CAS-003 Exam Questions - Online Test
CAS-003 Premium VCE File

150 Lectures, 20 Hours

Master the CAS-003 CompTIA Advanced Security Practitioner (CASP) content and be ready for exam day success quickly with this Examcollection CAS-003 download. We guarantee it!We make it a reality and give you real CAS-003 questions in our CompTIA CAS-003 braindumps.Latest 100% VALID CompTIA CAS-003 Exam Questions Dumps at below page. You can use our CompTIA CAS-003 braindumps and pass your exam.
Also have CAS-003 free dumps questions for you:
NEW QUESTION 1
An insurance company has an online quoting system for insurance premiums. It allows potential customers to fill in certain details about their car and obtain a quote. During an investigation, the following patterns were detected:
Pattern 1 – Analysis of the logs identifies that insurance premium forms are being filled in but only single fields are incrementally being updated.
Pattern 2 – For every quote completed, a new customer number is created; due to legacy systems, customer numbers are running out.
Which of the following is the attack type the system is susceptible to, and what is the BEST way to defend against it? (Select TWO).
- A. Apply a hidden field that triggers a SIEM alert
- B. Cross site scripting attack
- C. Resource exhaustion attack
- D. Input a blacklist of all known BOT malware IPs into the firewall
- E. SQL injection
- F. Implement an inline WAF and integrate into SIEM
- G. Distributed denial of service
- H. Implement firewall rules to block the attacking IP addresses
Answer: CF
Explanation:
A resource exhaustion attack involves tying up predetermined resources on a system, thereby making the resources unavailable to others.
Implementing an inline WAF would allow for protection from attacks, as well as log and alert admins to what's going on. Integrating in into SIEM allows for logs and other security-related documentation to be collected for analysis.
Incorrect Answers:
A: SIEM technology analyses security alerts generated by network hardware and applications. B: Cross site scripting attacks occur when malicious scripts are injected into otherwise trusted websites.
D: Traditional firewalls block or allow traffic. It is not, however, the best way to defend against a resource exhaustion attack.
E: A SQL injection attack occurs when the attacker makes use of a series of malicious SQL queries to directly influence the SQL database.
G: A distributed denial-of-service (DDoS) attack occurs when many compromised systems attack a single target. This results in denial of service for users of the targeted system.
H: Traditional firewalls block or allow traffic. It is not, however, the best way to defend against a resource exhaustion attack.
References:
http://searchsecurity.techtarget.com/feature/Four-questions-to-ask-befoHYPERLINK "http://searchsecurity.techtarget.com/feature/Four-questions-to-ask-before-buying-a-Webapplication- firewall"re-buying-a-Web-application-firewall
http://searchsecurity.techtarget.comHYPERLINK "http://searchsecurity.techtarget.com/definition/security-information-and-event-management- SIEM"/definition/security-information-and-event-management-SIEM https://en.wikipedia.org/wiki/Security_information_and_event_management
http:HYPERLINK "http://searchsecurity.techtarget.com/definition/distributed-denial-of-serviceattack"// searchsecurity.techtarget.com/definitHYPERLINK "http://searchsecurity.techtarget.com/definition/distributed-denial-of-serviceattack"
ion/distributed-denial-of-service-attack
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 150, 153
NEW QUESTION 2
A well-known retailer has experienced a massive credit card breach. The retailer had gone through an audit and had been presented with a potential problem on their network. Vendors were authenticating directly to the retailer’s AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where credit card servers were kept. The firewall rule was needed for an internal application that was developed, which presents risk. The retailer determined that
because the vendors were required to have site to site VPN’s no other security action was taken.
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
- A. Residual Risk calculation
- B. A cost/benefit analysis
- C. Quantitative Risk Analysis
- D. Qualitative Risk Analysis
Answer: C
Explanation:
Performing quantitative risk analysis focuses on assessing the probability of risk with a metric measurement which is usually a numerical value based on money or time.
