SY0-701 Exam Questions - Online Test
SY0-701 Premium VCE File

150 Lectures, 20 Hours

Cause all that matters here is passing the CompTIA SY0-701 exam. Cause all that you need is a high score of SY0-701 CompTIA Security+ Exam exam. The only one thing you need to do is downloading Actualtests SY0-701 exam study guides now. We will not let you down with our money-back guarantee.
Online CompTIA SY0-701 free dumps demo Below:
NEW QUESTION 1
Which of the following would be BEST for a technician to review to determine the total risk an organization can bear when assessing a "cloud-first" adoption strategy?
- A. Risk matrix
- B. Risk tolerance
- C. Risk register
- D. Risk appetite
Answer: B
Explanation:
To determine the total risk an organization can bear, a technician should review the organization's risk tolerance, which is the amount of risk the organization is willing to accept. This information will help determine the organization's "cloud-first" adoption strategy. References: CompTIA Security+ Certification Exam Objectives (SY0-601)
NEW QUESTION 2
A company wants to build a new website to sell products online. The website wd I host a storefront application that allow visitors to add products to a shopping cart and pay for products using a credit card. which Of the following protocols •would be most secure to implement?
- A. SSL
- B. SFTP
- C. SNMP
- D. TLS
Answer: D
Explanation:
TLS (Transport Layer Security) is a cryptographic protocol that provides secure communication over the internet. It can protect the data transmitted between the website and the visitors from eavesdropping, tampering, etc. It is the most secure protocol to implement for a website that sells products online using a credit card.
NEW QUESTION 3
A security architect is required to deploy to conference rooms some workstations that will allow sensitive data to be displayed on large screens. Due to the nature of the data, it cannot be stored in the conference rooms. The file share is located in a local data center. Which of the following should the security architect recommend to best meet the requirement?
- A. Fog computing and KVMs
- B. VDI and thin clients
- C. Private cloud and DLP
- D. Full drive encryption and thick clients
Answer: B
Explanation:
VDI and thin clients are the best solution to deploy to conference rooms for displaying sensitive data on large screens. VDI stands for virtual desktop infrastructure, which is a technology that hosts the desktop operating systems and applications on a central server or cloud and allows users to access them remotely. Thin clients are devices that have minimal hardware and software components and rely on a network connection to the VDI system. By using VDI and thin clients, the security architect can ensure that the sensitive data is not stored in the conference rooms, but rather in a secure data center or cloud. The thin clients can also be easily managed and updated centrally, reducing the maintenance costs and risks. References: https://www.acecloudhosting.com/blog/what-is-vdi-thin-client/
https://www.acecloudhosting.com/blog/what-is-vdi-thin-client/  https://www.parallels.com/blogs/ras/vdi-thin-client/
https://www.parallels.com/blogs/ras/vdi-thin-client/
NEW QUESTION 4
Which of the following would provide guidelines on how to label new network devices as part of the initial configuration?
- A. IP schema
- B. Application baseline configuration
- C. Standard naming convention policy
- D. Wireless LAN and network perimeter diagram
Answer: C
Explanation:
A standard naming convention policy would provide guidelines on how to label new network devices as part of the initial configuration. A standard naming convention policy is a document that defines the rules and formats for naming network devices, such as routers, switches, firewalls, servers, or printers. A standard naming convention policy can help an organization achieve consistency, clarity, and efficiency in network management and administration.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Network_Virtualization/PathIsolationDesignGuide/P
NEW QUESTION 5
A security engineer updated an application on company workstations. The application was running before the update, but it is no longer launching successfully. Which of the following most likely needs to be updated?
