GSNA Exam Questions - Online Test
GSNA Premium VCE File

150 Lectures, 20 Hours

Want to know Pass4sure GSNA Exam practice test features? Want to lear more about GIAC GIAC Systems and Network Auditor certification experience? Study 100% Correct GIAC GSNA answers to Up to the immediate present GSNA questions at Pass4sure. Gat a success with an absolute guarantee to pass GIAC GSNA (GIAC Systems and Network Auditor) test on your first attempt.
Check GSNA free dumps before getting the full version:
NEW QUESTION 1
Which of the following are the disadvantages of Dual-Homed Host Firewall Architecture?
- A. It can provide services by proxying them.
- B. It can provide a very low level of control.
- C. User accounts may unexpectedly enable services a user may not consider secure.
- D. It provides services when users log on to the dual-homed host directly.
Answer: ACD
Explanation:
A dual-homed host is one of the firewall architectures for implementing preventive security. It provides the first-line defense and protection technology for keeping untrusted bodies from compromising information security by violating trusted network space as shown in the image below: A dual-homed host (or bastion host) is a system fortified with two network interfaces (NICs) that sits between an un-trusted network (like the Internet) and trusted network (such as a corporate network) to provide secure access. Dual-homed, or bastion, is a general term for proxies, gateways, firewalls, or any server that provides secured applications or services directly to an untrusted network.
A dual-homed host also has some disadvantages, which are as follows:
* 1. It can provide services by proxying them.
* 2. User accounts may unexpectedly enable services a user may not consider secure.
* 3. It provides services when users log on to the dual-homed host directly.
Answer B is incorrect. Dual-Homed Host Firewall Architecture can provide a very high level of control.
NEW QUESTION 2
You want to append a tar file if the on-disk version of the tar file has a modification date more recent than its copy in the tar archive. Which of the following commands will you use to accomplish the task?
- A. tar -u
- B. tar -t
- C. tar -c
- D. tar –x
Answer: A
Explanation:
The tar -u command is used to append a tar file if the on-disk version of the tar file has a modification date more recent than its copy in the tar archive. Answer B is incorrect. The tar -t command is used to list the contents of an archive. Answer D is incorrect. The tar -x command is used to extract the files from an archive. Answer C is incorrect. The tar -c command is used to create a new archive of specified files.
NEW QUESTION 3
Which of the following wireless security features provides the best wireless security mechanism?
- A. WEP
- B. WPA with 802.1X authentication
- C. WPA
- D. WPA with Pre Shared Key
Answer: B
Explanation:
WPA with 802.1X authentication provides best wireless security mechanism. 802.1X authentication, also known as WPA-Enterprise, is a security mechanism for wireless networks. 802.1X provides port-based authentication, which involves communications between a supplicant, authenticator, and authentication server. The supplicant is often software on a client device, the authenticator is a wired Ethernet switch or wireless access point, and an authentication server is generally a RADIUS database. The authenticator acts like a security guard to a protected network. The supplicant (client device) is not allowed access through the authenticator to the protected side of the network until the supplicant's identity is authorized. With 802.1X port-based authentication, the supplicant provides credentials, such as user name/password or digital certificate, to the authenticator, and the authenticator forwards the credentials to the authentication server for verification. If the credentials are valid, the supplicant (client device) is allowed to access resources located on the protected side of the network.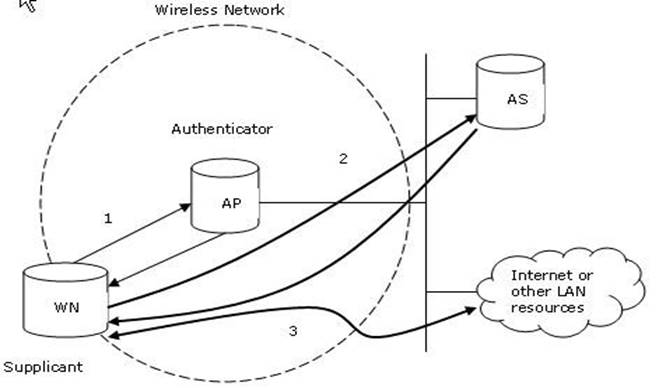
Answer A is incorrect. Wired equivalent privacy (WEP) uses the stream cipher RC4 (Rivest Cipher). WEP uses the Shared Key Authentication, since both the access point and the wireless device possess the same key. Attacker with enough Initialization Vectors can crack the key used and gain full access to the network. Answer D is incorrect. WPA-PSK is a strong encryption where encryption keys are automatically changed (called rekeying) and authenticated between devices after a fixed period of time, or after a fixed number of packets has been transmitted. Answer C is incorrect. WAP uses TKIP (Temporal Key Integrity Protocol) to enhance data encryption, but still vulnerable to different password
cracking attacks.
