CS0-002 Exam Questions - Online Test
CS0-002 Premium VCE File

150 Lectures, 20 Hours

Want to know Actualtests CS0-002 Exam practice test features? Want to lear more about CompTIA CompTIA Cybersecurity Analyst (CySA+) Certification Exam certification experience? Study Certified CompTIA CS0-002 answers to Renew CS0-002 questions at Actualtests. Gat a success with an absolute guarantee to pass CompTIA CS0-002 (CompTIA Cybersecurity Analyst (CySA+) Certification Exam) test on your first attempt.
CompTIA CS0-002 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
An organization developed a comprehensive incident response policy. Executive management approved the policy and its associated procedures. Which of the following activities would be MOST beneficial to evaluate personnel’s familiarity with incident response procedures?
- A. A simulated breach scenario involving the incident response team
- B. Completion of annual information security awareness training by all employees
- C. Tabletop activities involving business continuity team members
- D. Completion of lessons-learned documentation by the computer security incident response team
- E. External and internal penetration testing by a third party
Answer: A
NEW QUESTION 2
The computer incident response team at a multinational company has determined that a breach of sensitive data has occurred in which a threat actor has compromised the organization’s email system. Per the incident response procedures, this breach requires notifying the board immediately. Which of the following would be the BEST method of communication?
- A. Post of the company blog
- B. Corporate-hosted encrypted email
- C. VoIP phone call
- D. Summary sent by certified mail
- E. Externally hosted instant message
Answer: C
NEW QUESTION 3
Which of the following technologies can be used to house the entropy keys for disk encryption on desktops and laptops?
- A. Self-encrypting drive
- B. Bus encryption
- C. TPM
- D. HSM
Answer: A
NEW QUESTION 4
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too much access to customer data. Developers use personal workstations, giving the company little to no visibility into the development activities.
Which of the following would be BEST to implement to alleviate the CISO's concern?
- A. DLP
- B. Encryption
- C. Test data
- D. NDA
Answer: D
NEW QUESTION 5
The help desk provided a security analyst with a screenshot of a user's desktop: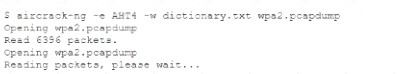
For which of the following is aircrack-ng being used?
- A. Wireless access point discovery
- B. Rainbow attack
- C. Brute-force attack
- D. PCAP data collection
Answer: B
NEW QUESTION 6
An organization is moving its infrastructure to the cloud in an effort to meet the budget and reduce staffing requirements. The organization has three environments: development, testing, and production. These environments have interdependencies but must remain relatively segmented.
Which of the following methods would BEST secure the company's infrastructure and be the simplest to manage and maintain?
- A. Create three separate cloud accounts for each environmen
- B. Configure account peering and security rules to allow access to and from each environment.
- C. Create one cloud account with one VPC for all environment
- D. Purchase a virtual firewall and create granular security rules.
- E. Create one cloud account and three separate VPCs for each environmen
- F. Create security rules to allow access to and from each environment.
- G. Create three separate cloud accounts for each environment and a single core account for network service
- H. Route all traffic through the core account.
Answer: C
NEW QUESTION 7
A cybersecurity analyst is responding to an incident. The company’s leadership team wants to attribute the incident to an attack group. Which of the following models would BEST apply to the situation?
- A. Intelligence cycle
- B. Diamond Model of Intrusion Analysis
- C. Kill chain
- D. MITRE ATT&CK
Answer: B
NEW QUESTION 8
A human resources employee sends out a mass email to all employees that contains their personnel records. A security analyst is called in to address the concern of the human resources director on how to prevent this from happening in the future.
Which of the following would be the BEST solution to recommend to the director?
- A. Install a data loss prevention system, and train human resources employees on its us
- B. Provide PII training to all employees at the compan
- C. Encrypt PII information.
- D. Enforce encryption on all emails sent within the compan
- E. Create a PII program and policy on how to handle dat
- F. Train all human resources employees.
- G. Train all employee
- H. Encrypt data sent on the company networ
- I. Bring in privacy personnel to present a plan on how PII should be handled.
- J. Install specific equipment to create a human resources policy that protects PII dat
- K. Train company employees on how to handle PII dat
- L. Outsource all PII to another compan
- M. Send the human resources director to training for PII handling.
Answer: A
NEW QUESTION 9
A security analyst is attempting to utilize the blowing threat intelligence for developing detection capabilities:
In which of the following phases is this APT MOST likely to leave discoverable artifacts?
- A. Data collection/exfiltration
- B. Defensive evasion
- C. Lateral movement
- D. Reconnaissance
Answer: A
NEW QUESTION 10
A security analyst is reviewing the following web server log: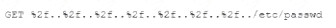
Which of the following BEST describes the issue?
- A. Directory traversal exploit
- B. Cross-site scripting
- C. SQL injection
- D. Cross-site request forgery
Answer: A
NEW QUESTION 11
Which of the following is the MOST important objective of a post-incident review?
