jn0-333 Exam Questions - Online Test
jn0-333 Premium VCE File

150 Lectures, 20 Hours

Cause all that matters here is passing the Juniper jn0-333 exam. Cause all that you need is a high score of jn0-333 Security, Specialist (JNCIS-SEC) exam. The only one thing you need to do is downloading Exambible jn0-333 exam study guides now. We will not let you down with our money-back guarantee.
Free jn0-333 Demo Online For Juniper Certifitcation:
NEW QUESTION 1
Your internal webserver uses port 8088 for inbound connections. You want to allow external HTTP traffic to connect to the webserver.
Which two actions would accomplish this task? (Choose two.)
- A. Create a custom application for port 8088 and create a security policy that permits the custom-http application.
- B. Remap port 80 to port 8088 in the junos-http application and create a security policy that permits the junos-http application.
- C. Use destination NAT to remap incoming traffic from port 80 to port 8088.
- D. Create an Application Layer Gateway to permit HTTP traffic on port 8088.
Answer: AC
NEW QUESTION 2
Which type of VPN provides a secure method of transporting encrypted IP traffic?
- A. IPsec
- B. Layer 3 VPN
- C. VPLS
- D. Layer 2 VPN
Answer: A
NEW QUESTION 3
You need to configure an IPsec tunnel between a remote site and a hub site. The SRX Series device at the remote site receives a dynamic IP address on the external interface that you will use for IPsec.
Which feature would you need to configure in this scenario?
- A. NAT-T
- B. crypto suite B
- C. aggressive mode
- D. IKEv2
Answer: C
NEW QUESTION 4
In a chassis cluster, which two characteristics are true regarding reth interfaces? (Choose two.)
- A. A reth interface inherits its failover properties from a redundancy group.
- B. Reth interfaces must be the same type of interface.
- C. Reth interfaces must be in the same slots on each node.
- D. A reth interface goes down if one of its child interfaces become unavailable.
Answer: AB
NEW QUESTION 5
You must verify if destination NAT is actively being used by users connecting to an internal server from the Internet.
Which action will accomplish this task on an SRX Series device?
- A. Examine the destination NAT translations table.
- B. Examine the installed routes in the packet forwarding engine.
- C. Examine the NAT translation table.
- D. Examine the active security flow sessions.
Answer: A
NEW QUESTION 6
What are three characteristics of session-based forwarding, compared to packet-based forwarding, on an SRX Series device? (Choose three.)
- A. Session-based forwarding uses stateful packet processing.
- B. Session-based forwarding requires less memory.
- C. Session-based forwarding performs faster processing of existing session.
- D. Session-based forwarding uses stateless packet processing,
- E. Session-based forwarding uses six tuples of information.
Answer: ACE
NEW QUESTION 7
Click the exhibit button.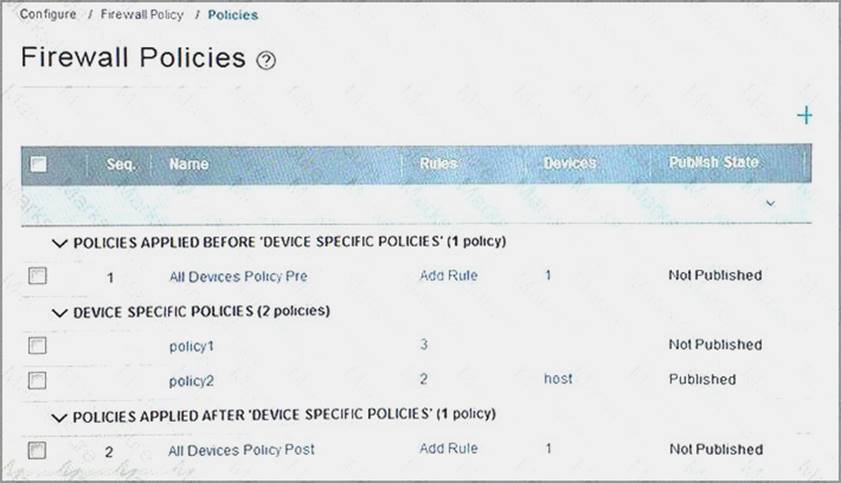
You are configuring security policies with Junos Space Security Director. Referring to the exhibit, which two statements are true? (Choose two.)
- A. The host device has three rules assigned to it.
- B. The policy assigned to the host device is published.
- C. The policy assigned to the host device requires publishing.
