SY0-701 Exam Questions - Online Test
SY0-701 Premium VCE File

150 Lectures, 20 Hours

Our pass rate is high to 98.9% and the similarity percentage between our SY0-701 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CompTIA SY0-701 exam in just one try? I am currently studying for the CompTIA SY0-701 exam. Latest CompTIA SY0-701 Test exam practice questions and answers, Try CompTIA SY0-701 Brain Dumps First.
Online SY0-701 free questions and answers of New Version:
NEW QUESTION 1
A security analyst is investigating a report from a penetration test. During the penetration test, consultants were able to download sensitive data from a back-end server. The back-end server was exposing an API that should have only been available from the companVs mobile application. After reviewing the back-end server logs, the security analyst finds the following entries
Which of the following is the most likely cause of the security control bypass?
- A. IP address allow list
- B. user-agent spoofing
- C. WAF bypass
- D. Referrer manipulation
Answer: B
Explanation:
User-agent spoofing is a technique that allows an attacker to modify the user-agent header of an HTTP request to impersonate another browser or device12. User-agent spoofing can be used to bypass security controls that rely on user-agent filtering or validation12. In this case, the attacker spoofed the user-agent header to match the company’s mobile application, which was allowed to access the back-end server’s API2.
NEW QUESTION 2
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop A security analyst walks the user through an installation of Wireshark and gets a five-minute pcap to analyze. The analyst observes the following output:
Which of the following attacks does the analyst most likely see in this packet capture?
- A. Session replay
- B. Evil twin
- C. Bluejacking
- D. ARP poisoning
Answer: B
Explanation:
An evil twin is a type of wireless network attack that involves setting up a rogue access point that mimics a legitimate one. It can trick users into connecting to the rogue access point instead of the real one, and then intercept or modify their traffic, steal their credentials, launch phishing pages, etc. In this packet capture, the analyst can see that there are two access points with the same SSID (CoffeeShop) but different MAC addresses (00:0c:41:82:9c:4f and 00:0c:41:82:9c:4e). This indicates that one of them is an evil twin that is trying to impersonate the other one.
NEW QUESTION 3
Which Of the following supplies non-repudiation during a forensics investiga-tion?
- A. Dumping volatile memory contents first
- B. Duplicating a drive With dd
- C. a SHA 2 signature of a drive image
- D. Logging everyone in contact with evidence
- E. Encrypting sensitive data
Answer: C
Explanation:
A SHA 2 signature is a cryptographic hash function that produces a unique and fixed-length output for any given input. It can provide non-repudiation during a forensics investigation by verifying the integrity and authenticity of a drive image and proving that it has not been altered or tampered with since it was created
NEW QUESTION 4
Which of the following best describes configuring devices to log to a centralized, off-site location for possible future reference?
- A. Log aggregation
- B. DLP
- C. Archiving
- D. SCAP
Answer: C
Explanation:
Archiving is the process of storing data for long-term preservation. In the context of IT security, archiving logs is the process of collecting and storing log files from devices in a centralized location. This allows organizations to access and analyze log data for troubleshooting, compliance, and security auditing purposes.
Log aggregation is the process of collecting log data from multiple sources and storing it in a single location. This can be done for performance or security reasons. However, log aggregation does not necessarily involve storing the logs in an off-site location.
DLP (Data Loss Prevention) is a set of technologies and processes that are used to protect sensitive data from unauthorized access, use, disclosure, alteration, or destruction. DLP can be used to prevent data from being exfiltrated from an organization's network, but it does not typically involve storing logs in an off-site location.
SCAP (Security Content Automation Protocol) is a set of standards and tools that are used to automate the assessment and remediation of security vulnerabilities. SCAP can be used to collect log data from devices, but it does not typically involve storing the logs in an off-site location.
Therefore, the best answer to the question is archiving.
NEW QUESTION 5
Remote workers in an organization use company-provided laptops with locally installed applications and locally stored data Users can store data on a remote server using an encrypted connection. The organization discovered data stored on a laptop had been made available to the public Which of the following security solutions would mitigate the risk of future data disclosures?
- A. FDE
- B. TPM
- C. HIDS
- D. VPN
Answer: A
Explanation:
Based on these definitions, the best security solution to mitigate the risk of future data disclosures from a laptop would be FDE123. FDE would prevent unauthorized access to the data stored on the laptop even if it is stolen or lost. FDE can also use TPM to store the encryption key and ensure that only trusted software can decrypt the data3. HIDS and VPN are not directly related to data encryption, but they can provide additional security benefits by detecting intrusions and protecting network traffic respectively.
NEW QUESTION 6
A security researcher is tracking an adversary by noting its attacks and techniques based on its capabilities, infrastructure, and victims. Which of the following is the researcher MOST likely using?