Incorrect Answers:
A: A residual risk is one that still remains once the risk responses are applied. Thus a Residual risk calculation is not required.
B: Cost Benefit Analysis is used for Quality Planning. This is not what is required.
D: A qualitative risk analysis entails a subjective assessment of the probability of risks. The scenario warrants a quantitative risk.
References:
Project Management Institute, A Guide to the Project Management Body of Knowledge (PMBOK Guide), 5th Edition, Project Management Institute, Inc., Newtown Square, 2013, pp. 373, 585, 589 Schwalbe, Kathy, Managing Information Technology Projects, Revised 6th Edition, Course Technology, Andover, 2011, pp. 421-447
Whitaker, Sean, PMP Training Kit, O’Reilly Media, Sebastopol, 2013, pp. 335-375
NEW QUESTION 3
A software development team is conducting functional and user acceptance testing of internally developed web applications using a COTS solution. For automated testing, the solution uses valid user credentials from the enterprise directory to authenticate to each application. The solution stores the username in plain text and the corresponding password as an encoded string in a script within a file, located on a globally accessible network share. The account credentials used belong to the development team lead. To reduce the risks associated with this scenario while minimizing disruption to ongoing testing, which of the following are the BEST actions to take? (Choose two.)
- A. Restrict access to the network share by adding a group only for developers to the share’s ACL
- B. Implement a new COTS solution that does not use hard-coded credentials and integrates with directory services
- C. Obfuscate the username within the script file with encoding to prevent easy identification and the account used
- D. Provision a new user account within the enterprise directory and enable its use for authentication to the target application
- E. Share the username and password with all developers for use in their individual scripts
- F. Redesign the web applications to accept single-use, local account credentials for authentication
Answer: AB
NEW QUESTION 4
Company.org has requested a black-box security assessment be performed on key cyber terrain. On area of concern is the company’s SMTP services. The security assessor wants to run reconnaissance before taking any additional action and wishes to determine which SMTP server is Internet-facing. Which of the following commands should the assessor use to determine this information?
- A. dnsrecon –d company.org –t SOA
- B. dig company.org mx
- C. nc –v company.org
- D. whois company.org
Answer: A
NEW QUESTION 5
In a situation where data is to be recovered from an attacker’s location, which of the following are the FIRST things to capture? (Select TWO).
- A. Removable media
- B. Passwords written on scrap paper
- C. Snapshots of data on the monitor
- D. Documents on the printer
- E. Volatile system memory
- F. System hard drive
Answer: CE
Explanation:
An exact copy of the attacker’s system must be captured for further investigation so that the original data can remain unchanged. An analyst will then start the process of capturing data from the most volatile to the least volatile.
The order of volatility from most volatile to least volatile is as follows: Data in RAM, including CPU cache and recently used data and applications Data in RAM, including system and network processes
Swap files (also known as paging files) stored on local disk drives Data stored on local disk drives
Logs stored on remote systems Archive media
Incorrect Answers:
A: Removable media is not regarded as volatile data.
B: Passwords written on scrap paper is not regarded as volatile data. D: Documents on the printer is not regarded as volatile data.
F: Data stored on the system hard drive is lower in the order of volatility compared to system memory.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 250-254
http://blogs.getcertifiedgetahead.com/security-forensic-pHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensic-performance-basedquestion/" erformaHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensicperformance- based-question/"nce-based-question/
NEW QUESTION 6
A medical facility wants to purchase mobile devices for doctors and nurses. To ensure accountability, each individual will be assigned a separate mobile device. Additionally, to protect patients’ health information, management has identified the following requirements:
Data must be encrypted at rest.
The device must be disabled if it leaves the facility. The device must be disabled when tampered with
Which of the following technologies would BEST support these requirements? (Select two.)
