CAS-003 Exam Questions - Online Test
CAS-003 Premium VCE File

150 Lectures, 20 Hours

We provide real CAS-003 exam questions and answers braindumps in two formats. Download PDF & Practice Tests. Pass CompTIA CAS-003 Exam quickly & easily. The CAS-003 PDF type is available for reading and printing. You can print more and practice many times. With the help of our CompTIA CAS-003 dumps pdf and vce product and material, you can easily pass the CAS-003 exam.
CompTIA CAS-003 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.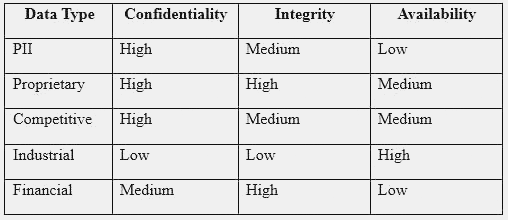
Based on the data classification table above, which of the following BEST describes the overall classification?
- A. High confidentiality, high availability
- B. High confidentiality, medium availability
- C. Low availability, low confidentiality
- D. High integrity, low availability
Answer: B
NEW QUESTION 2
An investigator wants to collect the most volatile data first in an incident to preserve the data that runs the highest risk of being lost. After memory, which of the following BEST represents the remaining order of volatility that the investigator should follow?
- A. File system information, swap files, network processes, system processes and raw disk blocks.
- B. Raw disk blocks, network processes, system processes, swap files and file system information.
- C. System processes, network processes, file system information, swap files and raw disk blocks.
- D. Raw disk blocks, swap files, network processes, system processes, and file system informatio
Answer: C
Explanation:
The order in which you should collect evidence is referred to as the Order of volatility. Generally, evidence should be collected from the most volatile to the least volatile. The order of volatility from most volatile to least volatile is as follows:
Data in RAM, including CPU cache and recently used data and applications Data in RAM, including system and network processes
Swap files (also known as paging files) stored on local disk drives Data stored on local disk drives
Logs stored on remote systems Archive media
Incorrect Answers:
A: System and network processes are more volatile than file system information and swap files. B: System and network processes are more volatile than raw disk blocks.
D: System and network processes are more volatile than raw disk blocks and swap files. References:
http://blogs.getcertifiedgetahead.com/security-forensic-performance-baseHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensic-performance-based-question/"d-question/
NEW QUESTION 3
Which of the following system would be at the GREATEST risk of compromise if found to have an open vulnerability associated with perfect ... secrecy?
- A. Endpoints
- B. VPN concentrators
- C. Virtual hosts
- D. SIEM
- E. Layer 2 switches
Answer: B
NEW QUESTION 4
Given the code snippet below: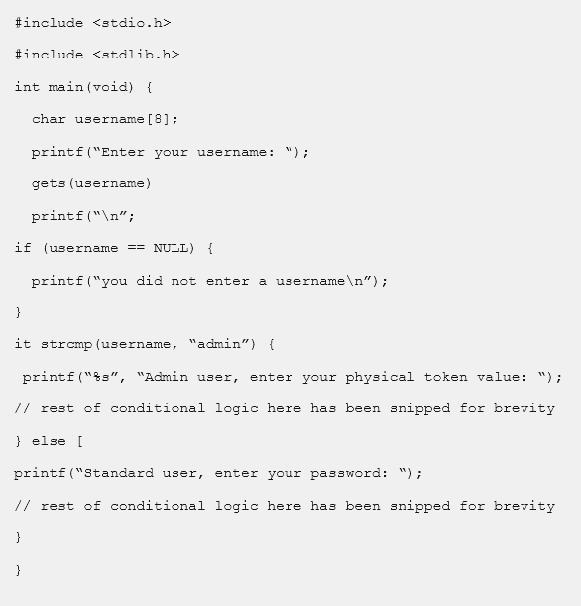
Which of the following vulnerability types in the MOST concerning?
- A. Only short usernames are supported, which could result in brute forcing of credentials.
- B. Buffer overflow in the username parameter could lead to a memory corruption vulnerability.