- A. Blocklist
- B. Deny list
- C. Quarantine list
- D. Approved fist
Answer: D
Explanation:
Approved list is a list of applications or programs that are allowed to run on a system or network. An approved list can prevent unauthorized or malicious software from running and compromising the security of the system or network. An approved list can also help with patch management and compatibility issues. If the security engineer updated an application on the company workstations, the application may need to be added or updated on the approved list to be able to launch successfully. References: 1
CompTIA Security+ Certification
Exam Objectives, page 10, Domain 2.0: Architecture and Design, Objective 2.4: Explain the importance of
embedded and specialized systems security 2
CompTIA Security+ Certification Exam Objectives, page 12,
Domain 3.0: Implementation, Objective 3.1: Implement secure network architecture concepts 3
https://www.comptia.org/blog/what-is-application-whitelisting
NEW QUESTION 6
The management team has requested that the security team implement 802.1X into the existing wireless network setup. The following requirements must be met:
• Minimal interruption to the end user
• Mutual certificate validation
Which of the following authentication protocols would meet these requirements?
- A. EAP-FAST
- B. PSK
- C. EAP-TTLS
- D. EAP-TLS
Answer: D
Explanation:
EAP-TLS (Extensible Authentication Protocol - Transport Layer Security) is an authentication protocol that uses certificates to provide mutual authentication between the client and the authentication server. It also allows for the encryption of user credentials, making EAP-TLS a secure and reliable authentication protocol. According to the CompTIA Security+ SY0-601 Official Text Book, EAP-TLS is well-suited for wireless networks due to its mutual authentication capabilities and its ability to securely store credentials. It is also the preferred authentication protocol for 802.1X wireless networks.
NEW QUESTION 7
A security administrator would like to ensure all cloud servers will have software preinstalled for facilitating vulnerability scanning and continuous monitoring. Which of the following concepts should the administrator utilize?
- A. Provisioning
- B. Staging
- C. Development
- D. Quality assurance
Answer: A
Explanation:
Provisioning is the process of creating and setting up IT infrastructure, and includes the steps required to manage user and system access to various resources . Provisioning can be done for servers, cloud environments, users, networks, services, and more .
In this case, the security administrator wants to ensure that all cloud servers will have software preinstalled for facilitating vulnerability scanning and continuous monitoring. This means that the administrator needs to
provision the cloud servers with the necessary software and configuration before they are deployed or used by customers or end users. Provisioning can help automate and standardize the process of setting up cloud servers and reduce the risk of human errors or inconsistencies.
NEW QUESTION 8
Several universities are participating in a collaborative research project and need to share compute and storage resources. Which of the following cloud deployment strategies would best meet this need?
- A. Community
- B. Private
- C. Public
- D. Hybrid
Answer: A
Explanation:
A community cloud deployment strategy would best meet the need of several universities participating in a collaborative research project and needing to share compute and storage resources. A community cloud is a type of cloud service model that provides a shared platform for multiple organizations with common interests, goals, or requirements. A community cloud can offer benefits such as cost savings, scalability, security, privacy, compliance, and collaboration. References:
https://www.comptia.org/blog/cloud-service-models-saas-paas-and-iaas-explained https://www.certblaster.com/wp-content/uploads/2020/11/CompTIA-Security-SY0-601-Exam-Objectives-1.0.pd
NEW QUESTION 9
Which of the following describes the exploitation of an interactive process to gain access to restricted areas?
- A. Persistence
- B. Port scanning
- C. Privilege escalation
- D. Pharming
Answer: C
Explanation:
Privilege escalation describes the exploitation of an interactive process to gain access to restricted areas. It is a type of attack that allows a normal user to obtain higher privileges or access rights on a system or network, such as administrative or root access. Privilege escalation can be achieved by exploiting a vulnerability, design flaw, or misconfiguration in the system or application. Privilege escalation can allow an attacker to perform unauthorized actions, such as accessing sensitive data, installing malware, or compromising other systems. References: https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/privilege-escalation-3/
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/privilege-escalation-3/ https://www.linkedin.com/learning/comptia-security-plus-sy0-601-cert-prep-2-secure-code-design-and-im
https://www.linkedin.com/learning/comptia-security-plus-sy0-601-cert-prep-2-secure-code-design-and-im
NEW QUESTION 10
Which of the following best describes the situation where a successfully onboarded employee who is using a fingerprint reader is denied access at the company's mam gate?