- A. eFuse
- B. NFC
- C. GPS
- D. Biometric
- E. USB 4.1
- F. MicroSD
Answer: CD
NEW QUESTION 7
The senior security administrator wants to redesign the company DMZ to minimize the risks associated with both external and internal threats. The DMZ design must support security in depth, change management and configuration processes, and support incident reconstruction. Which of the following designs BEST supports the given requirements?
- A. A dual firewall DMZ with remote logging where each firewall is managed by a separate administrator.
- B. A single firewall DMZ where each firewall interface is managed by a separate administrator and logging to the cloud.
- C. A SaaS based firewall which logs to the company’s local storage via SSL, and is managed by the change control team.
- D. A virtualized firewall, where each virtual instance is managed by a separate administrator and logging to the same hardware.
Answer: A
Explanation:
Security in depth is the concept of creating additional layers of security. The traditional approach of securing the IT infrastructure is no longer enough. Today’s threats are multifaceted and often persistent, and traditional network perimeter security controls cannot effectively mitigate them. Organizations need to implement more effective, multi-level security controls that are embedded with their electronic assets. They need to protect key assets from both external and internal threats. This security in depth approach is meant to sustain attacks even when perimeter and traditional controls have been breached.
In this question, using two firewalls to secure the DMZ from both external and internal attacks is the best approach. Having each firewall managed by a separate administrator will reduce the chance of a configuration error being made on both firewalls. The remote logging will enable incident reconstruction.
Incorrect Answers:
B: Depending on the number of interfaces on the firewall, you could protect from external and internal threats with a single firewall although two firewalls is a better solution. However, it is not practical to have separate interfaces on the same firewall managed by different administrators. The firewall rules work together in a hierarchy to determine what traffic is allowed through each interface.
C: A SaaS based firewall can be used to protect cloud resources. However, it is not the best solution for protecting the network in this question.
D: A virtualized firewall could be used. However, multiple instances of the same firewall should be identical. They should not be configured separately by different administrators.
References:
http://www.oracle.com/technetwork/topics/entarch/oracle-wp-securiHYPERLINK "http://www.oracle.com/technetwork/topics/entarch/oracle-wp-security-ref-arch-1918345.pdf"tyref- arch-1918345.pdf
NEW QUESTION 8
A SaaS-based email service provider often receives reports from legitimate customers that their IP netblocks are on blacklists and they cannot send email. The SaaS has confirmed that affected customers typically have IP addresses within broader network ranges and some abusive customers within the same IP ranges may have performed spam campaigns. Which of the following actions should the SaaS provider perform to minimize legitimate customer impact?
- A. Inform the customer that the service provider does not have any control over third-party blacklist entrie
- B. The customer should reach out to the blacklist operator directly
- C. Perform a takedown of any customer accounts that have entries on email blacklists because this is a strong indicator of hostile behavior
- D. Work with the legal department and threaten legal action against the blacklist operator if the netblocks are not removed because this is affecting legitimate traffic
- E. Establish relationship with a blacklist operators so broad entries can be replaced with more granular entries and incorrect entries can be quickly pruned
Answer: D
NEW QUESTION 9
A security researches is gathering information about a recent spoke in the number of targeted attacks against multinational banks. The spike is on top of already sustained attacks against the banks. Some of the previous attacks have resulted in the loss of sensitive data, but as of yet the attackers have not successfully stolen any funds.
Based on the information available to the researcher, which of the following is the MOST likely threat profile?
- A. Nation-state-sponsored attackers conducting espionage for strategic gain.
- B. Insiders seeking to gain access to funds for illicit purposes.
- C. Opportunists seeking notoriety and fame for personal gain.
- D. Hackvisits seeking to make a political statement because of socio-economic factor
Answer: D
NEW QUESTION 10
An engineer maintains a corporate-owned mobility infrastructure, and the organization requires that all web browsing using corporate-owned resources be monitored. Which of the following would allow the organization to meet its requirement? (Choose two.)