- C. Hardcoded usernames with different code paths taken depend on which user is entered.
- D. Format string vulnerability is present for admin users but not for standard user
Answer: B
NEW QUESTION 5
A security analyst is reviewing the corporate MDM settings and notices some disabled settings, which consequently permit users to download programs from untrusted developers and manually install them. After some conversations, it is confirmed that these settings were disabled to support the internal development of mobile applications. The security analyst is now recommending that developers and testers have a separate device profile allowing this, and that the rest of the organization’s users do not have the ability to manually download and install untrusted applications. Which of the following settings should be toggled to achieve the goal? (Choose two.)
- A. OTA updates
- B. Remote wiping
- C. Side loading
- D. Sandboxing
- E. Containerization
- F. Signed applications
Answer: EF
NEW QUESTION 6
A cybersecurity analyst is hired to review the security the posture of a company. The cybersecurity analyst notice a very high network bandwidth consumption due to SYN floods from a small number of IP addresses. Which of the following would be the BEST action to take to support incident response?
- A. Increase the company's bandwidth.
- B. Apply ingress filters at the routers.
- C. Install a packet capturing tool.
- D. Block all SYN packet
Answer: B
NEW QUESTION 7
The DLP solution has been showing some unidentified encrypted data being sent using FTP to a remote server. A vulnerability scan found a collection of Linux servers that are missing OS level patches. Upon further investigation, a technician notices that there are a few unidentified processes running on a number of the servers. What would be a key FIRST step for the data security team to undertake at this point?
- A. Capture process ID data and submit to anti-virus vendor for review.
- B. Reboot the Linux servers, check running processes, and install needed patches.
- C. Remove a single Linux server from production and place in quarantine.
- D. Notify upper management of a security breach.
- E. Conduct a bit level image, including RAM, of one or more of the Linux server
Answer: E
Explanation:
Incident management (IM) is a necessary part of a security program. When effective, it mitigates business impact, identifies weaknesses in controls, and helps fine-tune response processes.
In this question, an attack has been identified and confirmed. When a server is compromised or used to commit a crime, it is often necessary to seize it for forensics analysis. Security teams often face two challenges when trying to remove a physical server from service: retention of potential evidence in volatile storage or removal of a device from a critical business process.
Evidence retention is a problem when the investigator wants to retain RAM content. For example, removing power from a server starts the process of mitigating business impact, but it also denies forensic analysis of data, processes, keys, and possible footprints left by an attacker.
A full a bit level image, including RAM should be taken of one or more of the Linux servers. In many cases, if your environment has been deliberately attacked, you may want to take legal action against the perpetrators. In order to preserve this option, you should gather evidence that can be used
against them, even if a decision is ultimately made not to pursue such action. It is extremely important to back up the compromised systems as soon as possible. Back up the systems prior to performing any actions that could affect data integrity on the original media.
Incorrect Answers:
A: Capturing process ID data and submitting it to anti-virus vendor for review would not be the first step. Furthermore, it is unlikely that a virus is the cause of the problem on the LINUX servers. It is much more likely that the missing OS level patches left the systems vulnerable.
B: Rebooting the Linux servers would lose the contents of the running RAM. This may be needed for litigation so a full backup including RAM should be taken first. Then the servers can be cleaned and patched.
C: Removing a single Linux server from production and placing it in quarantine would probably involve powering off the server. Powering off the server would lose the contents of the running RAM. This may be needed for litigation so a full backup including RAM should be taken first.
D: Notifying upper management of a security breach probably should be done after the security breach is contained. You should follow standard incident management procedures first. Reporting on the incident is one of the later steps in the process.
References:
http://whatis.techtarget.com/reference/FiHYPERLINK "http://whatis.techtarget.com/reference/Five- Steps-to-Incident-Management-in-a-Virtualized-Environment"ve-Steps-to-Incident-Management-ina-
Virtualized-Environment
https://technet.miHYPERLINK "https://technet.microsoft.com/enhttps:// certkingdom.com
us/library/cc700825.aspx"crosoft.com/en-us/library/cc700825.aspx
NEW QUESTION 8
A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices.