- A. The Diamond Model of Intrusion Analysis
- B. The Cyber Kill Chain
- C. The MITRE CVE database
- D. The incident response process
Answer: A
Explanation:
The Diamond Model is a framework for analyzing cyber threats that focuses on four key elements: adversary, capability, infrastructure, and victim. By analyzing these elements, security researchers can gain a better understanding of the threat landscape and develop more effective security strategies.
NEW QUESTION 7
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following steps:
* 1. Configure the RADIUS server.
* 2. Configure the WiFi controller.
* 3. Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01 Password: guestpass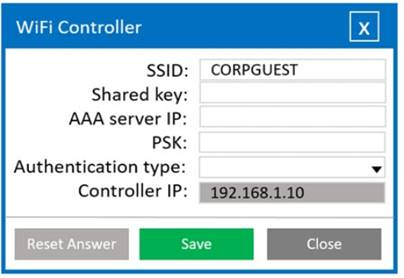
Solution:
Wifi Controller SSID: CORPGUEST
SHARED KEY: Secret
AAA server IP: 192.168.1.20
PSK: Blank
Authentication type: WPA2-EAP-PEAP-MSCHAPv2 Controller IP: 192.168.1.10
Radius Server Shared Key: Secret
Client IP: 192.168.1.10
Authentication Type: Active Directory Server IP: 192.168.1.20
Wireless Client SSID: CORPGUEST
Username: guest01 Userpassword: guestpass PSK: Blank
Authentication type: WPA2-Enterprise
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
A Chief Information Officer receives an email stating a database will be encrypted within 24 hours unless a payment of $20,000 is credited to the account mentioned In the email. This BEST describes a scenario related to:
- A. whaling.
- B. smishing.
- C. spear phishing
- D. vishing
Answer: C
Explanation:
The scenario of receiving an email stating a database will be encrypted unless a payment is made is an example of spear phishing. References: CompTIA Security+ Study Guide by Emmett Dulaney, Chapter 2: Threats, Attacks, and Vulnerabilities, Social Engineering
NEW QUESTION 9
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would best support the policy?
- A. Mobile device management
- B. Full device encryption
- C. Remote wipe
- D. Biometrics
Answer: A
Explanation:
Mobile device management (MDM) is a solution that allows an organization to manage, monitor, and secure mobile devices that are used by employees for work purposes. It can protect company information on user devices by enforcing policies and controls such as encryption, password, remote wipe, etc., and detecting and preventing unauthorized access or data leakage.
NEW QUESTION 10
An annual information security has revealed that several OS-level configurations are not in compliance due to Outdated hardening standards the company is using Which Of the following would be best to use to update and reconfigure the OS.level security configurations?
- A. CIS benchmarks
- B. GDPR guidance
- C. Regional regulations
- D. ISO 27001 standards
Answer: A
Explanation:
CIS benchmarks are best practices and standards for securing various operating systems, applications, cloud environments, etc. They are developed by a community of experts and updated regularly to reflect the latest threats and vulnerabilities. They can be used to update and reconfigure the OS-level security configurations to ensure compliance and reduce risks
NEW QUESTION 11
A manufacturing company has several one-off legacy information systems that cannot be migrated to a newer OS due to software compatibility issues. The OSs are still supported by the vendor but the industrial software is no longer supported The Chief Information Security Officer has created a resiliency plan for these systems that will allow OS patches to be installed in a non-production environment, white also creating backups of the systems for recovery. Which of the following resiliency techniques will provide these capabilities?
- A. Redundancy
- B. RAID 1+5
- C. Virtual machines
- D. Full backups
Answer: C
Explanation:
Virtual machines are software-based simulations of physical computers that run on a host system and share its resources. They can provide resiliency for legacy information systems that cannot be migrated to a newer OS due to software compatibility issues by allowing OS patches to be installed in a non-production environment without affecting the production environment. They can also create backups of the systems for recovery by taking snapshots or copies of the virtual machine files.
NEW QUESTION 12
An information security officer at a credit card transaction company is conducting a framework-mapping exercise with the internal controls. The company recently established a new office in Europe. To which of the following frameworks should the security officer map the existing controls' (Select two).
- A. ISO
- B. PCI DSS
- C. SOC
- D. GDPR
- E. CSA
- F. NIST
Answer: BD
Explanation:
PCI DSS (Payment Card Industry Data Security Standard) is a set of security standards and requirements for organizations that store, process, or transmit payment card data. It aims to protect cardholder data and prevent fraud and data breaches. GDPR (General Data Protection Regulation) is a regulation that governs the collection, processing, and transfer of personal data of individuals in the European Union. It aims to protect the privacy and rights of data subjects and impose obligations and penalties on data controllers and
processors. These are the frameworks that the security officer should map the existing controls to, as they are relevant for a credit card transaction company that has a new office in Europe
NEW QUESTION 13
A company's help desk has received calls about the wireless network being down and users being unable to connect to it. The network administrator says all access pcints are up and running. One of the help desk technicians notices the affected users are working in a near the parking Jot Which Of the following IS the most likely reason for the outage?