- A. Exempt mobile devices from the requirement, as this will lead to privacy violations
- B. Configure the devices to use an always-on IPSec VPN
- C. Configure all management traffic to be tunneled into the enterprise via TLS
- D. Implement a VDI solution and deploy supporting client apps to devices
- E. Restrict application permissions to establish only HTTPS connections outside of the enterprise boundary
Answer: BE
NEW QUESTION 11
A company wants to perform analysis of a tool that is suspected to contain a malicious payload. A forensic analyst is given the following snippet:
^32^[34fda19(fd^43gfd/home/user/lib/module.so.343jk^rfw(342fds43g
Which of the following did the analyst use to determine the location of the malicious payload?
- A. Code deduplicators
- B. Binary reverse-engineering
- C. Fuzz testing
- D. Security containers
Answer: B
NEW QUESTION 12
Joe is a security architect who is tasked with choosing a new NIPS platform that has the ability to perform SSL inspection, analyze up to 10Gbps of traffic, can be centrally managed and only reveals inspected application payload data to specified internal security employees. Which of the following
steps should Joe take to reach the desired outcome?
- A. Research new technology vendors to look for potential product
- B. Contribute to an RFP and then evaluate RFP responses to ensure that the vendor product meets all mandatory requirement
- C. Test the product and make a product recommendation.
- D. Evaluate relevant RFC and ISO standards to choose an appropriate vendor produc
- E. Research industry surveys, interview existing customers of the product and then recommend that the product be purchased.
- F. Consider outsourcing the product evaluation and ongoing management to an outsourced provider on the basis that each of the requirements are met and a lower total cost of ownership (TCO) is achieved.
- G. Choose a popular NIPS product and then consider outsourcing the ongoing device management to a cloud provide
- H. Give access to internal security employees so that they can inspect the application payload data.
- I. Ensure that the NIPS platform can also deal with recent technological advancements, such as threats emerging from social media, BYOD and cloud storage prior to purchasing the product.
Answer: A
Explanation:
A request for a Proposal (RFP) is in essence an invitation that you present to vendors asking them to submit proposals on a specific commodity or service. This should be evaluated, then the product should be tested and then a product recommendation can be made to achieve the desired outcome. Incorrect Answers:
B: A RFC is a request for comments and this is not what is required since you need to evaluate the new technology.
C: Issues involved that has to be taken into account when outsourcing will not help Joe make a decision as to which new NIPS platform to choose.
D: Making a choice of using the most popular NIPS is not going to ensure that all the conditions will be met.
E: One of the conditions that must be met by the new NIPS platform is central management and his options do not satisfy that condition.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 197-198, 297
NEW QUESTION 13
A company has created a policy to allow employees to use their personally owned devices. The Chief Information Officer (CISO) is getting reports of company data appearing on unapproved forums and an increase in theft of personal electronic devices. Which of the following security controls would BEST reduce the risk of exposure?
- A. Disk encryption on the local drive
- B. Group policy to enforce failed login lockout
- C. Multifactor authentication
- D. Implementation of email digital signatures
Answer: A
NEW QUESTION 14
A security manager for a service provider has approved two vendors for connections to the service provider backbone. One vendor will be providing authentication services for its payment card service, and the other vendor will be providing maintenance to the service provider infrastructure sites. Which of the following business agreements is MOST relevant to the vendors and service provider’s relationship?
- A. Memorandum of Agreement
- B. Interconnection Security Agreement
- C. Non-Disclosure Agreement
- D. Operating Level Agreement
Answer: B
Explanation:
The Interconnection Security Agreement (ISA) is a document that identifies the requirements for connecting systems and networks and details what security controls are to be used to protect the systems and sensitive data.
Incorrect Answers:
A: A memorandum of agreement (MOA) is a document composed between parties to cooperate on an agreed upon project or meet an agreed objective.
C: A nondisclosure agreement (NDA) is designed to protect confidential information.
D: An operating level agreement (OLA) defines the responsibilities of each partner's internal support group.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 237, 238
NEW QUESTION 15
Which of the following technologies prevents an unauthorized HBA from viewing iSCSI target information?