Which of the following tools is the security engineer using to produce the above output?
- A. Vulnerability scanner
- B. SIEM
- C. Port scanner
- D. SCAP scanner
Answer: B
NEW QUESTION 9
A project manager is working with a team that is tasked to develop software applications in a structured environment and host them in a vendor’s cloud-based infrastructure. The organization will maintain responsibility for the software but will not manage the underlying server applications. Which of the following does the organization plan to leverage?
- A. SaaS
- B. PaaS
- C. IaaS
- D. Hybrid cloud
- E. Network virtualization
Answer: B
NEW QUESTION 10
A hospital’s security team recently determined its network was breached and patient data was accessed by an external entity. The Chief Information Security Officer (CISO) of the hospital approaches the executive management team with this information, reports the vulnerability that led to the breach has already been remediated, and explains the team is continuing to follow the appropriate incident response plan. The executive team is concerned about the hospital’s brand reputation and asks the CISO when the incident should be disclosed to the affected patients. Which of the following is the MOST appropriate response?
- A. When it is mandated by their legal and regulatory requirements
- B. As soon as possible in the interest of the patients
- C. As soon as the public relations department is ready to be interviewed
- D. When all steps related to the incident response plan are completed
- E. Upon the approval of the Chief Executive Officer (CEO) to release information to the public
Answer: A
NEW QUESTION 11
Wireless users are reporting issues with the company’s video conferencing and VoIP systems. The security administrator notices internal DoS attacks from infected PCs on the network causing the VoIP system to drop calls. The security administrator also notices that the SIP servers are unavailable
during these attacks. Which of the following security controls will MOST likely mitigate the VoIP DoS attacks on the network? (Select TWO).
- A. Install a HIPS on the SIP servers
- B. Configure 802.1X on the network
- C. Update the corporate firewall to block attacking addresses
- D. Configure 802.11e on the network
- E. Configure 802.1q on the network
Answer: AD
Explanation:
Host-based intrusion prevention system (HIPS) is an installed software package that will monitor a single host for suspicious activity by analyzing events taking place within that host.
IEEE 802.11e is deemed to be of significant consequence for delay-sensitive applications, such as Voice over Wireless LAN and streaming multimedia.
Incorrect Answers:
B: 802.1X is used by devices to attach to a LAN or WLAN.
C: Updating the corporate firewall will not work as the DoS attacks are from an internal source. E: 802.1q is used for VLAN tagging.
References: https:HYPERLINK
"https://en.wikipedia.org/wiki/Intrusion_prevention_system"//en.wikipedia.org/wiki/Intrusion_pre vention_system
https://en.wikipedia.orHYPERLINK "https://en.wikipedia.org/wiki/IEEE_802.11e- 2005"g/wiki/IEEE_802.11e-2005
https://en.wikipedia.org/wiki/IEEE_802.1X https://en.wikipedia.org/wiki/IEEE_802.1Q
NEW QUESTION 12
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a special platform was discovered, allowing an attacker to capture the data between the end user and the web server providing these services. After invest the new vulnerability, it was determined that the web services providing are being impacted by this new threat. Which of the following data types a MOST likely at risk of exposure based on this new threat? (Select TWO)
- A. Cardholder data
- B. intellectual property
- C. Personal health information
- D. Employee records
- E. Corporate financial data
Answer: AC
NEW QUESTION 13
At 9:00 am each morning, all of the virtual desktops in a VDI implementation become extremely slow and/or unresponsive. The outage lasts for around 10 minutes, after which everything runs properly again. The administrator has traced the problem to a lab of thin clients that are all booted at 9:00 am each morning. Which of the following is the MOST likely cause of the problem and the BEST solution? (Select TWO).
- A. Add guests with more memory to increase capacity of the infrastructure.
- B. A backup is running on the thin clients at 9am every morning.
- C. Install more memory in the thin clients to handle the increased load while booting.
- D. Booting all the lab desktops at the same time is creating excessive I/O.
