SY0-701 Exam Questions - Online Test
SY0-701 Premium VCE File

150 Lectures, 20 Hours

Act now and download your CompTIA SY0-701 test today! Do not waste time for the worthless CompTIA SY0-701 tutorials. Download Far out CompTIA CompTIA Security+ Exam exam with real questions and answers and begin to learn CompTIA SY0-701 with a classic professional.
Online CompTIA SY0-701 free dumps demo Below:
NEW QUESTION 1
A desktop computer was recently stolen from a desk located in the lobby of an office building. Which of the following would be the best way to secure a replacement computer and deter future theft?
- A. Installing proximity card readers on all entryway doors
- B. Deploying motion sensor cameras in the lobby
- C. Encrypting the hard drive on the new desktop
- D. Using cable locks on the hardware
Answer: D
Explanation:
Using cable locks on the hardware can be an effective way to secure a desktop computer and deter future theft. Cable locks are physical security devices that attach to the computer case and to a nearby stationary object, such as a desk or wall. This makes it more difficult for a thief to remove the computer without damaging it or attracting attention.
Installing proximity card readers on all entryway doors can enhance physical security by limiting access to authorized individuals. Deploying motion sensor cameras in the lobby can also help deter theft by capturing
images of any unauthorized individuals entering the premises or attempting to steal the computer. Encrypting the hard drive on the replacement desktop can also help protect sensitive data in the event of theft, but it does not provide physical security for the device itself.
NEW QUESTION 2
Which of the following environments typically hosts the current version configurations and code, compares user-story responses and workflow, and uses a modified version of actual data for testing?
- A. Development
- B. Staging
- C. Production
- D. Test
Answer: B
Explanation:
Staging is an environment in the software development lifecycle that is used to test a modified version of the actual data, current version configurations, and code. This environment compares user-story responses and workflow before the software is released to the production environment. References: CompTIA Security+ Study Guide, Sixth Edition, Sybex, pg. 496
NEW QUESTION 3
A security engineer learns that a non-critical application was compromised. The most recent version of the application includes a malicious reverse proxy while the application is running. Which of the following should the engineer is to quickly contain the incident with the least amount of impact?
- A. Configure firewall rules to block malicious inbound access.
- B. Manually uninstall the update that contains the backdoor.
- C. Add the application hash to the organization's blocklist.
- D. Tum off all computers that have the application installed.
Answer: C
Explanation:
A reverse proxy backdoor is a malicious reverse proxy that can intercept and manipulate the traffic between the client and the web server3. This can allow an attacker to access sensitive data or execute commands on the web server.
One possible way to quickly contain the incident with the least amount of impact is to add the application hash to the organization’s blocklist. A blocklist is a list of applications or files that are not allowed to run on a system or network. By adding the application hash to the blocklist, the security engineer can prevent the malicious application from running and communicating with the reverse proxy backdoor.
NEW QUESTION 4
A security engineer is setting up passwordless authentication for the first time. INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.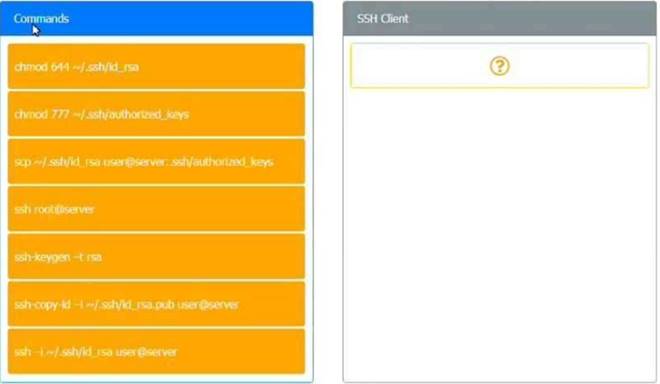
Solution:
A screenshot of a computer Description automatically generated with medium confidence
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 5
A developer is building a new portal to deliver single-pane-of-glass management capabilities to customers with multiple firewalls. To Improve the user experience, the developer wants to implement an authentication and authorization standard that uses security tokens that contain assertions to pass user Information between nodes. Which of the following roles should the developer configure to meet these requirements? (Select TWO).
- A. Identity processor
- B. Service requestor
- C. Identity provider
- D. Service provider
- E. Tokenized resource
- F. Notarized referral
Answer: CD
Explanation:
An identity provider (IdP) is responsible for authenticating users and generating security tokens containing user information. A service provider (SP) is responsible for accepting security tokens and granting access to resources based on the user's identity.