- A. Deduplication
- B. Data snapshots
- C. LUN masking
- D. Storage multipaths
Answer: C
Explanation:
A logical unit number (LUN) is a unique identifier that designates individual hard disk devices or grouped devices for address by a protocol associated with a SCSI, iSCSI, Fibre Channel (FC) or similar interface. LUNs are central to the management of block storage arrays shared over a storage area network (SAN).
LUN masking subdivides access to a given port. Then, even if several LUNs are accessed through the same port, the server masks can be set to limit each server's access to the appropriate LUNs. LUN masking is typically conducted at the host bus adapter (HBA) or switch level.
Incorrect Answers:
A: Deduplication is the process of eliminating multiple copies of the same data to save storage space. It does not prevent an unauthorized HBA from viewing iSCSI target information.
B: Data snapshots are point in time copies of data often used by data backup applications. They do not prevent an unauthorized HBA from viewing iSCSI target information.
D: Storage multipaths are when you have multiple connections to a storage device. This provides path redundancy in the event of a path failure and can also (in active/active configurations) provide extra capacity by aggregating the bandwidth of the multiple storage paths. However, they do not prevent an unauthorized HBA from viewing iSCSI target information.
References:
http://searchviHYPERLINK "http://searchvirtualstorage.techtarget.com/definition/LUNmasking" rtualstorage.techtarget.com/definition/LUN-masking
NEW QUESTION 16
A network engineer wants to deploy user-based authentication across the company’s wired and wireless infrastructure at layer 2 of the OSI model. Company policies require that users be centrally managed and authenticated and that each user’s network access be controlled based on the user’s role within the company. Additionally, the central authentication system must support hierarchical trust and the ability to natively authenticate mobile devices and workstations. Which of the following are needed to implement these requirements? (Select TWO).
- A. SAML
- B. WAYF
- C. LDAP
- D. RADIUS
- E. Shibboleth
- F. PKI
Answer: CD
Explanation:
RADIUS is commonly used for the authentication of WiFi connections. We can use LDAP and RADIUS for the authentication of users and devices.
LDAP and RADIUS have something in common. They‘re both mainly protocols (more than a database) which uses attributes to carry information back and forth. They‘re clearly defined in RFC documents so you can expect products from different vendors to be able to function properly together.
RADIUS is NOT a database. It’s a protocol for asking intelligent questions to a user database. LDAP is just a database. In recent offerings it contains a bit of intelligence (like Roles, Class of Service and so on) but it still is mainly just a rather stupid database. RADIUS (actually RADIUS servers like FreeRADIUS) provide the administrator the tools to not only perform user authentication but also to authorize users based on extremely complex checks and logic. For instance you can allow access on a specific NAS only if the user belongs to a certain category, is a member of a specific group and an outside script allows access. There’s no way to perform any type of such complex decisions in a user database.
Incorrect Answers:
A: Security Assertion Markup Language (SAML) is an XML-based, open-standard data format for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. It is used for authenticating users, not devices.
B: WAYF stands for Where Are You From. It is a third-party authentication provider used by websites of some online institutions. WAYF does not meet the requirements in this question.
E: Shibboleth is an open-source project that provides Single Sign-On capabilities and allows sites to make informed authorization decisions for individual access of protected online resources. It cannot perform the device authentication required in this question.
F: PKI (Public Key Infrastructure) uses digital certificates to affirm the identity of the certificate subject and bind that identity to the public key contained in the certificate. PKI does not meet the requirements in this question.
References: https://kkalev.wordpress.com/2007/03/17/radius-vs-ldap/
NEW QUESTION 17
A security administrator is hardening a TrustedSolaris server that processes sensitive data. The data owner has established the following security requirements:
The data is for internal consumption only and shall not be distributed to outside individuals The systems administrator should not have access to the data processed by the server
The integrity of the kernel image is maintained
Which of the following host-based security controls BEST enforce the data owner’s requirements? (Choose three.)