- E. Install 10-Gb uplinks between the hosts and the lab to increase network capacity.
- F. Install faster SSD drives in the storage system used in the infrastructure.
- G. The lab desktops are saturating the network while booting.
- H. The lab desktops are using more memory than is available to the host system
Answer: DF
Explanation:
The problem lasts for 10 minutes at 9am every day and has been traced to the lab desktops. This question is asking for the MOST likely cause of the problem. The most likely cause of the problem is that the lab desktops being started at the same time at the beginning of the day is causing excessive disk I/O as the operating systems are being read and loaded from disk storage.
The solution is to install faster SSD drives in the storage system that contains the desktop operating systems.
Incorrect Answers:
A: If a lack of memory was the cause of the problem, the problem would occur throughout the day; not just for the 10 minutes it takes to boot the lab desktops. Therefore adding guests with more memory will not solve the problem so this answer is incorrect.
B: This question is asking for the MOST likely cause of the problem. A backup running on the thin clients at 9am every morning as soon as the lab desktops start up is an unlikely cause of the problem. It is much more likely that the lab desktops starting up at the same time is causing high disk I/O.
C: The lab desktops starting up would not cause memory issues on the thin clients so adding memory will not solve the issue.
E: The lab desktops starting up would not cause network bandwidth issues so increasing the bandwidth will not solve the issue.
G: The lab desktops starting up would not saturate the network.
H: If the lab desktops are using more memory than is available to the host systems, the problem would occur throughout the day; not just for the 10 minutes it takes to boot the lab desktops.
NEW QUESTION 14
A SaaS-based email service provider often receives reports from legitimate customers that their IP netblocks are on blacklists and they cannot send email. The SaaS has confirmed that affected customers typically have IP addresses within broader network ranges and some abusive customers within the same IP ranges may have performed spam campaigns. Which of the following actions should the SaaS provider perform to minimize legitimate customer impact?
- A. Inform the customer that the service provider does not have any control over third-party blacklist entrie
- B. The customer should reach out to the blacklist operator directly
- C. Perform a takedown of any customer accounts that have entries on email blacklists because this is a strong indicator of hostile behavior
- D. Work with the legal department and threaten legal action against the blacklist operator if the netblocks are not removed because this is affecting legitimate traffic
- E. Establish relationship with a blacklist operators so broad entries can be replaced with more granular entries and incorrect entries can be quickly pruned
Answer: D
NEW QUESTION 15
A company is in the process of implementing a new front end user interface for its customers, the goal is to provide them with more self-service functionality. The application has been written by developers over the last six months and the project is currently in the test phase.
Which of the following security activities should be implemented as part of the SDL in order to provide the MOST security coverage over the solution? (Select TWO).
- A. Perform unit testing of the binary code
- B. Perform code review over a sampling of the front end source code
- C. Perform black box penetration testing over the solution
- D. Perform grey box penetration testing over the solution
- E. Perform static code review over the front end source code
Answer: DE
Explanation:
With grey box penetration testing it means that you have limited insight into the devise which would most probable by some code knowledge and this type of testing over the solution would provide the most security coverage under the circumstances.
A Code review refers to the examination of an application (the new network based software product in this case) that is designed to identify and assess threats to the organization. With a static code review it is assumed that you have all the sources available for the application that is being examined. By performing a static code review over the front end source code you can provide adequate security coverage over the solution.
Incorrect Answers:
A: Unit testing of the binary code will not provide the most security coverage.
B: Code review over a sampling of the front end source code will not provide adequate security coverage.
C: Black box penetration testing is best done when the source code is not available. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 168-169
NEW QUESTION 16
An intruder was recently discovered inside the data center, a highly sensitive are
- A. To gain access, the intruder circumvented numerous layers of physical and electronic security measure
- B. Company leadership has asked for a thorough review of physical security controls to prevent this from happening agai
- C. Which of the following departments are the MOST heavily invested in rectifying the problem? (Select THREE).
