642-889 Exam Questions - Online Test
642-889 Premium VCE File

150 Lectures, 20 Hours

Your success in is our sole target and we develop all our in a way that facilitates the attainment of this target. Not only is our material the best you can find, it is also the most detailed and the most updated. for Cisco 642-889 are written to the highest standards of technical accuracy.
Online 642-889 free questions and answers of New Version:
NEW QUESTION 1
In Layer 3 MPLS VPN implementations, if some of the VPNv4 routes on one PE router do not appear on another PE router, what could be the problem?
- A. RD mismatch between the PE routers
- B. RT export and import configuration errors
- C. RD export and import configuration errors
- D. VRF name mismatch between the PE routers
Answer: B
Explanation: http://blog.initialdraft.com/archives/1537/
NEW QUESTION 2
Which MP-BGP address family must be configured to use VPLS autodiscovery in a Cisco IOS XR router?
- A. address-family l2vpn vpls-vpws
- B. address-family vpnv4 unicast
- C. address-family ipv4 mdt
- D. address-family ipv4 tunnel
- E. address-family vpls vfi
Answer: A
Explanation: http://www.cisco.com/en/US/docs/ios/12_2sr/12_2srb/feature/guide/srbgpl2v.html
NEW QUESTION 3
Which Layer 2 VPN technology is implemented over an IP core network without the need for MPLS?
- A. VPLS
- B. VPWS
- C. AToM
- D. L2TPv3
Answer: D
Explanation: http://www.cisco.com/en/US/docs/ios/12_3t/12_3t2/feature/guide/gtl2tpv3.html#wp1040784
The Layer 2 Tunnel Protocol Version 3 feature expands on Cisco support of the Layer 2 Tunnel Protocol Version 3 {L2TPv3}. L2TPv3 is an Internet Engineering Task Force {IETF} l2tpext working group draft that provides several enhancements to L2TP for the capability to tunnel any Layer 2 payload over L2TP.
Specifically, L2TPv3 defines the L2TP protocol for tunneling Layer 2 payloads over an IP core network using Layer 2 virtual private networks {VPNs}. Benefits of this feature include the following:
•L2TPv3 simplifies deployment of VPNs
•L2TPv3 does not require Multiprotocol Label Switching
•L2TPv3 supports Layer 2 tunneling over IP for any payload
NEW QUESTION 4
DRAG DROP
Answer:
Explanation: Benefits of IEEE 802.1ah standard
The benefits of IEEE 802.1ah provider backbone bridges are as follows:
• Increased service instance scalability
• MAC address scalability
IEEE 802.1ah Standard for Provider Backbone Bridging Overview
The IEEE 802.1ah Provider Backbone Bridge feature encapsulates or decapsulates end user traffic on a Backbone Edge Bridge {BEB} at the edge of the Provider Backbone Bridged Network {PBBN}. A Backbone Core Bridge {BCB} based network provides internal transport of the IEEE 802.1ah encapsulated frames within the PBBN.
Overview of OAM The advent of Ethernet as a metropolitan and wide-area networking technology has accelerated the need for a new set of OAM protocols. Service provider networks are large and complex with a wide user base, and they often involve different operators that must work together to provide end-to-end services to enterprise customers. While enterprise end-customer demands continue to increase, so do the requirements for service provider Ethernet networks, particularly in the areas of availability and mean time to repair {MTTR}. Ethernet OAM addresses these challenges and more, thereby directly impacting the competitiveness of the service provider. Ethernet has been used as a LAN technology for many years, and enterprises have managed these networks effectively, primarily with the use of Internet protocols such as Simple Network Management Protocol {SNMP}, ICMP Echo {or IP Ping}, IP Traceroute, and Cisco Unidirectional Link Detection Protocol {UDLD} and Layer 2 Traceroute
{supported in Cisco Catalyst® OS and some Cisco IOS® Software-based platforms}. In addition to these troubleshooting protocols, Cisco provides a wealth of other configuration, fault, network management, and performance management tools. Cisco also supports MPLS OAM capabilities such as Virtual Circuit Connectivity Verification {VCCV} and Label Switched Path {LSP} ping on the Carrier Ethernet platforms. To complement these OAM capabilities and to ensure that Ethernet can deliver the required customer service-level agreements {SLAs}, Cisco has developed comprehensive Ethernet and IP SLA agents, along with an embedded event manager {EEM}, and IPTV video quality tools for automated measurement and troubleshooting of Carrier Ethernet deployments.