- A. SELinux
- B. DLP
- C. HIDS
- D. Host-based firewall
- E. Measured boot
- F. Data encryption
- G. Watermarking
Answer: CEF
NEW QUESTION 18
A storage as a service company implements both encryption at rest as well as encryption in transit of customers’ dat
- A. The security administrator is concerned with the overall security of the encrypted customer data stored by the company servers and wants the development team to implement asolution that will strengthen the customer’s encryption ke
- B. Which of the following, if implemented, will MOST increase the time an offline password attack against the customers’ data would take?
- C. key = NULL ; for (int i=0; i<5000; i++) { key = sha(key + password) }
- D. password = NULL ; for (int i=0; i<10000; i++) { password = sha256(key) }
- E. password = password + sha(password+salt) + aes256(password+salt)
- F. key = aes128(sha256(password), password))
Answer: A
Explanation:
References:
http://HYPERLINK "http://stackoverflow.com/questions/4948322/fundamental-difference-betweenhashing- and-encryption-algorithms"sHYPERLINK
"http://stackoverflow.com/questions/4948322/fundamental-difference-between-hashing-andencryption- algorithms"tackoverflow.com/questions/4948322/fundamental-difference-betweenhashing-
and-encryption-aHYPERLINK "http://stackoverflow.com/questions/4948322/fundamentaldifference- between-hashing-and-encryption-algorithms"lgorithms
NEW QUESTION 19
A security analyst has been asked to create a list of external IT security concerns, which are applicable to the organization. The intent is to show the different types of external actors, their attack vectors, and the types of vulnerabilities that would cause business impact. The Chief Information Security Officer (CISO) will then present this list to the board to request funding for controls in areas that have insufficient coverage.
Which of the following exercise types should the analyst perform?
- A. Summarize the most recently disclosed vulnerabilities.
- B. Research industry best practices and latest RFCs.
- C. Undertake an external vulnerability scan and penetration test.
- D. Conduct a threat modeling exercis
Answer: D
NEW QUESTION 20
A company sales manager received a memo from the company’s financial department which stated that the company would not be putting its software products through the same security testing as previous years to reduce the research and development cost by 20 percent for the upcoming year. The memo also stated that the marketing material and service level agreement for each product would remain unchanged. The sales manager has reviewed the sales goals for the upcoming year and identified an increased target across the software products that will be affected by the financial department’s change. All software products will continue to go through new development in the coming year. Which of the following should the sales manager do to ensure the company stays out of trouble?
- A. Discuss the issue with the software product's user groups
- B. Consult the company’s legal department on practices and law
- C. Contact senior finance management and provide background information
- D. Seek industry outreach for software practices and law
Answer: B
Explanation:
To ensure that the company stays out of trouble, the sales manager should enquire about the legal ramifications of the change by consulting with the company’s legal department, particularly as the marketing material is not being amended.
Incorrect Answers:
A: The software product's user groups would not have insight on the legal ramifications of the change by the company, and they might not have knowledge of the service-level agreements or any contracts that the company has with other customers.
C: The sales manager does not have additional background information to provide.
D: Legal information pertaining to internal operations should be obtained from the company’s legal department.