- D. Facilities management
- E. Human resources
- F. Research and development
- G. Programming
- H. Data center operations
- I. Marketing
- J. Information technology
Answer: AEG
Explanation:
A: Facilities management is responsible for the physical security measures in a facility or building. E: The breach occurred in the data center, therefore the Data center operations would be greatly concerned.
G: Data centers are important aspects of information technology (IT) in large corporations. Therefore the IT department would be greatly concerned.
Incorrect Answers:
B: Human Resources security is concerned with employees joining an organization, moving between
different positions in the organization, and leaving the organization.
C: Research and Development is concerned with security at the design and development stage of a system.
D: Programming security is concerned with application code and application vulnerabilities. F: Marketing is not concerned with security.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 281, 326-328
NEW QUESTION 17
An administrator wants to install a patch to an application. INSTRUCTIONS
Given the scenario, download, verify, and install the patch in the most secure manner. The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.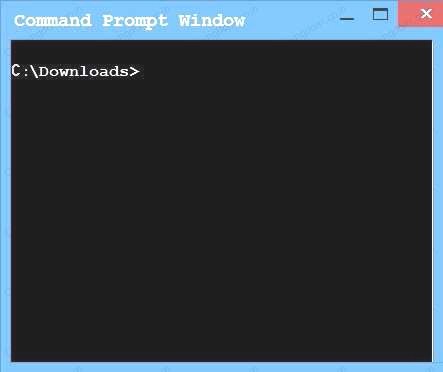

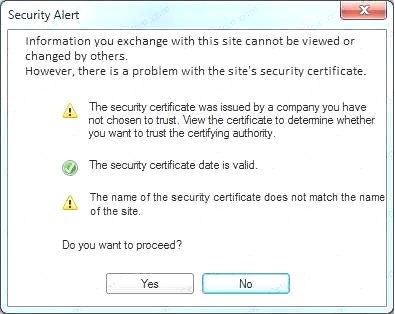

- A. In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
 Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown:
Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown: Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show
Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show - B. Make sure that the hash matches.
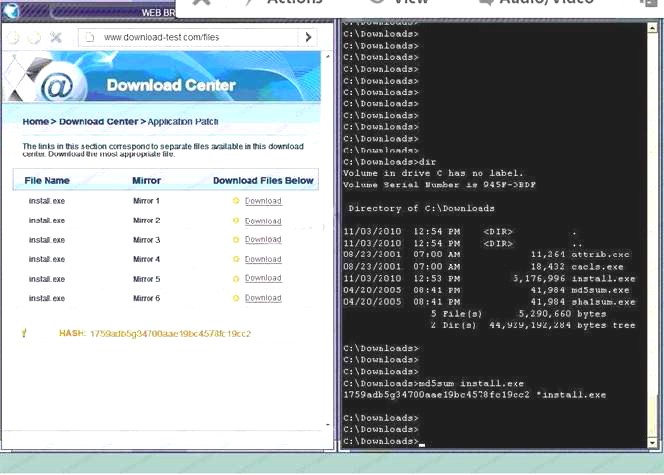 Finally, type in install.exe to install it and make sure there are no signature verification errors.
Finally, type in install.exe to install it and make sure there are no signature verification errors. - C. In this case the second link should be used (This may vary in actual exam). The first link showed the following error so it should not be used.
 Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown.Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show
Also, Two of the link choices used HTTP and not HTTPS as shown when hovering over the links as shown.Since we need to do this in the most secure manner possible, they should not be used.Finally, the second link was used and the MD5 utility of MD5sum should be used on the install.exe file as show - D. Make sure that the hash matches.Finally, type in install.exe to install it and make sure there are no signature verification error
Answer: A
NEW QUESTION 18
An organization has established the following controls matrix: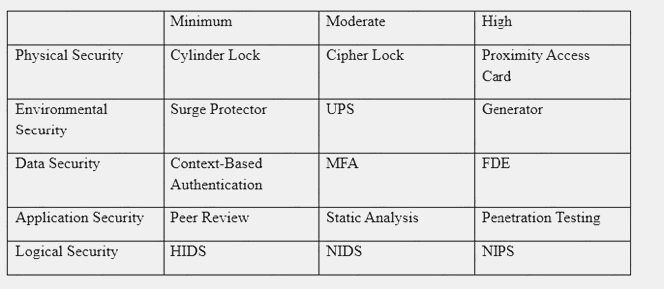
The following control sets have been defined by the organization and are applied in aggregate fashion:
Systems containing PII are protected with the minimum control set. Systems containing medical data are protected at the moderate level. Systems containing cardholder data are protected at the high level.