- A. Capture lessons learned and improve incident response processes
- B. Develop a process for containment and continue improvement efforts
- C. Identify new technologies and strategies to remediate
- D. Identify a new management strategy
Answer: A
NEW QUESTION 12
A new on-premises application server was recently installed on the network. Remote access to the server was enabled for vendor support on required ports, but recent security reports show large amounts of data are being sent to various unauthorized networks through those ports. Which of the following configuration changes must be implemented to resolve this security issue while still allowing remote vendor access?
- A. Apply a firewall application server rule.
- B. Whitelist the application server.
- C. Sandbox the application server.
- D. Enable port security.
- E. Block the unauthorized networks.
Answer: B
NEW QUESTION 13
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets.
Which of the following should be considered FIRST prior to disposing of the electronic data?
- A. Sanitization policy
- B. Data sovereignty
- C. Encryption policy
- D. Retention standards
Answer: D
NEW QUESTION 14
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following: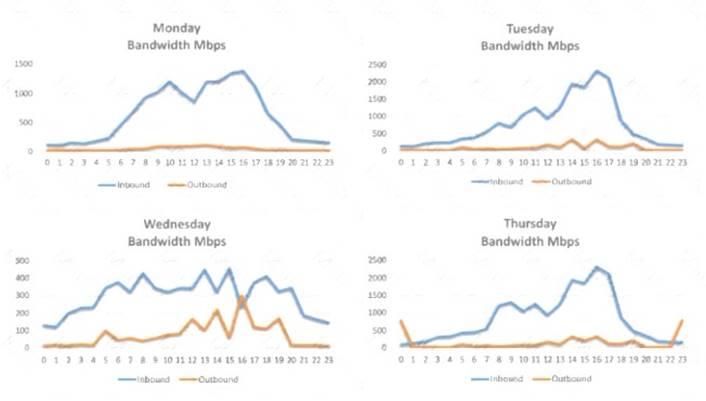
Which of the following should the analyst review to find out how the data was exfilltrated?
- A. Monday's logs
- B. Tuesday's logs
- C. Wednesday's logs
- D. Thursday's logs
Answer: D
NEW QUESTION 15
A security analyst is reviewing the logs from an internal chat server. The chat.log file is too large to review manually, so the analyst wants to create a shorter log file that only includes lines associated with a user demonstrating anomalous activity. Below is a snippet of the log: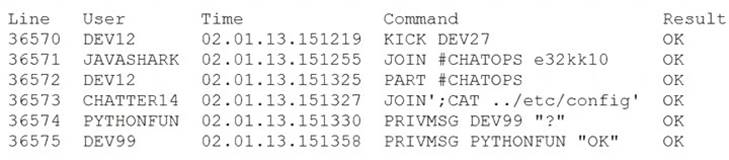
Which of the following commands would work BEST to achieve the desired result?
- A. grep -v chatter14 chat.log
- B. grep -i pythonfun chat.log
- C. grep -i javashark chat.log
- D. grep -v javashark chat.log
- E. grep -v pythonfun chat.log
- F. grep -i chatter14 chat.log
Answer: D
NEW QUESTION 16
During an investigation, a security analyst determines suspicious activity occurred during the night shift over the weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website.
Which of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
- A. An IPS signature modification for the specific IP addresses
- B. An IDS signature modification for the specific IP addresses
- C. A firewall rule that will block port 80 traffic
- D. A firewall rule that will block traffic from the specific IP addresses
Answer: D
NEW QUESTION 17
An analyst identifies multiple instances of node-to-node communication between several endpoints within the 10.200.2.0/24 network and a user machine at the IP address 10.200.2.5. This user machine at the IP address 10.200.2.5 is also identified as initiating outbound communication during atypical business hours with several IP addresses that have recently appeared on threat feeds.
Which of the following can be inferred from this activity?
- A. 10.200.2.0/24 is infected with ransomware.
- B. 10.200.2.0/24 is not routable address space.
- C. 10.200.2.5 is a rogue endpoint.
- D. 10.200.2.5 is exfiltrating data.
Answer: D
NEW QUESTION 18
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When conducting the scan, the analyst received the following code snippet of results: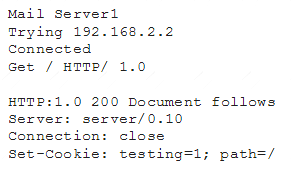
Which of the following describes the output of this scan?
- A. The analyst has discovered a False Positive, and the status code is incorrect providing an OK message.
- B. The analyst has discovered a True Positive, and the status code is correct providing a file not found error message.
- C. The analyst has discovered a True Positive, and the status code is incorrect providing a forbidden message.
- D. The analyst has discovered a False Positive, and the status code is incorrect providing a server error message.
Answer: B
NEW QUESTION 19
......
100% Valid and Newest Version CS0-002 Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/CS0-002-dumps.html (New 186 Q&As)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (91-100)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (21-30)
- How Many Questions Of SY0-701 Free Question
- How Many Questions Of CAS-004 Free Dumps
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (81-90)
- [2021-New] CompTIA CAS-002 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA SY0-501 Dumps With Update Exam Questions (1-10)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (111-120)
- [2021-New] CompTIA 220-902 Dumps With Update Exam Questions (161-170)
- [2021-New] CompTIA SK0-004 Dumps With Update Exam Questions (31-40)

