JN0-230 Exam Questions - Online Test
JN0-230 Premium VCE File

150 Lectures, 20 Hours

Exam Code: JN0-230 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Security - Associate (JNCIA-SEC)
Certification Provider: Juniper
Free Today! Guaranteed Training- Pass JN0-230 Exam.
Juniper JN0-230 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
You want to generate reports from the l-Web on an SRX Series device. Which logging mode would you use in this scenario?
- A. Syslog
- B. Stream
- C. Event
- D. local
Answer: B
NEW QUESTION 2
You want to integrate an SRX Series device with SKY ATP. What is the first action to accomplish task?
- A. Issue the commit script to register the SRX Series device.
- B. Copy the operational script from the Sky ATP Web UI.
- C. Create an account with the Sky ATP Web UI.
- D. Create the SSL VPN tunnel between the SRX Series device and Sky ATP.
Answer: C
NEW QUESTION 3
Which three actions would be performed on traffic traversing an IPsec VPAN? (Choose three.)
- A. Port forwarding
- B. Authentication
- C. Encryption
- D. Deep inspection
- E. Payload verification
Answer: BCE
NEW QUESTION 4
What is the purpose of the Shadow Policies workspace in J-Web?
- A. The Shadow Policies workspace shows unused security policies due to policy overlap.
- B. The Shadow Policies workspace shows unused IPS policies due to policy overlap.
- C. The Shadow Policies workspace shows used security policies due to policy overlap
- D. The Shadow Policies workspace shows used IPS policies due to policy overlap
Answer: A
NEW QUESTION 5
On an SRX device, you want to regulate traffic base on network segments. In this scenario, what do you configure to accomplish this task?
- A. Screens
- B. Zones
- C. ALGs
- D. NAT
Answer: B
NEW QUESTION 6
Which two segments describes IPsec VPNs? (Choose two.)
- A. IPsec VPN traffic is always authenticated.
- B. IPsec VPN traffic is always encrypted.
- C. IPsec VPNs use security to secure traffic over a public network between two remote sites.
- D. IPsec VPNs are dedicated physical connections between two private networks.
Answer: AC
NEW QUESTION 7
Which two statements are true about security policy actions? (Choose two.)
- A. The reject action drops the traffic and sends a message to the source device.
- B. The deny action silently drop the traffic.
- C. The deny action drops the traffic and sends a message to the source device.
- D. The reject action silently drops the traffic.
Answer: AB
NEW QUESTION 8
What are configuring the antispam UTM feature on an SRX Series device.
Which two actions would be performed by the SRX Series device for e-mail that is identified as spam? (Choose two.)
- A. Tag the e-mail
- B. Queue the e-mail
- C. Block the e-mail
- D. Quarantine e-mail
Answer: AC
NEW QUESTION 9
You configure and applied several global policies and some of the policies have overlapping match criteria.
- A. In this scenario, how are these global policies applies?
- B. The first matched policy is the only policy applied.
- C. The most restrictive that matches is applied.
- D. The least restrictive policy that matches is applied.
Answer: A
NEW QUESTION 10
Which statements is correct about global security policies?
- A. Global policies allow you to regulate traffic with addresses and applications, regardless of their security zones.
- B. Traffic matching global is not added to the session table.
- C. Global policies eliminate the need to assign interface to security zones.
- D. Global security require you to identify a source and destination zone.
Answer: A
NEW QUESTION 11
You verify that the SSH service is configured correctly on your SRX Series device, yet administrators attempting to connect through a revenue port are not able to connect.
In this scenario, what must be configured to solve this problem?
- A. A security policy allowing SSH traffic.
- B. A host-inbound-traffic setting on the incoming zone
- C. An MTU value target than the default value
- D. A screen on the internal interface
Answer: B
NEW QUESTION 12
Which flow module components handles processing for UTM?
- A. Policy
- B. Zones
- C. Services
- D. Screen options
Answer: C
NEW QUESTION 13
Which two actions are performed on an incoming packet matching an existing session? (Choose two.)
- A. Zone processing
- B. Security policy evolution
- C. Service ALG processing
- D. Screens processing
Answer: CD
NEW QUESTION 14
Host-inbound-traffic is configured on the DMZ zone and the ge-0/0/9.0 interface attached to that zone. Referring to the exhibit,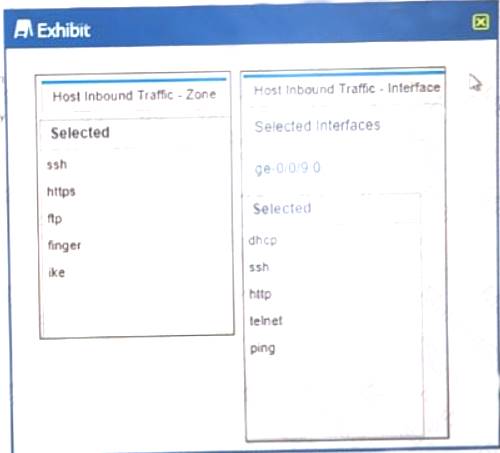
which to types of management traffic would be performed on the SRX Series device? (Choose two.)
- A. HTTPS
- B. SSH
- C. Finger
- D. HTTP
Answer: BD
NEW QUESTION 15
A new SRX Series device has been delivered to your location. The device has the factory-default configuration loaded. You have powered on the device and connected to the console port.
What would you use to log into the device to begin the initial configuration?
- A. Root with a password of juniper’’
- B. Root with no password
- C. Admin with password
- D. Admin with a password ‘’juniper’’
Answer: B
NEW QUESTION 16
Users in your network are downloading files with file extensions that you consider to be unsafe for your network. You must prevent files with specific file extensions from entering your network.