NEW QUESTION 6
Hackers recently attacked a company's network and obtained several unfavorable pictures from the Chief Executive Officer's workstation. The hackers are threatening to send the images to the press if a ransom is not paid. Which of the following is impacted the MOST?
- A. Identify theft
- B. Data loss
- C. Data exfiltration
- D. Reputation
Answer: D
Explanation:
The best option that describes what is impacted the most by the hackers’ attack and threat would be D. Reputation. Reputation is the perception or opinion that others have about a person or an organization. Reputation can affect the trust, credibility, and success of a person or an organization. In this scenario, if the hackers send the unfavorable pictures to the press, it can damage the reputation of the Chief Executive Officer and the company, and cause negative consequences such as loss of customers, partners, investors, or employees.
NEW QUESTION 7
A security analyst is hardening a network infrastructure The analyst is given the following requirements
• Preserve the use of public IP addresses assigned to equipment on the core router
• Enable "in transport" encryption protection to the web server with the strongest ciphers. Which of the following should the analyst implement to meet these requirements? (Select two).
- A. Configure VLANs on the core router
- B. Configure NAT on the core router.
- C. Configure BGP on the core router
- D. Enable AES encryption on the web server
- E. Enable 3DES encryption on the web server
- F. Enable TLSv2 encryption on the web server
Answer: BF
Explanation:
NAT (Network Address Translation) is a technique that allows a router to translate private IP addresses into
public IP addresses and vice versa. It can preserve the use of public IP addresses assigned to equipment on the core router by allowing multiple devices to share a single public IP address. TLSv2 (Transport Layer Security version 2) is a cryptographic protocol that provides secure communication over the internet. It can enable “in transport” encryption protection to the web server with the strongest ciphers by encrypting the data transmitted between the web server and the clients using advanced algorithms and key exchange methods.
NEW QUESTION 8
Security engineers are working on digital certificate management with the top priority of making administration easier. Which of the following certificates is the best option?
- A. User
- B. Wildcard
- C. Self-signed
- D. Root
Answer: B
Explanation:
A wildcard certificate is a type of digital certificate that can be used to secure multiple subdomains under a single domain name. For example, a wildcard certificate for *.example.com can be used to secure www.example.com, mail.example.com, blog.example.com, etc. A wildcard certificate can make administration easier by reducing the number of certificates that need to be issued, managed, and renewed. It can also save costs and simplify configuration.
NEW QUESTION 9
Which of the following environments would MOST likely be used to assess the execution of component parts of a system at both the hardware and software levels and to measure performance characteristics?
- A. Test
- B. Staging
- C. Development
- D. Production
Answer: A
Explanation:
The test environment is used to assess the execution of component parts of a system at both the hardware and software levels and to measure performance characteristics. References: CompTIA Security+ Study Guide 601, Chapter 2
NEW QUESTION 10
A user received an SMS on a mobile phone that asked for bank details. Which of the following social engineering techniques was used in this case?
- A. SPIM
- B. Vishing
- C. Spear phishing
- D. Smishing
Answer: D
Explanation:
Smishing is a type of social engineering technique that involves sending fraudulent or malicious text messages (SMS) to a user’s mobile phone. It can trick the user into providing personal or financial information, clicking on malicious links, downloading malware, etc., by impersonating a legitimate entity or creating a sense of urgency or curiosity.
NEW QUESTION 11
Which of the following controls would be the MOST cost-effective and time-efficient to deter intrusions at the perimeter of a restricted, remote military training area?
(Select TWO).
- A. Barricades
- B. Thermal sensors
- C. Drones
- D. Signage
- E. Motion sensors
- F. Guards
- G. Bollards
Answer: AD
Explanation:
Barricades and signage are the most cost-effective and time-efficient controls to deter intrusions at the perimeter of a restricted, remote military training area. References: CompTIA Security+ Study Guide Exam SY0-601, Chapter 7
CompTIA Security+ Study Guide Exam SY0-601, Chapter 7
NEW QUESTION 12
Which of the following controls would provide the BEST protection against tailgating?
- A. Access control vestibule
- B. Closed-circuit television
- C. Proximity card reader
- D. Faraday cage
Answer: A
Explanation:
Access control vestibules, also known as mantraps or airlocks, are physical security features that require individuals to pass through two or more doors to enter a secure area. They are effective at preventing tailgating, as only one person can pass through each door at a time.
References: https://www.comptia.org/content/guides/what-is-a-mantrap
https://www.comptia.org/content/guides/what-is-a-mantrap CompTIA Security+ Study Guide, Sixth Edition (SY0-601), page 222
CompTIA Security+ Study Guide, Sixth Edition (SY0-601), page 222
NEW QUESTION 13
Which of the following would produce the closet experience of responding to an actual incident response scenario?