NEW QUESTION 21
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company’s products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below: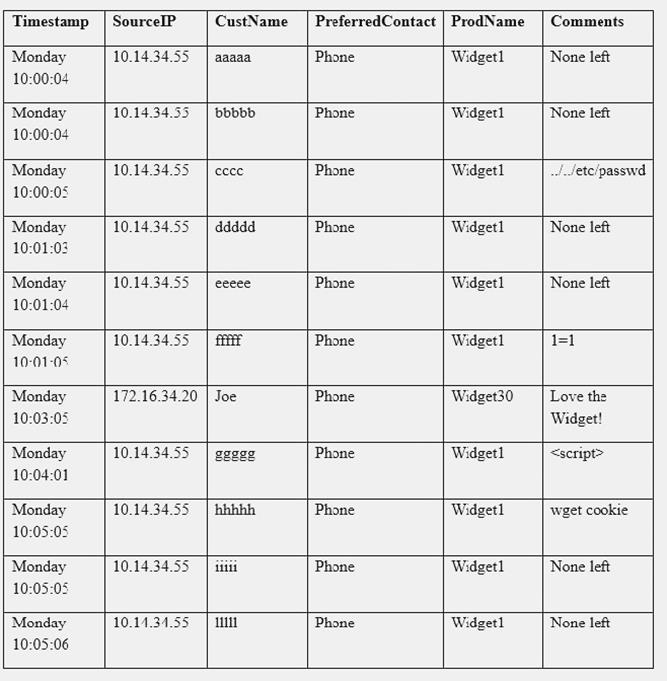
Which of the following is the MOST likely type of activity occurring?
- A. SQL injection
- B. XSS scanning
- C. Fuzzing
- D. Brute forcing
Answer: A
NEW QUESTION 22
A security engineer is embedded with a development team to ensure security is built into products being developed. The security engineer wants to ensure developers are not blocked by a large number of security requirements applied at specific schedule points. Which of the following solutions BEST meets the engineer’s goal?
- A. Schedule weekly reviews of al unit test results with the entire development team and follow up between meetings with surprise code inspections.
- B. Develop and implement a set of automated security tests to be installed on each development team leader’s workstation.
- C. Enforce code quality and reuse standards into the requirements definition phase of the waterfall development process.
- D. Deploy an integrated software tool that builds and tests each portion of code committed by developers and provides feedback.
Answer: C
NEW QUESTION 23
An administrator has enabled salting for users' passwords on a UNIX box. A penetration tester must attempt to retrieve password hashes. Which of the following files must the penetration tester use to eventually obtain passwords on the system? (Select TWO).
- A. /etc/passwd
- B. /etc/shadow
- C. /etc/security
- D. /etc/password
- E. /sbin/logon
- F. /bin/bash
Answer: AB
Explanation:
In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes a password or passphrase. In this question, enabling salting for users' passwords means to store the passwords in an encrypted format.
Traditional Unix systems keep user account information, including one-way encrypted passwords, in a text file called ``/etc/passwd''. As this file is used by many tools (such as ``ls'') to display file ownerships, etc. by matching user id #'s with the user's names, the file needs to be world-readable. Consequentially, this can be somewhat of a security risk.
Another method of storing account information is with the shadow password format. As with the traditional method, this method stores account information in the /etc/passwd file in a compatible
format. However, the password is stored as a single "x" character (ie. not actually stored in this file). A second file, called ``/etc/shadow'', contains encrypted password as well as other information such as account or password expiration values, etc.
Incorrect Answers:
C: The /etc/security file contains group information. It does not contain usernames or passwords. D: There is no /etc/password file. Usernames are stored in the /etc/passwd file.
E: There is no /sbin/logon file. Usernames are stored in the /etc/passwd file.
F: /bin/bash is a UNIX shell used to run a script. It is not where usernames or passwords are stored. References:
http://www.tldp.org/LDP/lame/LAME/linux-admin-made-easy/shadow-file-formats.HYPERLINK "http://www.tldp.org/LDP/lame/LAME/linux-admin-made-easy/shadow-file-formats.html"html
NEW QUESTION 24
One of the objectives of a bank is to instill a security awareness culture. Which of the following are techniques that could help to achieve this? (Choose two.)
- A. Blue teaming
- B. Phishing simulations
- C. Lunch-and-learn
- D. Random audits
- E. Continuous monitoring
- F. Separation of duties
Answer: BE
NEW QUESTION 25
A network engineer is attempting to design-in resiliency characteristics for an enterprise network’s VPN services.
If the engineer wants to help ensure some resilience against zero-day vulnerabilities explogted against the VPN implementation, which of the following decisions would BEST support this objective?