Which UTM feature should be enable on an SRX Series device to accomplish this task?
- A. Content filtering
- B. Web filtering
- C. Antispam
- D. URL filtering
Answer: A
NEW QUESTION 17
Which actions would be applied for the pre-ID default policy unified policies?
- A. Redirect the session
- B. Reject the session
- C. Log the session
- D. Silently drop the session
Answer: C
NEW QUESTION 18
You are designing a new security policy on an SRX Series device. You must block an application and log all occurrence of the application access attempts.
In this scenario, which two actions must be enabled in the security policy? (Choose two.)
- A. Log the session initiations
- B. Enable a reject action
- C. Log the session closures
- D. Enable a deny action
Answer: AD
NEW QUESTION 19
Referring to the exhibit.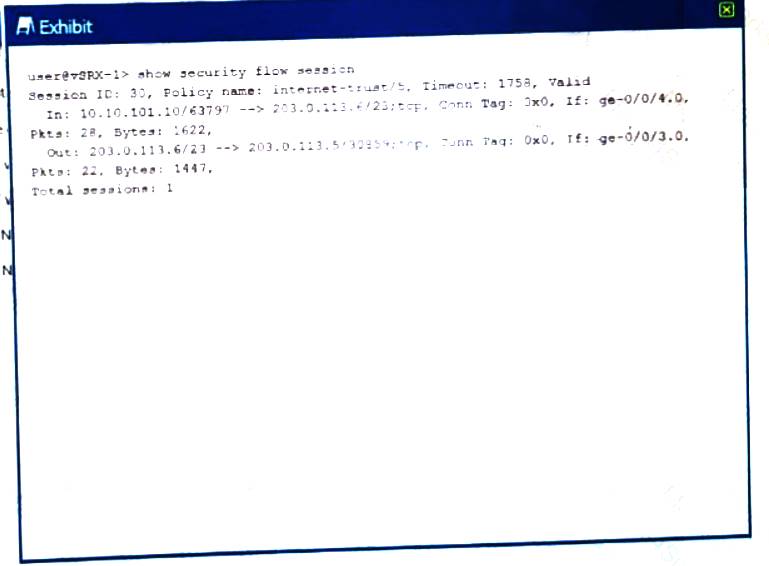
Which type of NAT is being performed?
- A. Source NAT with PAT
- B. Source NAT without PAT
- C. Destination NAT without PAT
- D. Destination NAT with PAT
Answer: A
NEW QUESTION 20
Which method do VPNs use to prevent outside parties from viewing packet in clear text?
- A. Integrity
- B. Authentication
- C. Encryption
- D. NAT_T
Answer: C
NEW QUESTION 21
Which two match conditions would be used in both static NAT and destination NAT rule sets? (Choose two.)
- A. Destination zone
- B. Destination interface
- C. Source interface
- D. Source zone
Answer: BD
NEW QUESTION 22
You have configured antispam to allow e-mail from example.com, however the logs you see thatjcart@example.comis blocked
Referring to the exhibit.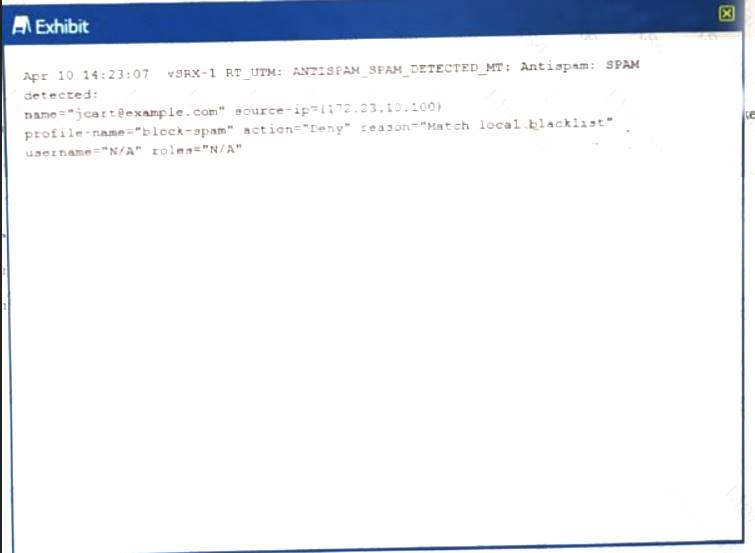
What are two ways to solve this problem?
- A. Verify connectivity with the SBL server.
- B. Addjcart@exmple.comto the profile antispam address whitelist.
- C. Deletejcart@example.comfrom the profile antispam address blacklist
- D. Deletejcart@example.comfrom the profile antispam address whitelist
Answer: BC
NEW QUESTION 23
Which two statements are true about UTM on an SRX340? (Choose two.)
- A. A default UTM policy is created.
- B. No default profile is created.
- C. No default UTM policy is created
- D. A default UTM profile is created
Answer: BC
NEW QUESTION 24
......
P.S. Easily pass JN0-230 Exam with 65 Q&As Exambible Dumps & pdf Version, Welcome to Download the Newest Exambible JN0-230 Dumps: https://www.exambible.com/JN0-230-exam/ (65 New Questions)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (61-70)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (161-170)
- Latest Jn0-333 Dumps 2021
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (71-80)
- How Many Questions Of JN0-104 Pdf
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (91-100)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (1-10)
- Top Tips Of Up To The Immediate Present JN0-104 Sample Question
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (11-20)
- What Download JN0-104 Exam Question Is