- A. Someone near the is jamming the signal.
- B. A user has set up a rogue access point near building.
- C. Someone set up an evil twin access Print in tie affected area.
- D. The APS in the affected area have been from the network
Answer: A
Explanation:
Wireless jamming is a way for an attacker to disrupt a wireless network and create a denial of ser-vice situation by decreasing the signal-to-noise ratio at the receiving device. The attacker would need to be relatively close to the wireless network to overwhelm the good signal. The other options are not likely to cause a wireless network outage for users near the parking lot.
NEW QUESTION 14
During a recent security assessment, a vulnerability was found in a common OS. The OS vendor was unaware of the issue and promised to release a patch within the next quarter. Which of the following best describes this type of vulnerability?
- A. Legacy operating system
- B. Weak configuration
- C. Zero day
- D. Supply chain
Answer: C
Explanation:
A zero-day vulnerability is a security flaw that is unknown to the vendor and the public, and therefore has no patch or fix available. A zero-day attack is an exploit that takes advantage of a zero-day vulnerability before the vendor or the security community becomes aware of it. A zero-day attack can cause serious damage to a system or network, as there is no defense against it until a patch is released. References: https://resources.infosecinstitute.com/certification/security-domain-1-threats-attacks-and-vulnerabilities/
https://resources.infosecinstitute.com/certification/security-domain-1-threats-attacks-and-vulnerabilities/  https://www.professormesser.com/security-plus/sy0-501/zero-day-attacks-4/
https://www.professormesser.com/security-plus/sy0-501/zero-day-attacks-4/
NEW QUESTION 15
A security analyst needs to implement an MDM solution for BYOD users that will allow the company to retain control over company emails residing on the devices and limit data exfiltration that might occur if the devices are lost or stolen.Which of the following would BEST meet these requirements? (Select TWO).
- A. Full-device encryption
- B. Network usage rules
- C. Geofencing
- D. Containerization
- E. Application whitelisting
- F. Remote control
Answer: DE
Explanation:
MDM solutions emerged to solve problems created by BYOD. With MDM, IT teams can remotely wipe devices clean if they are lost or stolen. MDM also makes the life of an IT administrator a lot easier as it allows them to enforce corporate policies, apply software updates, and even ensure that password protection is used on each device. Containerization and application whitelisting are two features of MDM that can help retain control over company emails residing on the devices and limit data exfiltration that might occur if the devices are lost or stolen.
Containerization is a technique that creates a separate and secure space on the device for work-related data and applications. This way, personal and corporate data are isolated from each other, and IT admins can manage only the work container without affecting the user’s privacy. Containerization also allows IT admins to remotely wipe only the work container if needed, leaving the personal data intact.
Application whitelisting is a technique that allows only authorized applications to run on the device. This way, IT admins can prevent users from installing or using malicious or unapproved applications that might compromise the security of corporate data. Application whitelisting also allows IT admins to control which applications can access corporate resources, such as email servers or cloud storage.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.office1.com/blog/byod-vs-mdm
NEW QUESTION 16
A new security engineer has started hardening systems. One of the hardening techniques the engineer is using involves disabling remote logins to the NAS. Users are now reporting the inability to use SCP to transfer files to the NAS, even though the data is still viewable from the users' PCs. Which of the following is the MOST likely cause of this issue?
- A. TFTP was disabled on the local hosts
- B. SSH was turned off instead of modifying the configuration file
- C. Remote login was disabled in the networkd.conf instead of using the sshd.conf.
- D. Network services are no longer running on the NA
Answer: B
Explanation:
Disabling remote logins to the NAS likely involved turning off SSH instead of modifying the configuration file. This would prevent users from using SCP to transfer files to the NAS, even though the data is still viewable from the users' PCs. Source: TechTarget
NEW QUESTION 17
Which of the following provides a catalog of security and privacy controls related to the United States federal information systems?
- A. GDPR
- B. PCI DSS
- C. ISO 27000
- D. NIST 800-53
Answer: D
Explanation:
NIST 800-53 provides a catalog of security and privacy controls related to the United States federal information systems. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 3: Architecture and Design, pp. 123-125
NEW QUESTION 18
......
100% Valid and Newest Version SY0-701 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/SY0-701-dumps.html (New 0 Q&As)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (121-130)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (121-130)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (71-80)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (391-400)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (101-110)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (451-460)
- [2021-New] CompTIA LX0-104 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (161-170)