NEW QUESTION 4
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 Active Directory domain-based network. The domain contains one hundred Windows XP Professional client computers. Mark is deploying an 802.11 wireless LAN on the network. The wireless LAN will use Wired Equivalent Privacy (WEP) for all the connections. According to the company's security policy, the client computers must be able to automatically connect to the wireless LAN. However, the unauthorized computers must not be allowed to connect to the wireless LAN and view the wireless network. Mark wants to configure all the wireless access points and client computers to act in accordance with the company's security policy. What will he do to accomplish this? (Choose three)
- A. Configure the authentication type for the wireless LAN to Shared Key
- B. On each client computer, add the SSID for the wireless LAN as the preferred network
- C. Install a firewall software on each wireless access point
- D. Disable SSID Broadcast and enable MAC address filtering on all wireless access points
- E. Configure the authentication type for the wireless LAN to Open system
- F. Broadcast SSID to connect to the access point (AP)
Answer: ABD
Explanation:
To configure all the wireless access points and client computers to act in accordance with the company's security policy, Mark will take the following actions: Configure the authentication type for the wireless LAN to Shared Key. Shared Key authentication provides access control. Disable SSID Broadcast and enable MAC address filtering on all the wireless access points. Disabling SSID Broadcast and enabling MAC address filtering will prevent unauthorized wireless client computers from connecting to the access point (AP). Only the computers with particular MAC addresses will be able to connect to the wireless access points. On each client computer, add the SSID for the wireless LAN as the preferred network. Answer E is incorrect. Setting the authentication type for the wireless LAN to Open System will disable Wired Equivalent Privacy (WEP). This level of WEP will not provide security.
NEW QUESTION 5
John works as a Security Professional. He is assigned a project to test the security of www.we-are-secure.com. John wants to get the information of all network connections and listening ports in the numerical form. Which of the following commands will he use?
- A. netstat -e
- B. netstat –r
- C. netstat -s
- D. netstat –an
Answer: D
Explanation:
According to the scenario, John will use the netstat -an command to accomplish the task. The netstat -an command is used to get the information of all network connections and listening ports in the numerical form. The netstat command displays
protocol-related statistics and the state of current TCP/IP connections. It is used to get information about the open connections on a computer, incoming and outgoing data, as well as the ports of remote computers to which the computer is connected. The netstat command gets all this networking information by reading the kernel routing tables in the memory. Answer A is incorrect. The netstat -e command displays the Ethernet information. Answer B is incorrect. The netstat -r command displays the routing table information. Answer C is incorrect. The netstat -s command displays per-protocol statistics. By default, statistics are shown for TCP, UDP and IP.
NEW QUESTION 6
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the company for personal reasons. He wants to send out some secret information of the company. To do so, he takes an image file and simply uses a tool image hide and embeds the secret file within an image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using the image file to send the data, the mail server of his company is unable to filter this mail. Which of the following techniques is he performing to accomplish his task?
- A. Web ripping
- B. Steganography
- C. Email spoofing
- D. Social engineering
Answer: B
Explanation:
According to the scenario, John is performing the Steganography technique for sending malicious data. Steganography is an art and science of hiding information by embedding harmful messages within other seemingly harmless messages. It works by replacing bits of unused data, such as graphics, sound, text, and HTML, with bits of invisible information in regular computer files. This hidden information can be in the form of plain text, cipher text, or even in the form of images. Answer A is incorrect. Web ripping is
a technique in which the attacker copies the whole structure of a Web site to the local disk and obtains all files of the Web site. Web ripping helps an attacker to trace the loopholes of the Web site. Answer D is incorrect. Social engineering is the art of convincing people and making them disclose useful information such as account names and passwords. This information is further exploited by hackers to gain access to a user's computer or network. This method involves mental ability of the people to trick someone rather than their technical skills. A user should always distrust people who ask him for his account name or password, computer name, IP address, employee ID, or other information that can be misused. Answer C is incorrect. John is not performing email spoofing. In email spoofing, an attacker sends emails after writing another person's mailing address in the from field of the email id.