- A. Implement a reverse proxy for VPN traffic that is defended and monitored by the organization’s SOC with near-real-time alerting to administrators.
- B. Subscribe to a managed service provider capable of supporting the mitigation of advanced DDoS attacks on the enterprise’s pool of VPN concentrators.
- C. Distribute the VPN concentrators across multiple systems at different physical sites to ensure some backup services are available in the event of primary site loss.
- D. Employ a second VPN layer concurrently where the other layer’s cryptographic implementation is sourced from a different vendor.
Answer: D
NEW QUESTION 26
Ann is testing the robustness of a marketing website through an intercepting proxy. She has intercepted the following HTTP request:
POST /login.aspx HTTP/1.1 Host: comptia.org
Content-type: text/html txtUsername=ann&txtPassword=ann&alreadyLoggedIn=false&submit=true
Which of the following should Ann perform to test whether the website is susceptible to a simple authentication bypass?
- A. Remove all of the post data and change the request to /login.aspx from POST to GET
- B. Attempt to brute force all usernames and passwords using a password cracker
- C. Remove the txtPassword post data and change alreadyLoggedIn from false to true
- D. Remove the txtUsername and txtPassword post data and toggle submit from true to false
Answer: C
Explanation:
The text “txtUsername=ann&txtPassword=ann” is an attempted login using a username of ‘ann’ and also a password of ‘ann’.
The text “alreadyLoggedIn=false” is saying that Ann is not already logged in.
To test whether we can bypass the authentication, we can attempt the login without the password
and we can see if we can bypass the ‘alreadyloggedin’ check by changing alreadyLoggedIn from false to true. If we are able to log in, then we have bypassed the authentication check.
Incorrect Answers:
A: GET /login.aspx would just return the login form. This does not test whether the website is susceptible to a simple authentication bypass.
B: We do not want to guess the usernames and passwords. We want to see if we can get into the site without authentication.
D: We need to submit the data so we cannot toggle submit from true to false.
NEW QUESTION 27
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiations, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability
2. The data will be hosted and managed outside of the company’s geographical location
The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant on the project, which of the following should the project’s security consultant recommend as the NEXT step?
- A. Develop a security exemption, as it does not meet the security policies
- B. Mitigate the risk by asking the vendor to accept the in-country privacy principles
- C. Require the solution owner to accept the identified risks and consequences
- D. Review the entire procurement process to determine the lessons learned
Answer: C
NEW QUESTION 28
Users have been reporting unusual automated phone calls, including names and phone numbers, that appear to come from devices internal to the company. Which of the following should the systems administrator do to BEST address this problem?
- A. Add an ACL to the firewall to block VoIP.
- B. Change the settings on the phone system to use SIP-TLS.
- C. Have the phones download new configurations over TFTP.
- D. Enable QoS configuration on the phone VLA
Answer: B
NEW QUESTION 29
Following a security assessment, the Chief Information Security Officer (CISO) is reviewing the results of the assessment and evaluating potential risk treatment strategies. As part of the CISO’s
evaluation, a judgment of potential impact based on the identified risk is performed. To prioritize response actions, the CISO uses past experience to take into account the exposure factor as well as the external accessibility of the weakness identified. Which of the following is the CISO performing?
- A. Documentation of lessons learned
- B. Quantitative risk assessment
- C. Qualitative assessment of risk
- D. Business impact scoring
- E. Threat modeling
Answer: B
NEW QUESTION 30
......
Recommend!! Get the Full CAS-003 dumps in VCE and PDF From Certstest, Welcome to Download: https://www.certstest.com/dumps/CAS-003/ (New 443 Q&As Version)
- The Latest Guide To SY0-601 Preparation
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (1-10)
- Top Tips Of Latest SY0-701 Free Practice Exam
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (611-620)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (121-130)
- Download XK0-004 Cram 2021
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (21-30)
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (31-40)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (41-50)