Ethernet OAM addresses the following challenges:
• The existing protocols mentioned earlier will not work unless the Ethernet layer is operating properly, making Ethernet OAM a prerequisite.
• Many service providers do not want to overlay an IP infrastructure simply for management and troubleshooting of Layer 2 Ethernet services.
• The current management protocols lack the per-customer or per-service granularity that is required to manage the individual Layer 2 Ethernet services provided to enterprises.
• The existing protocols do not assist with provisioning of Ethernet services, which is particularly difficult when the service provider and end customer must coordinate the configurations on their respective Ethernet equipment. Ethernet OAM is a broad topic, but this paper will focus on three main areas of Ethernet OAM that are most in need by service providers and are rapidly evolving in the standards bodies: Service Layer OAM {IEEE 802.1ag Connectivity Fault Management}, Link Layer OAM {IEEE 802.3ah OAM}, and Ethernet Local Management
Interface {MEF-16 E-LMI}. Each of these different OAM protocols has unique objectives and is complementary to the others IEEE 802.1ad[note 1] is an Ethernet networking standard informally known as IEEE 802.1QinQ and is an amendment to IEEE standard IEEE 802.1Q-1998. The technique is also known as provider bridging, Stacked VLANs or simply QinQ or Q-in-Q.
The original 802.1Q specification allows a single VLAN header to be inserted into an Ethernet frame. QinQ allows multiple VLAN headers to be inserted into a single frame, an essential capability for implementing Metro Ethernet network topologies. Just as QinQ extends 802.1Q, QinQ itself is extended by other Metro Ethernet protocols.[specify] In a multiple VLAN header context, out of convenience the term "VLAN tag" or just "tag" for short is often used in place of "802.1Q VLAN header". QinQ allows multiple VLAN tags in an Ethernet frame; together these tags constitute
a tag stack. When used in the context of an Ethernet frame, a QinQ frame is a frame that has 2 VLAN 802.1Q headers {double-tagged}.
There is a mild confusion regarding the naming because the 802.1ad standard was grown out of the 802.1QinQ protocol {which was developed based the trademarked method 802.1Q, with capital "Q" as a distinction instead of the 802.1q as the standardised protocol} which originally used 0x9100 as ethernet type instead of 0x88a8. While the network industry usually mix the naming the proper, standardised name is 802.1ad which sometimes gets appended by the other alternative names mentioned above; the plain "802.1QinQ" name usually refers to the old standard which is now considered obsolete
NEW QUESTION 5
A routing entry on a PE router has an ext-hop address of ::ffff:[IP ADDRESS]. Which service provider technology is being deployed?
- A. 6VPE
- B. 6PE
- C. 4to6 tunnel
- D. 6to4 tunnel
Answer: B
NEW QUESTION 6
Which three possible misconfigurations can occur on the backbone IGP section of an MPLS Layer 3 VPN setup? {Choose three.}
- A. configuring the LDP router ID with an incorrect loopback interface
- B. configuring the wrong AS number on a client eBGP peering
- C. configuring the wrong area number on a PE-CE OSPF link
- D. decreasing the MPLS MTU
- E. disabling MPLS on a core link
- F. disabling MPLS LDP sync in the IGP routing process
Answer: ADE
NEW QUESTION 7
In MPLS Layer 3 VPN implementations, what is used at the PEs to transform the customer IPv4 prefixes into a unique 96-bit prefix?
- A. RT
- B. RD
- C. VC ID
- D. PW ID
- E. AS number
Answer: B
NEW QUESTION 8
What is the primary difference between 6PE and 6VPE?