NEW QUESTION 7
You work as an Exchange Administrator for XYZ CORP. The network design of the company is given below: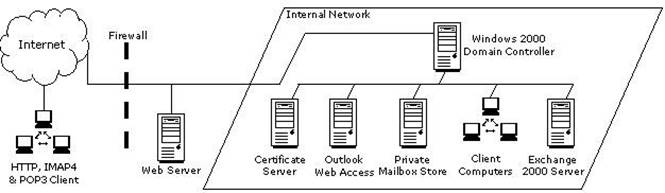
Employees are required to use Microsoft Outlook Web Access to access their emails remotely. You are required to accomplish the following goals: Ensure fault tolerance amongst the servers. Ensure the highest level of security and encryption for the Outlook Web Access clients. What will you do to accomplish these goals?
- A. Install one front-end Exchange 2000 server and continue to run Microsoft Outlook Web Access on the existing serve
- B. Place the new server on the perimeter networ
- C. Configure unique URLs for each serve
- D. Configure Certificate Service
- E. Create a rule on the firewall to direct port 443 to the servers.
- F. Install two front-end Exchange 2000 server
- G. Place the new servers on the internal network and configure load balancing between the
- H. Configure Certificate Service
- I. Create a rule on the firewall to redirect port 443 to the servers.
- J. Install two front-end Exchange 2000 server
- K. Place the new servers on the perimeter network and configure load balancing between the
- L. Configure Certificate Service
- M. Create a rule on the firewall to redirect port 443 to the servers.
- N. Install two Exchange 2000 server
- O. Place the new servers on the perimeter networ
- P. Configure unique URLs for each serve
- Q. Configure Certificate Service
- R. Create a rule on the firewall to direct port 443 to the servers.
Answer: C
Explanation:
To ensure fault tolerance among the servers and to get the highest possible level of security and encryption for OWA clients, you must install two front-end Exchange 2000 servers. Place the new servers on the perimeter network and configure load balancing between them. To enhance security, you should also configure Certificate Services and create a rule on the firewall to redirect port 443 to the servers. The most secure firewall configuration is placing a firewall on either side of the front-end servers. This isolates the front-end servers in a perimeter network, commonly referred to as a demilitarized zone (DMZ). It is always better to configure more than one front-end server to get fault tolerance.
NEW QUESTION 8
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to see the local device files or 'links to device files' for a non-standard device driver. Which of the following Unix configuration files should you use to accomplish the task?
- A. profile
- B. /etc/bootptab
- C. /dev/MAKEDEV
- D. /etc/aliases
Answer: C
Explanation:
In Unix, the /dev/MAKEDEV file is used by system administrators for local device files or links to device files for a non-standard device driver. Answer A is incorrect. In Unix, the profile file stores the system wide environment and startup script program. Answer D is incorrect. In Unix, the /etc/aliases file is where the user's name is matched to a nickname for e-mail. Answer B is incorrect. In Unix, the /etc/bootptab/ file contains the configuration for the BOOTP server daemon.
NEW QUESTION 9
Which of the following commands can you use to search a string 'pwd' in all text files without opening them? (Choose two)
- A. vi
- B. grep
- C. sed
- D. locate
Answer: BC
Explanation:
sed and grep are the two commands that can be used to search a specified string in all text files without opening them. sed is a stream editor that is used to perform basic text transformations on an input stream (a file or input from a pipeline).
NEW QUESTION 10
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He notices that UDP port 137 of the We-are- secure server is open. Assuming that the Network Administrator of We-are-secure Inc. has not changed the default port values of the services, which of the following services is running on UDP port 137?
