SY0-701 Exam Questions - Online Test
SY0-701 Premium VCE File

150 Lectures, 20 Hours

Want to know Examcollection SY0-701 Exam practice test features? Want to lear more about CompTIA CompTIA Security+ Exam certification experience? Study Pinpoint CompTIA SY0-701 answers to Renew SY0-701 questions at Examcollection. Gat a success with an absolute guarantee to pass CompTIA SY0-701 (CompTIA Security+ Exam) test on your first attempt.
Check SY0-701 free dumps before getting the full version:
NEW QUESTION 1
An organization's corporate offices were destroyed due to a natural disaster, so the organization is now setting up offices in a temporary work space. Which of the following will the organization most likely consult?
- A. The business continuity plan
- B. The risk management plan
- C. The communication plan
- D. The incident response plan
Answer: A
Explanation:
A business continuity plan is a document or a process that outlines how an organization can continue its critical operations and functions in the event of a disruption or disaster. It can include strategies and procedures for recovering or relocating resources, personnel, data, etc., to ensure minimal downtime and impact. The organization will most likely consult the business continuity plan when setting up offices in a temporary work space after its corporate offices were destroyed due to a natural disaster.
NEW QUESTION 2
A company a "right to forgotten" request To legally comply, the company must remove data related to the requester from its systems. Which Of the following Company most likely complying with?
- A. NIST CSF
- B. GDPR
- C. PCI OSS
- D. ISO 27001
Answer: B
Explanation:
GDPR stands for General Data Protection Regulation, which is a law that regulates data protection and privacy in the European Union (EU) and the European Economic Area (EEA). GDPR also applies to the transfer of personal data outside the EU and EEA areas. GDPR grants individuals the right to request the deletion or removal of their personal data from an organization’s systems under certain circumstances. This right is also known as the “right to be forgotten” or the “right to erasure”. An organization that receives such a request must comply with it within a specified time frame, unless there are legitimate grounds for retaining the data.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://gdpr-info.eu/issues/right-to-be-forgotten/
NEW QUESTION 3
A penetration tester was able to compromise a host using previously captured network traffic. Which of the
following is the result of this action?
- A. Integer overflow
- B. Race condition
- C. Memory leak
- D. Replay attack
Answer: D
Explanation:
A replay attack is a form of network attack in which valid data transmission is maliciously or fraudulently repeated or delayed12. This can allow an attacker to compromise a host by resending a previously captured message, such as a password or a session token, that looks legitimate to the receiver1. A replay attack can be prevented by using methods such as random session keys, timestamps, or one-time passwords that expire after use12. A replay attack is different from an integer overflow, which is a type of software vulnerability that occurs when an arithmetic operation attempts to create a numeric value that is too large to be represented within the available storage space3. A race condition is another type of software vulnerability that occurs when multiple processes access and manipulate the same data concurrently, and the outcome depends on the order of execution3. A memory leak is a type of software defect that occurs when a program fails to release memory that is no longer needed, causing the program to consume more memory than necessary and potentially affecting the performance or stability of the system3.
NEW QUESTION 4
Which of the following environments utilizes dummy data and is MOST likely to be installed locally on a system that allows code to be assessed directly and modified easily with each build?
- A. Production
- B. Test
- C. Staging
- D. Development
Answer: D
Explanation:
A development environment is the environment that is used to develop and test software. It is typically installed locally on a system that allows code to be assessed directly and modified easily with each build. In this environment, dummy data is often utilized to test the software's functionality.
Reference: CompTIA Security+ Study Guide, Exam SY0-601, Chapter 3: Architecture and Design
NEW QUESTION 5
Which of the following would be best to ensure data is saved to a location on a server, is easily scaled, and is centrally monitored?
- A. Edge computing
- B. Microservices
- C. Containers
- D. Thin client
Answer: C
Explanation:
Containers are a method of virtualization that allow you to run multiple isolated applications on a single server. Containers are lightweight, portable, and scalable, which means they can save resources, improve performance, and simplify deployment. Containers also enable centralized monitoring and management of the applications running on them, using tools such as Docker or Kubernetes. Containers are different from edge computing, which is a distributed computing paradigm that brings computation and data storage closer to the location where it is needed. Microservices are a software architecture style that breaks down complex applications into smaller, independent services that communicate with each other. Thin clients are devices that rely on a server to perform most of the processing tasks and only provide a user interface.
NEW QUESTION 6
An incident has occurred in the production environment.