- D. The host device has two rules assigned to it.
Answer: BD
NEW QUESTION 8
Which two statements are true about global security policies? (Choose two.)
- A. Global security policies are evaluated before regular security policies.
- B. Global security policies can be configured to match addresses across multiple zones.
- C. Global security policies can match traffic regardless of security zones.
- D. Global security policies do not support IPv6 traffic.
Answer: BC
NEW QUESTION 9
Which three statements describes traditional firewalls? (Choose three.)
- A. A traditional firewall performs stateless packet processing.
- B. A traditional firewall offers encapsulation, authentication, and encryption.
- C. A traditional firewall performs stateful packet processing.
- D. A traditional firewall forwards all traffic by default.
- E. A traditional firewall performs NAT and PAT.
Answer: BCE
NEW QUESTION 10
You want to implement IPsec on your SRX Series devices, but you do not want to use a preshared key. Which IPsec implementation should you use?
- A. public key infrastructure
- B. next-hop tunnel binding
- C. tunnel mode
- D. aggressive mode
Answer: A
NEW QUESTION 11
Which two statements about security policy actions are true? (Choose two.)
- A. The log action implies an accept action.
- B. The log action requires an additional terminating action.
- C. The count action implies an accept action.
- D. The count action requires an additional terminating action.
Answer: BD
NEW QUESTION 12
Click the Exhibit button.
You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172.25.11.0/24 subnet to the Internet. You create a policy named permit – http between the trust and untrust zones that permits HTTP traffic.
When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)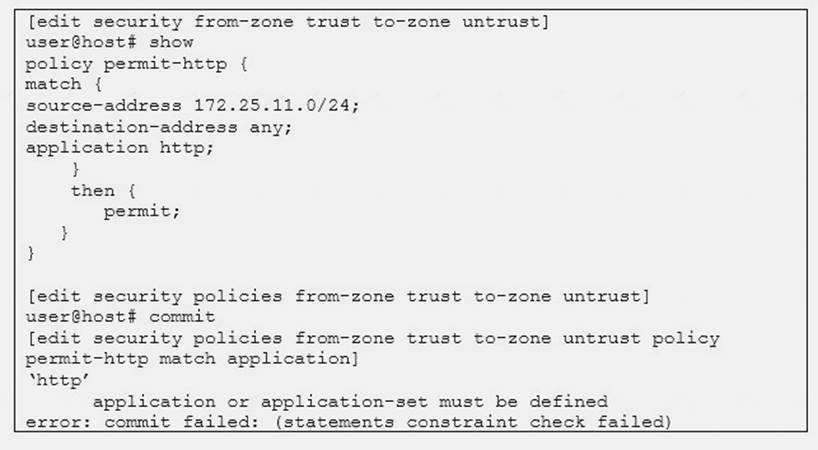
- A. Create a custom application named http at the [edit applications] hierarchy.
- B. Execute the Junos commit full command to override the error and apply the configuration.
- C. Modify the security policy to use the built-in junos-http application.
- D. Issue the rollback 1 command from the top of the configuration hierarchy and attempt the commit again.
Answer: BC
NEW QUESTION 13
Click the Exhibit button.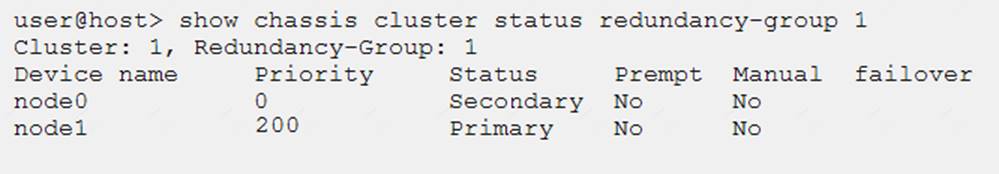
Which two statements describe the output shown in the exhibit? (Choose two.)
- A. Node 0 is controlling traffic for redundancy group 1.
- B. Node 1 is controlling traffic for redundancy group 1.
- C. Redundancy group 1 experienced an operational failure.
- D. Redundancy group 1 was administratively failed over.
Answer: BD
NEW QUESTION 14
What are two supported hypervisors for hosting a vSRX? (Choose two.)
- A. VMware ESXi
- B. Solaris Zones
- C. KVM
- D. Docker
Answer: AC
NEW QUESTION 15
Which UDP port is used in Ipsec tunneling when NAT-T is in use?