- A. Lessons learned
- B. Simulation
- C. Walk-through
- D. Tabletop
Answer: B
Explanation:
A simulation exercise is designed to create an experience that is as close as possible to a real-world incident response scenario. It involves simulating an attack or other security incident and then having security personnel respond to the situation as they would in a real incident. References: CompTIA Security+ SY0-601 Exam Objectives: 1.1 Explain the importance of implementing security concepts, methodologies, and practices.
NEW QUESTION 14
When planning to build a virtual environment, an administrator need to achieve the following,
•Establish polices in Limit who can create new VMs
•Allocate resources according to actual utilization‘
•Require justication for requests outside of the standard requirements.
•Create standardized categories based on size and resource requirements Which of the following is the administrator MOST likely trying to do?
- A. Implement IaaS replication
- B. Product against VM escape
- C. Deploy a PaaS
- D. Avoid VM sprawl
Answer: D
Explanation:
The administrator is most likely trying to avoid VM sprawl, which occurs when too many VMs are created and managed poorly, leading to resource waste and increased security risks. The listed actions can help establish policies, resource allocation, and categorization to prevent unnecessary VM creation and ensure proper management. Reference: CompTIA Security+ Certification Exam Objectives, Exam SY0-601, 3.6 Given a scenario, implement the appropriate virtualization components.
NEW QUESTION 15
An organization would like to remediate the risk associated with its cloud service provider not meeting its advertised 99.999% availability metrics. Which of the following should the organization consult for the exact requirements for the cloud provider?
- A. SLA
- B. BPA
- C. NDA
- D. MOU
Answer: A
Explanation:
The Service Level Agreement (SLA) is a contract between the cloud service provider and the organization that stipulates the exact requirements for the cloud provider. It outlines the level of service that the provider must deliver, including the minimum uptime percentage, support response times, and the remedies and penalties for failing to meet the agreed-upon service levels.
NEW QUESTION 16
A security analyst has received several reports of an issue on an internal web application. Users state they are having to provide their credentials twice to log in. The analyst checks with the application team and notes this is not an expected behavior. After looking at several logs, the analyst decides to run some commands on the gateway and obtains the following output:
Which of the following BEST describes the attack the company is experiencing?
- A. MAC flooding
- B. URL redirection
- C. ARP poisoning
- D. DNS hijacking
Answer: C
Explanation:
The output of the “netstat -ano” command shows that there are two connections to the same IP address and port number. This indicates that there are two active sessions between the client and server.
The issue of users having to provide their credentials twice to log in is known as a double login prompt issue. This issue can occur due to various reasons such as incorrect configuration of authentication settings, incorrect configuration of web server settings, or issues with the client’s browser.
Based on the output of the “netstat -ano” command, it is difficult to determine the exact cause of the issue. However, it is possible that an attacker is intercepting traffic between the client and server and stealing user credentials. This type of attack is known as C. ARP poisoning.
ARP poisoning is a type of attack where an attacker sends fake ARP messages to associate their MAC address with the IP address of another device on the network. This allows them to intercept traffic between the two devices and steal sensitive information such as user credentials.
NEW QUESTION 17
A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
- A. A An incident response plan
- B. A communications plan
- C. A business continuity plan
- D. A disaster recovery plan
Answer: B
Explanation:
The organization should use a communications plan to inform the affected parties. A communications plan is a document that outlines how an organization will communicate with internal and external stakeholders during a crisis or incident. It should include details such as who will be responsible for communicating with different stakeholders, what channels will be used to communicate, and what messages will be communicated.
An incident response plan is a document that outlines the steps an organization will take to respond to a security incident or data breach. A business continuity plan is a document that outlines how an organization will continue to operate during and after a disruption. A disaster recovery plan is a document that outlines how an organization will recover its IT infrastructure and data after a disaster.
NEW QUESTION 18
......
Thanks for reading the newest SY0-701 exam dumps! We recommend you to try the PREMIUM 2passeasy SY0-701 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/SY0-701/ (0 Q&As Dumps)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (61-70)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (141-150)
- Rebirth PT0-003 Prep For CompTIA PenTest+ Exam Certification
- Top Tips Of Improve PT0-002 Preparation Labs
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (91-100)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (551-560)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (11-20)
- Most Up-to-date XK0-004 Free Practice Questions For CompTIA Linux+ Certification Exam Certification
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (91-100)