Analyze the command outputs and identify the type of compromise.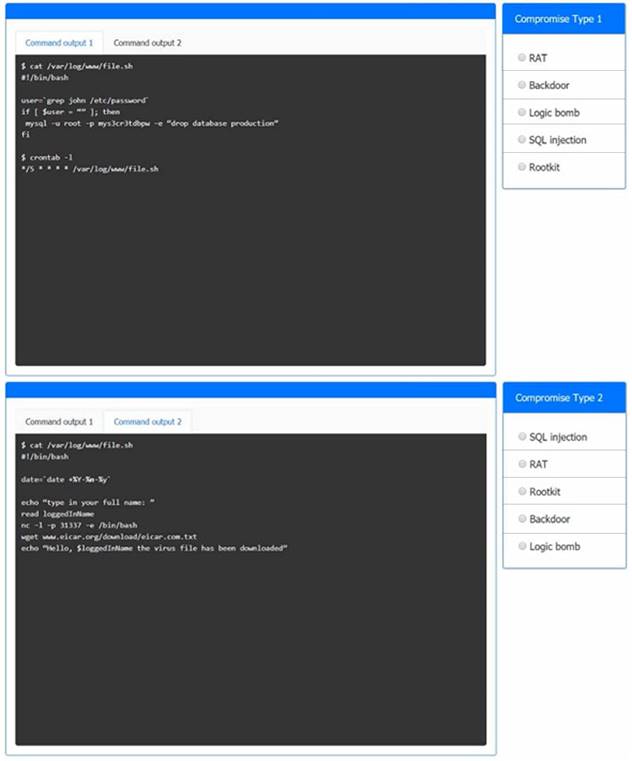
Solution:
Command Output1 = Logic Bomb
A logic bomb is a type of malicious code that executes when certain conditions are met, such as a specific date or time, or a specific user action1. In this case, the logic bomb is a script that runs every minute and checks if there is a user named john in the /etc/password file. If there is, it drops the production database using a MySQL command3. This could cause severe damage to the system and the data.
To prevent logic bombs, you should use antivirus software that can detect and remove malicious code, and also perform regular backups of your data. You should also avoid opening suspicious attachments or links from unknown sources, and use strong passwords for your accounts1.
Command Output2 = backdoorA backdoor is a type of malicious code that allows an attacker to access a system or network remotely, bypassing security measures1. In this case, the backdoor is a script that runs every time the date command is executed and prompts the user to enter their full name. Then, it opens a reverse shell connection using the nc command and downloads a virus file from a malicious website using the wget command2. This could allow the attacker to execute commands on the system and infect it with malware.
To prevent backdoors, you should use antivirus software that can detect and remove malicious code, and also update your system and applications regularly. You should also avoid executing unknown commands or scripts from untrusted sources, and use firewall rules to block unauthorized connections
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 7
An application owner reports suspicious activity on an internal financial application from various internal users within the past 14 days. A security analyst notices the following:
•Financial transactions were occurring during irregular time frames and outside of business hours by unauthorized users.
•Internal users in question were changing their passwords frequently during that time period.
•A jump box that several domain administrator users use to connect to remote devices was recently compromised.
•The authentication method used in the environment is NTLM.
Which of the following types of attacks is MOST likely being used to gain unauthorized access?
- A. Pass-the-hash
- B. Brute-force
- C. Directory traversal
- D. Replay
Answer: A
Explanation:
The suspicious activity reported by the application owner, combined with the recent compromise of the jump box and the use of NTLM authentication, suggests that an attacker is likely using a pass-the-hash attack to gain unauthorized access to the financial application. This type of attack involves stealing hashed passwords from memory and then using them to authenticate as the compromised user without needing to know the user's plaintext password. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 5
NEW QUESTION 8
A company needs to centralize its logs to create a baseline and have visibility on its security events Which of the following technologies will accomplish this objective?
- A. Security information and event management
- B. A web application firewall
- C. A vulnerability scanner
- D. A next-generation firewall
Answer: A
Explanation:
Security information and event management (SIEM) is a solution that collects, analyzes, and correlates logs and events from various sources such as firewalls, servers, applications, etc., within an organization’s network. It can centralize logs to create a baseline and have visibility on security events by providing a unified dashboard and reporting system for log management and security monitoring.
NEW QUESTION 9
A systems analyst is responsible for generating a new digital forensics chain -of- custody form Which of the following should the analyst include in this documentation? (Select two).