- A. 50
- B. 4500
- C. 500
- D. 51
Answer: B
NEW QUESTION 16
Click the Exhibit button.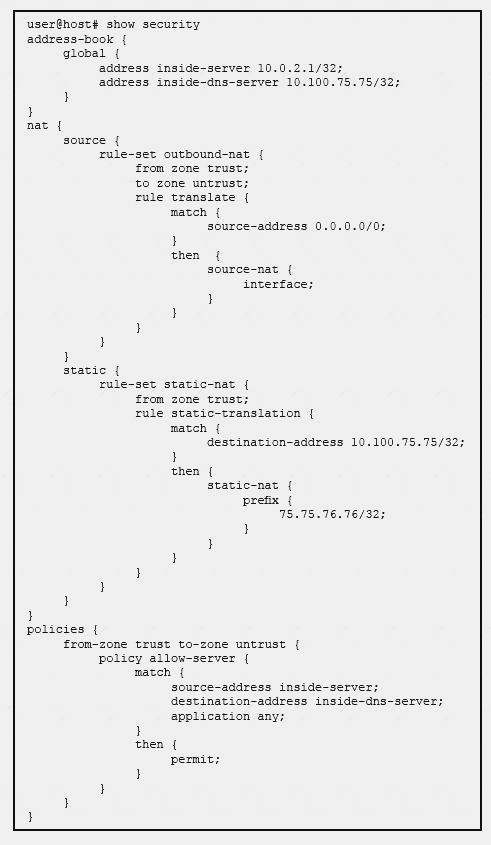
The inside server must communicate with the external DNS server. The internal DNS server address is 10.100.75.75. The external DNS server address is 75.75.76.76. Traffic from the inside server to the DNS server fails.
Referring to the exhibit, what is causing the problem?
- A. The security policy must match the translated destination address.
- B. Source and static NAT cannot be configured at the same time.
- C. The static NAT rule must use the global address book entry name for the DNS server.
- D. The security policy must match the translated source and translated destination address.
Answer: A
NEW QUESTION 17
What are the maximum number of redundancy groups that would be used on a chassis cluster?
- A. The maximum number of redundancy groups use is equal to the number of configured physical interfaces.
- B. The maximum number of redundancy groups use is equal to one more than the number of configured physical interfaces.
- C. The maximum number of redundancy groups use is equal to the number of configured logical interfaces.
- D. The maximum number of redundancy groups use is equal to one more than the number of configured logical interfaces.
Answer: C
NEW QUESTION 18
What is the correct ordering of Junos policy evaluation from first to last?
- A. global policy > zone-based policy > default policy
- B. default policy > zone-based policy > global policy
- C. global policy > default policy > zone-based policy
- D. zone-based policy > global policy > default policy
Answer: D
NEW QUESTION 19
Which process describes the implementation of screen options on an SRX Series device?
- A. Configured screen options are only applied when traffic does not match a valid route.
- B. Configured screen options are applied only to the first packet that is processed in a stateful session.
- C. Configured screen options are applied to all packets that are processed by the stateful session firewall processor.
- D. Configured screen options are only applied when traffic does not match a valid policy.
Answer: C
NEW QUESTION 20
Click to the Exhibit button.
Referring to the exhibit, which two statements are true? (Choose two.)
- A. Interface ge-0/0/0 will not accept SSH connections.
- B. Interfaces ge-0/0/0.0 and ge-0/0/1.0 will allow SSH connections.
- C. Interface ge-0/0/0.0 will respond to pings.
- D. Interface ge-0/0/1.0 will respond to pings.
Answer: BD
NEW QUESTION 21
Which interface is used exclusively to forward Ethernet-switching traffic between two chassis cluster nodes?
- A. swfab0
- B. fxp0
- C. fab0
- D. me0
Answer: A
NEW QUESTION 22
......
Recommend!! Get the Full jn0-333 dumps in VCE and PDF From Certifytools, Welcome to Download: https://www.certifytools.com/jn0-333-exam.html (New 75 Q&As Version)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (161-170)
- Top Tips Of Up To The Immediate Present JN0-104 Sample Question
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (31-40)
- Top Tips Of Replace JN0-682 Study Guides
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (131-140)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (101-110)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (11-20)
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (6-15)
- Most Recent Junos - Associate (JNCIA-Junos) JN0-104 Testing Material
- [2021-New] Juniper JN0-102 Dumps With Update Exam Questions (81-90)