- A. Crossover error rate
- B. False match raw
- C. False rejection
- D. False positive
Answer: C
Explanation:
False rejection Short
A false rejection occurs when a biometric system fails to recognize an authorized user and denies access. This can happen due to poor quality of the biometric sample, environmental factors, or system errors. References: https://www.comptia.org/blog/what-is-biometrics
NEW QUESTION 11
A systems integrator is installing a new access control system for a building. The new system will need to connect to the Company's AD server In order to validate current employees. Which of the following should the systems integrator configure to be the most secure?
- A. HTTPS
- B. SSH
- C. SFTP
- D. LDAPS
Answer: D
Explanation:
LDAPS (Lightweight Directory Access Protocol Secure) is the most secure protocol to use for connecting to an Active Directory server, as it encrypts the communication between the client and the server using SSL/TLS. This prevents eavesdropping, tampering, or spoofing of the authentication and authorization data.
References: 1
CompTIA Security+ Certification Exam Objectives, page 13, Domain 3.0: Implementation,
Objective 3.2: Implement secure protocols 2
CompTIA Security+ Certification Exam Objectives, page 15,
Domain 3.0: Implementation, Objective 3.5: Implement secure authentication mechanisms 3
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc731
NEW QUESTION 12
A police department is using the cloud to share information city officials Which of the cloud models describes this scenario?
- A. Hybrid
- B. private
- C. pubic
- D. Community
Answer: D
Explanation:
A community cloud model describes a scenario where a cloud service is shared among multiple organizations that have common goals, interests, or requirements. A community cloud can be hosted by one of the organizations, a third-party provider, or a combination of both. A community cloud can offer benefits such as cost savings, security, compliance, and collaboration. A police department using the cloud to share information with city officials is an example of a community cloud model.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.ibm.com/cloud/learn/community-cloud
NEW QUESTION 13
An employee, receives an email stating he won the lottery. The email includes a link that requests a name, mobile phone number, address, and date of birth be provided to confirm employee's identity before sending him the prize. Which of the following BEST describes this type of email?
- A. Spear phishing
- B. Whaling
- C. Phishing
- D. Vishing
Answer: C
Explanation:
Phishing is a type of social engineering attack that uses fraudulent emails or other forms of communication to trick users into revealing sensitive information, such as passwords, credit card numbers, or personal details. Phishing emails often impersonate legitimate entities, such as banks, online services, or lottery organizations, and entice users to click on malicious links or attachments that lead to fake websites or malware downloads. Phishing emails usually target a large number of users indiscriminately, hoping that some of them will fall for the scam.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.kaspersky.com/resource-center/definitions/what-is-phishing
NEW QUESTION 14
You are security administrator investigating a potential infection on a network.