- A. 6VPE does not require an MPLS core.
- B. 6VPE requires an IPv6-aware core.
- C. 6VPE provides IPv6 VPN services.
- D. 6VPE tunnels IPv6 packets inside IPv4 packets.
Answer: C
Explanation: 6PE is for transporting ipv6 natively and 6VPE is for ipv6 mpls vpns
NEW QUESTION 9
Which three Layer 3 VPN technologies are based on the overlay model? {Choose three.}
- A. ATM virtual circuits
- B. Frame Relay virtual circuits
- C. GRE/IPsec
- D. L2TPv3
- E. MPLS Layer 3 VPNs
- F. DMVPNs
Answer: CDF
Explanation: The overlay model, where the service provider provides emulated leased lines to the customer.
The service provider provides the customer with a set of emulated leased lines. These leased lines are called VCs, which can be either constantly available {PVCs} or established on demand {SVCs}. The QoS guarantees in the overlay VPN model usually are expressed in terms of bandwidth guaranteed on a certain VC {Committed Information Rate or CIR} and maximum bandwidth available on a certain VC {Peak Information Rate or PIR}. The committed bandwidth guarantee usually is provided through the statistical nature of the Layer 2 service but depends on the overbooking strategy of the service provider The peer-to-peer model, where the service provider and the customer exchange Layer 3 routing information and the provider relays the data between the customer sites on the optimum path between the sites and without the customer's involvement.
The peer-to-peer VPN model was introduced a few years ago to alleviate the drawbacks of the overlay VPN model. In the peer-to-peer model, the Provider Edge {PE} device is a router {PE-router} that directly exchanges routing information with the CPE router. The Managed Network service offered by many service providers, where the service provider also manages the CPE devices, is not relevant to this discussion because it's only a repackaging of another service. The Managed Network provider concurrently assumes the role of the VPN service provider providing the VPN infrastructure} and part of the VPN customer role {managing the CPE device}.
The peer-to-peer model provides a number of advantages over the traditional overlay model:
Routing {from the customer's perspective} becomes exceedingly simple, as the customer router exchanges routing information with only one {or a few} PE-router, whereas in the overlay VPN network, the number of neighbor routers can grow to a large number.
Routing between the customer sites is always optimal, as the provider routers know the customer's network topology and can thus establish optimum inter-site routing.
Bandwidth provisioning is simpler because the customer has to specify only the inbound and outbound bandwidths for each site {Committed Access Rate [CAR] and Committed Delivery Rate [CDR]} and not the exact site-to-site traffic profile.
The addition of a new site is simpler because the service provider provisions only an additional site and changes the configuration on the attached PE-router. Under the overlay VPN model, the service provider must provision a whole set of VCs leading from that site to other sites of the customer VPN.
Prior to an MPLS-based VPN implementation, two implementation options existed for the peer-to-peer VPN model: The shared-router approach, where several VPN customers share the same PE-router.
The dedicated-router approach, where each VPN customer has dedicated PE-routers.
NEW QUESTION 10
Refer to the exhibit.
What is the AS-PATH list for an e-BGP update sent from ABC site 1 to ABC site 2 on the CE2 BGP table?
- A. 300 300
- B. 300 6500
- C. 6500 300
- D. 6500 6500
- E. 6500 6500 200
Answer: D
NEW QUESTION 11
Which option is the minimal configuration required inside the L2VPN section of a Cisco IOS XR PE router to activate VPLS functionality?
