CS0-002 Exam Questions - Online Test
CS0-002 Premium VCE File

150 Lectures, 20 Hours

Your success in CompTIA CS0-002 is our sole target and we develop all our CS0-002 braindumps in a way that facilitates the attainment of this target. Not only is our CS0-002 study material the best you can find, it is also the most detailed and the most updated. CS0-002 Practice Exams for CompTIA CS0-002 are written to the highest standards of technical accuracy.
Online CS0-002 free questions and answers of New Version:
NEW QUESTION 1
An analyst is working with a network engineer to resolve a vulnerability that was found in a piece of legacy hardware, which is critical to the operation of the organization's production line. The legacy hardware does not have third-party support, and the OEM manufacturer of the controller is no longer in operation. The analyst documents the activities and verifies these actions prevent remote exploitation of the vulnerability.
Which of the following would be the MOST appropriate to remediate the controller?
- A. Segment the network to constrain access to administrative interfaces.
- B. Replace the equipment that has third-party support.
- C. Remove the legacy hardware from the network.
- D. Install an IDS on the network between the switch and the legacy equipment.
Answer: A
NEW QUESTION 2
Which of the following attacks can be prevented by using output encoding?
- A. Server-side request forgery
- B. Cross-site scripting
- C. SQL injection
- D. Command injection
- E. Cross-site request forgery
- F. Directory traversal
Answer: B
NEW QUESTION 3
A cybersecurity analyst has access to several threat feeds and wants to organize them while simultaneously comparing intelligence against network traffic.
Which of the following would BEST accomplish this goal?
- A. Continuous integration and deployment
- B. Automation and orchestration
- C. Static and dynamic analysis
- D. Information sharing and analysis
Answer: B
NEW QUESTION 4
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team’s NEXT step during the detection phase of this response process?
- A. Escalate the incident to management, who will then engage the network infrastructure team to keep them informed.
- B. Depending on system criticality, remove each affected device from the network by disabling wired and wireless connections.
- C. Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses.
- D. Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
Answer: D
NEW QUESTION 5
A security analyst is reviewing a web application. If an unauthenticated user tries to access a page in the application, the user is redirected to the login page. After successful authentication, the user is then redirected back to the original page. Some users have reported receiving phishing emails with a link that takes them to the application login page but then redirects to a fake login page after successful authentication.
Which of the following will remediate this software vulnerability?
- A. Enforce unique session IDs for the application.
- B. Deploy a WAF in front of the web application.
- C. Check for and enforce the proper domain for the redirect.
- D. Use a parameterized query to check the credentials.
- E. Implement email filtering with anti-phishing protection.
Answer: D
NEW QUESTION 6
A cybersecurity analyst is supporting an incident response effort via threat intelligence. Which of the following is the analyst MOST likely executing?
- A. Requirements analysis and collection planning
- B. Containment and eradication
- C. Recovery and post-incident review
- D. Indicator enrichment and research pivoting
Answer: A
NEW QUESTION 7
A security analyst discovers a vulnerability on an unpatched web server that is used for testing machine learning on Bing Data sets. Exploitation of the vulnerability could cost the organization $1.5 million in lost productivity. The server is located on an isolated network segment that has a 5% chance of being compromised. Which of the following is the value of this risk?
- A. $75.000
- B. $300.000
- C. $1.425 million
- D. $1.5 million
Answer: A
NEW QUESTION 8
A security analyst is reviewing packet captures from a system that was compromised. The system was already isolated from the network, but it did have network access for a few hours after being compromised. When viewing the capture in a packet analyzer, the analyst sees the following:
Which of the following can the analyst conclude?
- A. Malware is attempting to beacon to 128.50.100.3.
- B. The system is running a DoS attack against ajgidwle.com.
- C. The system is scanning ajgidwle.com for PII.
- D. Data is being exfiltrated over DNS.
Answer: D
NEW QUESTION 9
A network attack that is exploiting a vulnerability in the SNMP is detected. Which of the following should the cybersecurity analyst do FIRST?
- A. Apply the required patches to remediate the vulnerability.
- B. Escalate the incident to senior management for guidance.
- C. Disable all privileged user accounts on the network.
- D. Temporarily block the attacking IP address.