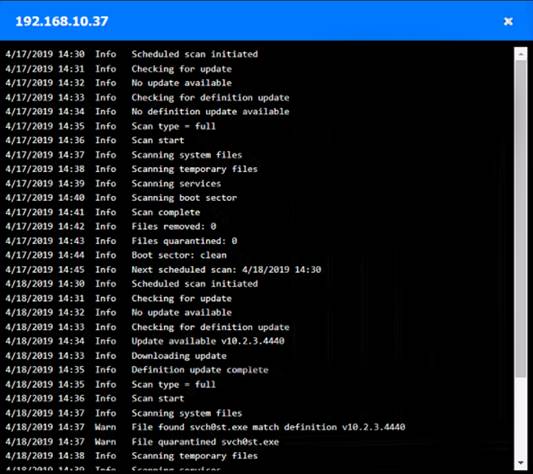
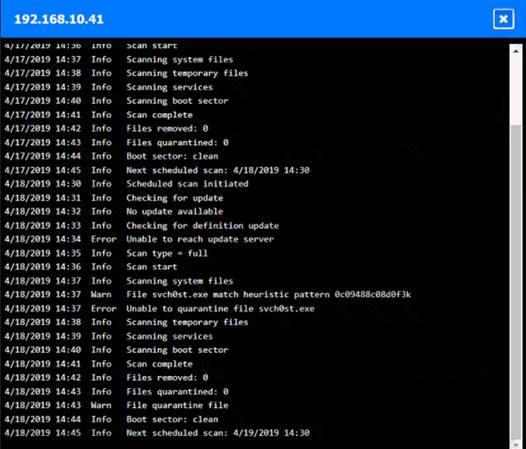
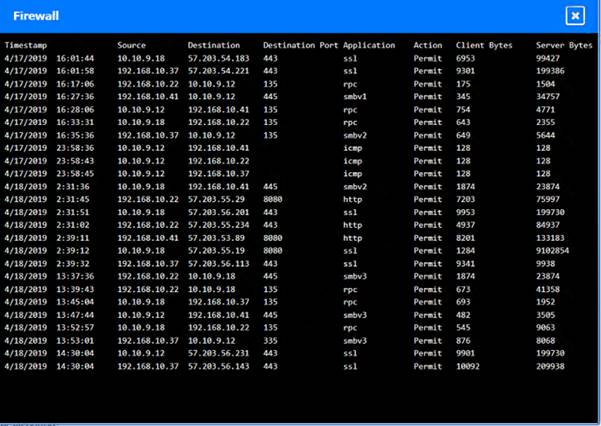
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.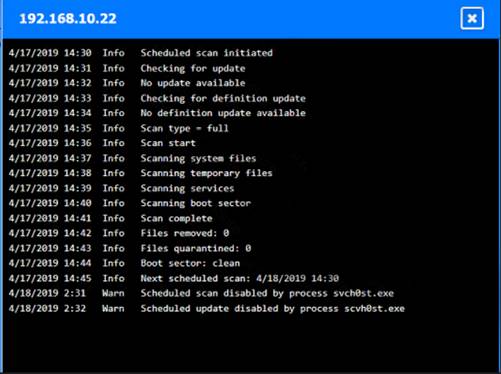
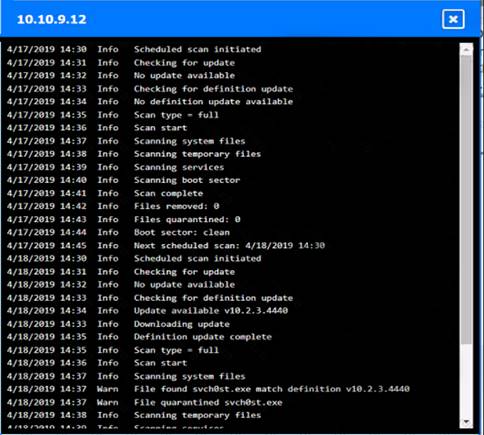
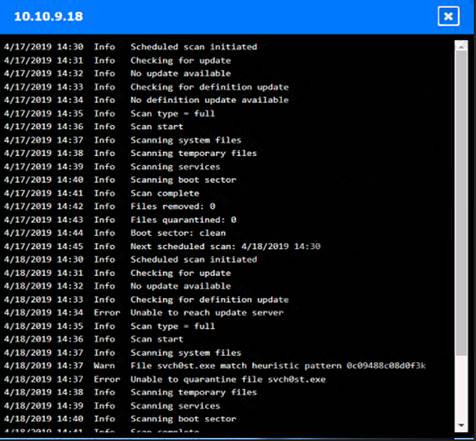
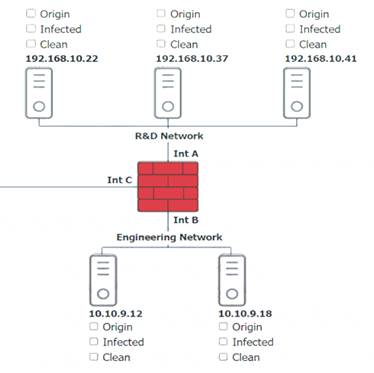
Solution:
Based on the logs, it seems that the host that originated the infection is 192.168.10.22. This host has a
suspicious process named svchost.exe running on port 443, which is unusual for a Windows service. It also
has a large number of outbound connections to different IP addresses on port 443, indicating that it is part of a botnet.