- A. l2vpnbridge group test bridge-domain testinterface TenGigE0/0/0/1.30!vfi testvpn-id 600 autodiscovery bgp rd 10.10.10.1:30route-target 1:300 signaling-protocol bgp ve-id 10
- B. l2vpnbridge group test bridge-domain testinterface TenGigE0/0/0/1.30!vfi testneighbor 10.10.10.2 pw-id 1400mpls static label local 1400 remote 1500
- C. l2vpnbridge group test bridge-domain testinterface TenGigE0/0/0/1.30!vfi testneighbor 10.10.10.2 pw-id 1400
- D. l2vpnbridge group test bridge-domain testinterface TenGigE0/0/0/1.30!vfi testvpn-id 600 autodiscovery bgp rd 10.10.10.1:30route-target 1:300 signaling-protocol bgp
- E. l2vpnbridge group test bridge-domain test vfi test autodiscovery bgp rd 10.10.10.1:30route-target 1:300 signaling-protocol bgp ve-id 10
Answer: C
NEW QUESTION 12
Which type of VPN requires a full mesh of virtual circuits to provide optimal site-to-site connectivity?
- A. MPLS Layer 3 VPNs
- B. Layer 2 overlay VPNs
- C. GET VPNs
- D. peer-to-peer VPNs
Answer: B
Explanation: 
http://etutorials.org/Networking/MPLS+VPN+Architectures/Part+2+MPLSbased+Virtual+Private+Networks/Chapter+7.+Virtual+Private+Network+VPN+Implementation+Options/Overlay+and+Peer-to-peer+VPN+Model/
Two VPN implementation models have gained widespread use:
The overlay model, where the service provider provides emulated leased lines to the customer.
The service provider provides the customer with a set of emulated leased lines. These leased lines are called VCs, which can be either constantly available {PVCs} or established on demand {SVCs}. The QoS guarantees in the overlay VPN model usually are expressed in terms of bandwidth guaranteed on a certain VC {Committed Information Rate or CIR} and maximum bandwidth available on a certain VC {Peak Information Rate or PIR}. The committed bandwidth guarantee usually is provided through the statistical nature of the Layer 2 service but depends on the overbooking strategy of the service provider The peer-to-peer model, where the service provider and the customer exchange Layer 3 routing information and the provider relays the data between the customer sites on the optimum path between the sites and without the customer's involvement. The peer-to-peer VPN model was introduced a few years ago to alleviate the drawbacks of the overlay VPN model. In the peer-to-peer model, the Provider Edge {PE} device is a router {PE-router} that directly exchanges routing information with the CPE router. The Managed Network service offered by many service providers, where the service provider also manages the CPE devices, is not relevant to this discussion because it's only a repackaging of another service. The Managed Network provider concurrently assumes the role of the VPN service provider {providing the VPN infrastructure} and part of the VPN customer role {managing the CPE device}. The peer-to-peer model provides a number of advantages over the traditional overlay model:
Routing {from the customer's perspective} becomes exceedingly simple, as the customer router exchanges routing information with only one {or a few} PE-router, whereas in the overlay VPN network, the number of neighbor routers can grow to a large number.
Routing between the customer sites is always optimal, as the provider routers know the customer's network topology and can thus establish optimum inter-site routing.
Bandwidth provisioning is simpler because the customer has to specify only the inbound and outbound bandwidths for each site {Committed Access Rate [CAR] and Committed Delivery Rate [CDR]} and not the exact site-to-site traffic profile.
The addition of a new site is simpler because the service provider provisions only an additional site and changes the configuration on the attached PE-router. Under the overlay VPN model, the service provider must provision a whole set of VCs leading from that site to other sites of the customer VPN.
Prior to an MPLS-based VPN implementation, two implementation options existed for the peer-to-peer VPN model: The shared-router approach, where several VPN customers share the same PE-router.
The dedicated-router approach, where each VPN customer has dedicated PE-routers.
Overlay VPN paradigm has a number of drawbacks, most significant of them being the need for the customer to establish point-to-point links or virtual circuits between sites. The formula to calculate how many point-to-point links or virtual circuits you need in the worst case is {{n}{n-1}}/2, where n is the number of sites you need to connect. For example, if you need to have full-mesh connectivity between 4 sites, you will need a total of 6 point-to-point links or virtual circuits. To overcome this drawback and provide the customer with optimum data transport across the Service Provider backbone, the peer-to-peer VPN concept was introduced where the Service Provider actively participates in the customer routing, accepting customer routes, transporting them across the Service Provider backbone and finally propagating them to other customer sites.