- A. HTTP
- B. TELNET
- C. NetBIOS
- D. HTTPS
Answer: C
Explanation:
NetBIOS is a Microsoft service that enables applications on different computers to communicate within a LAN. NetBIOS systems identify themselves with a 15- character unique name and use Server Message Block, which allows Remote directory, file and printer sharing, etc. The default port value of NetBIOS Name Resolution Service is 137/UDP. Answer A is incorrect. Hypertext Transfer Protocol (HTTP) is a client/server TCP/IP protocol used on the World Wide Web (WWW) to display Hypertext Markup Language (HTML) pages. HTTP defines how messages are formatted and transmitted, and what actions Web servers and browsers should take in response to various commands. For example, when a client application or browser sends a request to the server using HTTP commands, the server responds with a message containing the protocol version, success or failure code, server information, and body content, depending on the request. HTTP uses TCP port 80 as the default port. Answer D is incorrect. The default port of HTTPS is TCP/443. Hypertext Transfer Protocol Secure (HTTPS) protocol is a protocol used in the Universal Resource Locater (URL) address line to connect to a secure site. If a site has been made secure by using the Secure Sockets Layer (SSL) then HTTPS, instead of HTTP protocol, should be used as a protocol type in the URL. Answer B is incorrect. TELNET is a command-line connectivity tool that starts terminal emulation with a remote host running the telnet server service. TELNET allows users to communicate with a remote computer, offers the ability to run programs remotely, and facilitates remote administration. The TELNET utility uses the Telnet protocol for connecting to a remote computer running the Telnet server software, to access files. It uses TCP port 23 by default.
NEW QUESTION 11
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He is configuring the Apache Web server settings. He does not want the commands being used in the settings to be stored in the history. Which of the following commands can he use to disable history?
- A. history !!
- B. set +o history
- C. history !N
- D. set -o history
Answer: B
Explanation:
According to the scenario, John can use the set +o history command to disable history. Answer D is incorrect. John cannot use the set -o history command to accomplish his task. This command is used to enable disabled history.
Answer A is incorrect. John cannot use the history !! command to accomplish his task. This command is used to see the most recently typed command. Answer C is incorrect. John cannot use the history !N command to accomplish his task. This command is used to display the Nth history command.
NEW QUESTION 12
Which of the following responsibilities does not come under the audit process?
- A. Reporting all facts and circumstances of the irregular and illegal acts.
- B. Planning the IT audit engagement based on the assessed level of risk.
- C. Reviewing the results of the audit procedures.
- D. Applying security policies.
Answer: ABC
Explanation:
According to the standards of ISACA, an auditor should hold the following responsibilities: Planning the IT audit engagement based on an assessed level of risk. Designing audit procedures of irregular and illegal acts. Reviewing the results of the audit procedures. Assuming that acts are not isolated. Determining why the internal control system failed for that act. Conducting additional audit procedures. Evaluating the results of the expanded audit procedures. Reporting all facts and circumstances of the irregular and illegal acts. Distributing the report to the appropriate internal parties, such as managers. Answer D is incorrect. The auditor is not responsible for applying security policies.
NEW QUESTION 13
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 Active Directory domain-based network. The domain consists of a domain controller, two Windows 2003 member servers, and one hundred client computers. The company employees use laptops with Windows XP Professional. These laptops are equipped with wireless network cards that are used to connect to access points located in the Marketing department of the company. The company employees log on to the domain by using a user name and password combination. The wireless network has been configured with WEP in
addition to 802.1x. Mark wants to provide the best level of security for the kind of authentication used by the company. What will Mark do to accomplish the task?
- A. Use IPSec
- B. Use MD5
- C. Use PEAP
- D. Use EAP-TLS
Answer: C
Explanation:
In order to provide the best level of security for the kind of authentication used by the company, Mark will have to use the PEAP protocol. This protocol will provide the strongest password-based authentication for a WEP solution with 802.1x. Implementing 802.1x authentication for wireless security requires using an Extensible Authentication Protocol (EAP)-based method for authentication. There are two EAP-based methods: 1.EAP-Transport Layer Security (EAP-TLS) 2.Protected EAP (PEAP) Answer A is incorrect. IPSec has nothing to do with this issue.
NEW QUESTION 14
You are the Network Admin for a company. You are concerned about users having access to items they should not. Your concern is that they may inadvertently have been granted access to those resources. When conducting a user access and rights review, which of the following is most likely to show you such unintentional granting of user rights?