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
- A. Proximity card access to the server room, context-based authentication, UPS, and full-disk encryption for the database server.
- B. Cipher lock on the server room door, FDE, surge protector, and static analysis of all application code.
- C. Peer review of all application changes, static analysis of application code, UPS, and penetration testing of the complete system.
- D. Intrusion detection capabilities, network-based IPS, generator, and context-based authenticatio
Answer: D
NEW QUESTION 19
The latest independent research shows that cyber attacks involving SCADA systems grew an average of 15% per year in each of the last four years, but that this year’s growth has slowed to around 7%. Over the same time period, the number of attacks against applications has decreased or stayed flat each year. At the start of the measure period, the incidence of PC boot loader or BIOS based attacks was negligible. Starting two years ago, the growth in the number of PC boot loader attacks has grown exponentially. Analysis of these trends would seem to suggest which of the following strategies should be employed?
- A. Spending on SCADA protections should stay steady; application control spending should increase substantially and spending on PC boot loader controls should increase substantially.
- B. Spending on SCADA security controls should stay steady; application control spending should decrease slightly and spending on PC boot loader protections should increase substantially.
- C. Spending all controls should increase by 15% to start; spending on application controls should be suspended, and PC boot loader protection research should increase by 100%.
- D. Spending on SCADA security controls should increase by 15%; application control spending should increase slightly, and spending on PC boot loader protections should remain steady.
Answer: B
Explanation:
Spending on the security controls should stay steady because the attacks are still ongoing albeit reduced in occurrence Due to the incidence of BIOS-based attacks growing exponentially as the application attacks being decreased or staying flat spending should increase in this field. Incorrect Answers:
A: The SCADA security control spending and not the SCADA protection spending should stay steady. There is no need to in spending on application control.
C: There is no n increase spending on all security controls.
D: This is partly correct, but the spending on application control does not have to increase and the BIOS protections should increase since these attacks are now more prevalent.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 343
https://en.wikipedia.org/wiki/SCADA
NEW QUESTION 20
An enterprise with global sites processes and exchanges highly sensitive information that is protected under several countries’ arms trafficking laws. There is new information that malicious nation-state-sponsored activities are targeting the use of encryption between the geographically
disparate sites. The organization currently employs ECDSA and ECDH with P-384, SHA-384, and AES- 256-GCM on VPNs between sites. Which of the following techniques would MOST likely improve the resilience of the enterprise to attack on cryptographic implementation?
- A. Add a second-layer VPN from a different vendor between sites.
- B. Upgrade the cipher suite to use an authenticated AES mode of operation.
- C. Use a stronger elliptic curve cryptography algorithm.
- D. Implement an IDS with sensors inside (clear-text) and outside (cipher-text) of each tunnel between sites.
- E. Ensure cryptography modules are kept up to date from vendor supplying the
Answer: C
NEW QUESTION 21
......
Recommend!! Get the Full CAS-003 dumps in VCE and PDF From Surepassexam, Welcome to Download: https://www.surepassexam.com/CAS-003-exam-dumps.html (New 555 Q&As Version)
- Most Up-to-date XK0-004 Free Practice Questions For CompTIA Linux+ Certification Exam Certification
- Regenerate PT0-002 Free Dumps For CompTIA PenTest+ Certification Exam Certification
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (61-70)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (161-170)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (31-40)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (601-610)
- [2021-New] CompTIA LX0-103 Dumps With Update Exam Questions (21-30)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (111-120)
- Up To The Minute CompTIA Cybersecurity Analyst (CySA+) Certification Exam CS0-002 Free Practice Questions