The firewall log shows that this host has been communicating with 10.10.9.18, which is another infected host on the engineering network. This host also has a suspicious process named svchost.exe running on port 443, and a large number of outbound connections to different IP addresses on port 443.
The other hosts on the R&D network (192.168.10.37 and192.168.10.41) are clean, as they do not have any
suspicious processes or connections.
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
A security administrator installed a new web server. The administrator did this to increase the capacity for an application due to resource exhaustion on another server. Which of the following algorithms should the administrator use to split the number of the connections on each server in half?
- A. Weighted response
- B. Round-robin
- C. Least connection
- D. Weighted least connection
Answer: B
Explanation:
Round-robin is a type of load balancing algorithm that distributes traffic to a list of servers in rotation. It is a static algorithm that does not take into account the state of the system for the distribution of tasks. It assumes that all servers have equal capacity and can handle an equal amount of traffic.
NEW QUESTION 16
A company recently completed the transition from data centers to the cloud. Which of the following solutions will best enable the company to detect security threats in applications that run in isolated environments within the cloud environment?
- A. Security groups
- B. Container security
- C. Virtual networks
- D. Segmentation
Answer: B
Explanation:
Container security is a solution that can enable the company to detect security threats in applications that run in isolated environments within the cloud environment. Containers are units of software that package code and dependencies together, allowing applications to run quickly and reliably across different computing environments. Container security involves securing the container images, the container runtime, and the container orchestration platforms. Container security can help prevent unauthorized access, data breaches, malware infections, or denial-of-service attacks on the applications running in containers. References: 1
CompTIA Security+ Certification Exam Objectives, page 9, Domain 2.0: Architecture and Design, Objective 2.3 : Summarize secure application development, deployment, and automation concepts 2
CompTIA Security+
Certification Exam Objectives, page 10, Domain 2.0: Architecture and Design, Objective 2.4: Explain the
importance of embedded and specialized systems security 3
https://www.comptia.org/blog/what-is-container-security
NEW QUESTION 17
A backdoor was detected on the containerized application environment. The investigation detected that a zero-day vulnerability was introduced when the latest container image version was downloaded from a public registry. Which of the following is the BEST solution to prevent this type of incident from occurring again?
- A. Enforce the use of a controlled trusted source of container images
- B. Deploy an IPS solution capable of detecting signatures of attacks targeting containers
- C. Define a vulnerability scan to assess container images before being introduced on the environment
- D. Create a dedicated VPC for the containerized environment
Answer: A
Explanation:
Enforcing the use of a controlled trusted source of container images is the best solution to prevent incidents like the introduction of a zero-day vulnerability through container images from occurring again. References: CompTIA Security+ Study Guide by Emmett Dulaney, Chapter 11: Cloud Security, Container Security
NEW QUESTION 18
......
100% Valid and Newest Version SY0-701 Questions & Answers shared by Allfreedumps.com, Get Full Dumps HERE: https://www.allfreedumps.com/SY0-701-dumps.html (New 0 Q&As)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (71-80)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (51-60)
- Regenerate PT0-002 Free Dumps For CompTIA PenTest+ Certification Exam Certification
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (41-50)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (641-650)
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (61-70)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (81-90)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (81-90)
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (81-90)