- A. The order of volatility
- B. A forensics NDA
- C. The provenance of the artifacts
- D. The vendor's name
- E. The date and time
- F. A warning banner
Answer: CE
Explanation:
A digital forensics chain-of-custody form is a document that records the chronological and logical sequence of custody, control, transfer, analysis, and disposition of digital evidence. A digital forensics chain-of-custody form should include the following information: The provenance of the artifacts: The provenance of the artifacts refers to the origin and history of the digital evidence, such as where, when, how, and by whom it was collected, handled, analyzed, or otherwise controlled.
The provenance of the artifacts: The provenance of the artifacts refers to the origin and history of the digital evidence, such as where, when, how, and by whom it was collected, handled, analyzed, or otherwise controlled. The date and time: The date and time refer to the specific moments when the digital evidence was collected, handled, analyzed, transferred, or disposed of by each person involved in the chain of custody.
The date and time: The date and time refer to the specific moments when the digital evidence was collected, handled, analyzed, transferred, or disposed of by each person involved in the chain of custody.
Other information that may be included in a digital forensics chain-of-custody form are: The identification of the artifacts: The identification of the artifacts refers to the unique identifiers or labels assigned to the digital evidence, such as serial numbers, barcodes, hashes, or descriptions.
The identification of the artifacts: The identification of the artifacts refers to the unique identifiers or labels assigned to the digital evidence, such as serial numbers, barcodes, hashes, or descriptions. The signatures of the custodians: The signatures of the custodians refer to the names and signatures of each person who had custody or control of the digital evidence at any point in the chain of custody.
The signatures of the custodians: The signatures of the custodians refer to the names and signatures of each person who had custody or control of the digital evidence at any point in the chain of custody. The location of the artifacts: The location of the artifacts refers to the physical or logical places where the digital evidence was stored or processed, such as a lab, a server, a cloud service, or a device.
The location of the artifacts: The location of the artifacts refers to the physical or logical places where the digital evidence was stored or processed, such as a lab, a server, a cloud service, or a device.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://resources.infosecinstitute.com/topic/chain-of-custody-in-digital-forensics/
NEW QUESTION 10
A security analyst receives an alert that indicates a user's device is displaying anomalous behavior The analyst suspects the device might be compromised Which of the following should the analyst to first?
- A. Reboot the device
- B. Set the host-based firewall to deny an incoming connection
- C. Update the antivirus definitions on the device
- D. Isolate the device
Answer: D
Explanation:
Isolating the device is the first thing that a security analyst should do if they suspect that a user’s device might be compromised. Isolating the device means disconnecting it from the network or placing it in a separate network segment to prevent further communication with potential attackers or malicious hosts. Isolating the device can help contain the incident, limit the damage or data loss, preserve the evidence, and facilitate the investigation and remediation.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://resources.infosecinstitute.com/topic/incident-response-process/
NEW QUESTION 11
The Chief Information Security Officer directed a risk reduction in shadow IT and created a policy requiring all unsanctioned high-risk SaaS applications to be blocked from user access Which of the following is the BEST security solution to reduce this risk?
- A. CASB
- B. VPN concentrator
- C. MFA
- D. VPC endpoint
Answer: A
Explanation:
A Cloud Access Security Broker (CASB) can be used to monitor and control access to cloud-based applications, including unsanctioned SaaS applications. It can help enforce policies that prevent access to high-risk SaaS applications and provide visibility into the use of such applications by employees. References: CompTIA Security+ SY0-601 Exam Objectives: 3.3 Given a scenario, implement secure mobile solutions.
NEW QUESTION 12
An organization's Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained. Which of the following roles would MOST likely include these responsibilities?
- A. Data protection officer
- B. Data owner
- C. Backup administrator
- D. Data custodian
- E. Internal auditor
Answer: D
Explanation:
The responsibilities of ensuring backups are properly maintained and implementing technical controls to protect data are the responsibilities of the data custodian role. References: CompTIA Security+ Study Guide by Emmett Dulaney, Chapter 7: Securing Hosts and Data, Data Custodian
NEW QUESTION 13
A company has numerous employees who store PHI data locally on devices. The Chief Information Officer wants to implement a solution to reduce external exposure of PHI but not affect the business.
The first step the IT team should perform is to deploy a DLP solution:
- A. for only data in transit.
- B. for only data at reset.
- C. in blocking mode.
- D. in monitoring mode.
Answer: D
Explanation:
A DLP solution in monitoring mode is a good first step to deploy for data loss prevention. It allows the IT team to observe and analyze the data flows and activities without blocking or interfering with them. It helps to identify the sources and destinations of sensitive data, the types and volumes of data involved, and the potential risks and violations. It also helps to fine-tune the DLP policies and rules before switching to blocking mode, which can disrupt business operations if not configured properly.
NEW QUESTION 14
Which of the following should be addressed first on security devices before connecting to the network?
