- Leading GIAC Systems And Network Auditor GSNA Braindumps
- All About Download GCIH Preparation Labs
- Avant-garde GIAC Certified Incident Handler GCIH Exam Prep
- Top Tips Of Rebirth GSNA Exam Question