Answer: A
NEW QUESTION 10
While analyzing logs from a WAF, a cybersecurity analyst finds the following: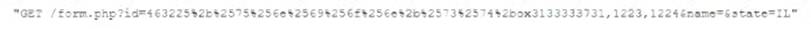
Which of the following BEST describes what the analyst has found?
- A. This is an encrypted GET HTTP request
- B. A packet is being used to bypass the WAF
- C. This is an encrypted packet
- D. This is an encoded WAF bypass
Answer: D
NEW QUESTION 11
Ransomware is identified on a company's network that affects both Windows and MAC hosts. The command and control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1. Iholdbadkeys.com, which resolves to IP address 72.172.16.2.
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?
- A. Block all outbound traffic to web host good1 iholdbadkeys.com at the border gateway.
- B. Block all outbound TCP connections to IP host address 172.172.16.2 at the border gateway.
- C. Block all outbound traffic on TCP ports 11000 to 65000 at the border gateway.
- D. Block all outbound traffic on TCP ports 11000 to 65000 to IP host address 172.172.16.2 at the border gateway.
Answer: A
NEW QUESTION 12
A product manager is working with an analyst to design a new application that will perform as a data analytics platform and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application.
Which of the following is a security concern when using a PaaS solution?
- A. The use of infrastructure-as-code capabilities leads to an increased attack surface.
- B. Patching the underlying application server becomes the responsibility of the client.
- C. The application is unable to use encryption at the database level.
- D. Insecure application programming interfaces can lead to data compromise.
Answer: D
NEW QUESTION 13
A malicious hacker wants to gather guest credentials on a hotel 802.11 network. Which of the following tools is the malicious hacker going to use to gain access to information found on the hotel network?
- A. Nikto
- B. Aircrak-ng
- C. Nessus
- D. tcpdump
Answer: A
NEW QUESTION 14
A security analyst at a technology solutions firm has uncovered the same vulnerabilities on a vulnerability scan for a long period of time. The vulnerabilities are on systems that are dedicated to the firm's largest client. Which of the following is MOST likely inhibiting the remediation efforts?
- A. The parties have an MOU between them that could prevent shutting down the systems
- B. There is a potential disruption of the vendor-client relationship
- C. Patches for the vulnerabilities have not been fully tested by the software vendor
- D. There is an SLA with the client that allows very little downtime
Answer: D
NEW QUESTION 15
A Chief Information Security Officer (CISO) wants to upgrade an organization's security posture by improving proactive activities associated with attacks from internal and external threats.
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
- A. Development of a hypothesis as part of threat hunting
- B. Log correlation, monitoring, and automated reporting through a SIEM platform
- C. Continuous compliance monitoring using SCAP dashboards
- D. Quarterly vulnerability scanning using credentialed scans
Answer: A
NEW QUESTION 16
Which of the following will allow different cloud instances to share various types of data with a minimal amount of complexity?
- A. Reverse engineering
- B. Application log collectors
- C. Workflow orchestration
- D. API integration
- E. Scripting
Answer: D
NEW QUESTION 17
A team of security analysis has been alerted to potential malware activity. The initial examination indicates one of the affected workstations on beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team's NEXT step during the detection phase of this response process?
- A. Escalate the incident to management ,who will then engage the network infrastructure team to keep them informed
- B. Depending on system critically remove each affected device from the network by disabling wired and wireless connections
- C. Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses Identify potentially affected systems by creating a correlation
- D. Identify potentially affected system by creating a correlation search in the SIEM based on the network traffic.
Answer: D
NEW QUESTION 18
A SIEM solution alerts a security analyst of a high number of login attempts against the company's webmail portal. The analyst determines the login attempts used credentials from a past data breach. Which of the following is the BEST mitigation to prevent unauthorized access?
- A. Single sign-on
- B. Mandatory access control
- C. Multifactor authentication
- D. Federation
- E. Privileged access management
Answer: E
NEW QUESTION 19
......
Recommend!! Get the Full CS0-002 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/CS0-002/ (New 186 Q&As Version)
- [2021-New] CompTIA LX0-103 Dumps With Update Exam Questions (1-10)
- The Secret Of CompTIA SY0-701 Exam Prep
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (241-250)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (551-560)
- Top Tips Of Leading CAS-003 Brain Dumps
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (31-40)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (141-150)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (131-140)
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (71-80)
- [2021-New] CompTIA LX0-103 Dumps With Update Exam Questions (11-20)