NEW QUESTION 13
What is required on a Cisco IOS XR router to assign an interface to a VRF?
- A. Assign the VRF to the interface, and then re-enable Cisco Express Forwarding on the interface.
- B. Assign the VRF to the interface, and then reset the CE-to-PE routing protocol process.
- C. Shut the interface, assign the VRF to the interface, and then no shut the interface.
- D. Remove the IP address configuration on the interface, assign the VRF to the interface, and then reconfigure the IP address on the interface.
Answer: D
Explanation: http://www.cisco.com/en/US/docs/ios_xr_sw/iosxr_r3.5/mpls/configuration/guide/gc35v3.html#wp1080845
NEW QUESTION 14
Refer the exhibit.


Which statement is correct regarding the pseudowire on connects PE7 to the 10.8.1.1 neighbor?
- A. The control word is enabled on both ends of the pseudowire
- B. The MTU size is 1500 bytes on both ends of the pseudowire
- C. Pseudowire backup is enabled
- D. The pseudowire is in the down state
Answer: B
Explanation:
show xconnect all
show ip interface brief
show mpls l2transport vc
show cable l2-vpn xconnect mpls-vc-map
NEW QUESTION 15
When you are using OSPF as the CE-to-PE routing protocol in MPLS VPN implementations, an OSPF route from customerA site 1 in Area 0 will appear as which kind of OSPF route in customerA site 2, also in Area 0?
- A. intra-area
- B. interarea
- C. E1
- D. E2
Answer: B
NEW QUESTION 16
Which option is the correct command to define an interface as Layer 2 on the Cisco ASR 9000?
- A. RP/0/RSP0/CPU0:R1{config}#int gigabitEthernet 0/6/0/0 l2transport
- B. RP/0/RSP0/CPU0:R1{config}#int gigabitEthernet 0/6/0/0 layer2
- C. RP/0/RSP0/CPU0:R1{config}#int gigabitEthernet 0/6/0/0 switchport
- D. RP/0/RSP0/CPU0:R1{config}#int gigabitEthernet 0/6/0/0 xconnect
Answer: A
Explanation: 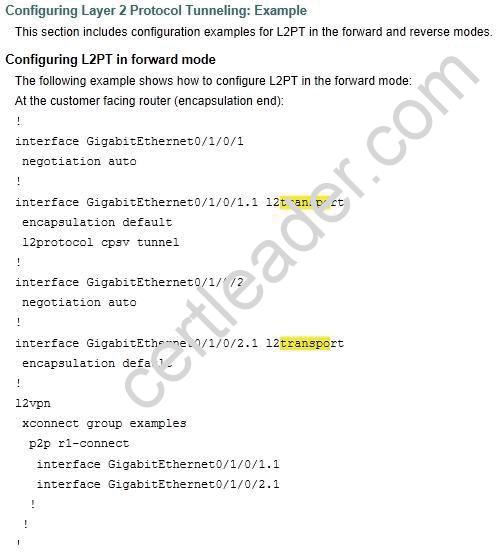
P.S. Dumpscollection now are offering 100% pass ensure 642-889 dumps! All 642-889 exam questions have been updated with correct answers: http://www.dumpscollection.net/dumps/642-889/ (126 New Questions)
- What Free 300-615 Preparation Is
- [2021-New] Cisco 400-051 Dumps With Update Exam Questions (121-130)
- [2021-New] Cisco 300-320 Dumps With Update Exam Questions (71-80)
- [2021-New] Cisco 400-101 Dumps With Update Exam Questions (191-200)
- Cisco 210-065 Exam Questions 2021
- [2021-New] Cisco 300-075 Dumps With Update Exam Questions (11-20)
- Approved 300-175 Exam Dumps 2021
- [2021-New] Cisco 400-051 Dumps With Update Exam Questions (6-15)
- Top Tips Of Rebirth 300-510 Practice
- [2021-New] Cisco 200-355 Dumps With Update Exam Questions (171-180)