- A. Open permissions
- B. Default settings
- C. API integration configuration
- D. Weak encryption
Answer: B
Explanation:
Before connecting security devices to the network, it is crucial to address default settings first. Manufacturers often ship devices with default settings that include default usernames, passwords, and configurations. These settings are widely known and can be easily exploited by attackers. Changing default settings helps to secure the device and prevent unauthorized access. Reference: CompTIA Security+ SY0-501 Exam Objectives, Section 3.2: "Given a scenario, implement secure systems design." (https://www.comptia.jp/pdf/Security%2B%20SY0-501%20Exam%20Objectives.pdf)
NEW QUESTION 15
The application development team is in the final stages of developing a new healthcare application. The team has requested copies of current PHI records to perform the final testing.
Which of the following would be the best way to safeguard this information without impeding the testing process?
- A. Implementing a content filter
- B. Anonymizing the data
- C. Deploying DLP tools
- D. Installing a FIM on the application server
Answer: B
Explanation:
Anonymizing the data is the process of removing personally identifiable information (PII) from data sets, so that the people whom the data describe remain anonymous12. Anonymizing the data can safeguard the PHI records without impeding the testing process, because it can protect the privacy of the patients while
preserving the data integrity and statistical accuracy for the application development team12. Anonymizing the data can be done by using techniques such as data masking, pseudonymization, generalization, data swapping, or data perturbation12.
Implementing a content filter is not the best way to safeguard the information, because it is a technique that blocks or allows access to certain types of content based on predefined rules or policies3. A content filter does not remove or encrypt PII from data sets, and it may not prevent unauthorized access or leakage of PHI records.
Deploying DLP tools is not the best way to safeguard the information, because it is a technique that monitors and prevents data exfiltration or transfer to unauthorized destinations or users. DLP tools do not remove or encrypt PII from data sets, and they may not be sufficient to protect PHI records from internal misuse or negligence.
Installing a FIM on the application server is not the best way to safeguard the information, because it is a technique that detects and alerts changes to files or directories on a system. FIM does not remove or encrypt PII from data sets, and it may not prevent unauthorized access or modification of PHI records.
NEW QUESTION 16
Which of the following supplies non-repudiation during a forensics investigation?
- A. Dumping volatile memory contents first
- B. Duplicating a drive with dd
- C. Using a SHA-2 signature of a drive image
- D. Logging everyone in contact with evidence
- E. Encrypting sensitive data
Answer: C
Explanation:
Using a SHA-2 signature of a drive image is a way to supply non-repudiation during a forensics investigation, as it can verify the integrity and authenticity of the data captured in the image. SHA-2 is a family of secure hash algorithms that can produce a unique and fixed-length digest of any input data. By hashing the drive image and comparing the signature with the original hash, the investigator can prove that the image has not been altered or tampered with since the time of acquisition. This can also help to identify the source of the data and prevent any denial from the suspect. References: https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/managing-evidence/
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/managing-evidence/ https://www.skillsoft.com/course/comptia-security-incident-response-digital-forensics-supporting-investig
https://www.skillsoft.com/course/comptia-security-incident-response-digital-forensics-supporting-investig
NEW QUESTION 17
An organization is building a new headquarters and has placed fake cameras around the building in an attempt to discourage potential intruders. Which of the following kinds of controls describes this security method?
- A. Detective
- B. Deterrent
- C. Directive
- D. Corrective
Answer: B
Explanation:
A deterrent control is a type of security control that is designed to discourage potential intruders from attempting to access or harm a system or network. A deterrent control relies on the perception or fear of negative consequences rather than the actual enforcement of those consequences. A deterrent control can also be used to influence the behavior of authorized users by reminding them of their obligations and responsibilities. An example of a deterrent control is placing fake cameras around the building, as it can create the illusion of surveillance and deter potential intruders from trying to break in. Other examples of deterrent controls are warning signs, security guards, or audit trails. References: https://www.ibm.com/topics/security-controls
https://www.ibm.com/topics/security-controls https://www.f5.com/labs/learning-center/what-are-security-controls
https://www.f5.com/labs/learning-center/what-are-security-controls
NEW QUESTION 18
......
Recommend!! Get the Full SY0-701 dumps in VCE and PDF From Certshared, Welcome to Download: https://www.certshared.com/exam/SY0-701/ (New 0 Q&As Version)
- CompTIA Jn0-210 Software 2021
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (31-40)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (311-318)
- Improve CAS-003 Forum 2021
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (151-160)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (161-170)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (121-130)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (131-140)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (81-90)