- A. IDS Logs
- B. Access Control Lists
- C. Server logs
- D. Group Membership
Answer: D
Explanation:
Most often user rights are determined by the groups the user belongs to. In some cases a user may mistakenly be added to a group they should not be. It is also common that a user moves within the organization, but is still retained in their previous group giving them those rights. Answer B is incorrect. Access Control Lists are usually setup up manually. This means that a person would not likely be inadvertently added. You might want to check the ACL's, and you might find some issues, but this is not the most likely way to find users with inappropriate rights. Answer C is incorrect. At best server logs can show you if a user accessed a resource. But a user could have access to a resource, and simply not have used that access yet. Answer A is incorrect. IDS logs will only help you identify potential attacks. Unless you suspect the user of intentionally trying to break into resources, an IDS log will not help in this scenario.
NEW QUESTION 15
The SALES folder has a file named XFILE.DOC that contains critical information about your company. This folder resides on an NTFS volume. The company's Senior Sales Manager asks you to provide security for that file. You make a backup of that file and keep it in a locked cupboard, and then you deny access on the file for the Sales group. John, a member of the Sales group, accidentally deletes that file. You have verified that John is not a member of any other group. Although you restore the file from backup, you are confused how John was able to delete the file despite having no access to that file. What is the most likely cause?
- A. The Sales group has the Full Control permission on the SALES folder.
- B. The Deny Access permission does not restrict the deletion of files.
- C. John is a member of another group having the Full Control permission on that file.
- D. The Deny Access permission does not work on files.
Answer: A
Explanation:
Although NTFS provides access controls to individual files and folders, users can perform certain actions even if permissions are set on a file or folder to prevent access. If a user has been denied access to any file and he has Full Control rights in the folder on which it resides, he will be able to delete the file, as Full Control rights in the folder allow the user to delete the contents of the folder. Answer C is incorrect. In the event of any permission conflict, the most restrictive one prevails. Moreover, the question clearly states that John is not a member of any other group. Answer B, D are incorrect. The Deny Access permission works on files.
NEW QUESTION 16
Which of the following applications work as mass-emailing worms? (Choose two)
- A. Chernobyl virus
- B. I LOVE YOU virus
- C. Nimda virus
- D. Melissa virus
Answer: BC
Explanation:
The Nimda and I LOVE YOU viruses work as mass-emailing worms.
NEW QUESTION 17
You work as a Software Developer for UcTech Inc. You want to ensure that a class is informed whenever an attribute is added, removed, or replaced in a session. Which of the following is the event that you will use to accomplish the task?
- A. HttpSessionBindingEvent
- B. HttpAttributeEvent
- C. HttpSessionEvent
- D. HttpSessionAttributeEvent
Answer: A
Explanation:
To be informed whenever an attribute is added, removed, or replaced in a session, a class must have a method with HttpSessionBindingEvent as its attribute. The HttpSessionBindingEvent class extends the HttpSessionEvent class. The HttpSessionBindingEvent class is used with the following listeners: HttpSessionBindingListener: It notifies the attribute when it is bound or unbound from a session. HttpSessionAttributeListener: It notifies the class when an attribute is bound, unbound, or replaced in a session. The session binds the object by a call to the HttpSession.setAttribute() method and unbinds the object by a call to the HttpSession.removeAttribute() method. Answer C is incorrect. The HttpSessionEvent is associated with the HttpSessionListener interface and HttpSessionActivationListener.
NEW QUESTION 18
......
100% Valid and Newest Version GSNA Questions & Answers shared by Surepassexam, Get Full Dumps HERE: https://www.surepassexam.com/GSNA-exam-dumps.html (New 368 Q&As)
- Update GCIA Free Exam For GIAC Certified Intrusion Analyst Certification
- The Secret Of GIAC GISF Dump
- How Many Questions Of GSNA Braindumps
- What Exact GCIA Testing Bible Is
- How Many Questions Of GISF Training Materials
- All About Actual GSNA Study Guides
- Top Tips Of Rebirth GSNA Exam Question
- Highest Quality GIAC GCIH Dump Online
- Rebirth GIAC Certified Intrusion Analyst GCIA Free Practice Questions
- Leading GIAC Systems And Network Auditor GSNA Braindumps

