Identity-and-Access-Management-Architect Exam Questions - Online Test
Identity-and-Access-Management-Architect Premium VCE File

150 Lectures, 20 Hours

Actual of Identity-and-Access-Management-Architect torrent materials and brain dumps for Salesforce certification for candidates, Real Success Guaranteed with Updated Identity-and-Access-Management-Architect pdf dumps vce Materials. 100% PASS Salesforce Certified Identity and Access Management Architect (SU23) exam Today!
Salesforce Identity-and-Access-Management-Architect Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A security architect is rolling out a new multi-factor authentication (MFA) mandate, where all employees must go through a secure authentication process before accessing Salesforce. There are multiple Identity Providers (IdP) in place and the architect is considering how the "Authentication Method Reference" field (AMR) in the Login History can help.
Which two considerations should the architect keep in mind? Choose 2 answers
- A. AMR field shows the authentication methods used at IdP.
- B. Both OIDC and Security Assertion Markup Language (SAML) are supported but AMR must be implemented at IdP.
- C. High-assurance sessions must be configured under Session Security Level Policies.
- D. Dependency on what is supported by OpenID Connect (OIDC) implementation at IdP.
Answer: AB
Explanation:
The AMR field in the Login History shows the authentication methods used at the IdP level, such as password, MFA, or SSO. Both OIDC and SAML are supported protocols for SSO, but the IdP must implement the AMR attribute and pass it to Salesforce. References: Secure Your Users’ Identity, Salesforce Multi-Factor Authentication (MFA) and Single Sign-on (SSO)
NEW QUESTION 2
Universal Containers is budding a web application that will connect with the Salesforce API using JWT OAuth Flow.
Which two settings need to be configured in the connect app to support this requirement? Choose 2 answers
- A. The Use Digital Signature option in the connected app.
- B. The "web" OAuth scope in the connected app,
- C. The "api" OAuth scope in the connected app.
- D. The "edair_api" OAuth scope m the connected app.
Answer: AC
Explanation:
JWT OAuth Flow is a protocol that allows a client app to obtain an access token from Salesforce by using a JSON Web Token (JWT) instead of an authorization code. The JWT contains information about the client app and the user who wants to access Salesforce. To use this flow, the client app needs to have a connected app configured in Salesforce. The connected app is a framework that enables an external application to integrate with Salesforce using APIs and standard protocols. To support JWT OAuth Flow, two settings need to be configured in the connected app: The Use Digital Signature option, which enables the connected app to verify the signature of the JWT using a certificate.
The Use Digital Signature option, which enables the connected app to verify the signature of the JWT using a certificate. The “api” OAuth scope, which allows the connected app to access Salesforce APIs on behalf of the user.
The “api” OAuth scope, which allows the connected app to access Salesforce APIs on behalf of the user.
References: JWT OAuth Flow, Connected Apps, OAuth Scopes
NEW QUESTION 3
Which two considerations should be made when implementing Delegated Authentication? Choose 2 answers
- A. The authentication web service can include custom attributes.
- B. It can be used to authenticate API clients and mobile apps.
- C. It requires trusted IP ranges at the User Profile level.
- D. Salesforce servers receive but do not validate a user’s credentials.
- E. Just-in-time Provisioning can be configured for new users.
Answer: BE
Explanation:
Delegated authentication is a feature that allows Salesforce to delegate the authentication process to an external service of your choice1. When implementing delegated authentication, you should consider the following aspects2: The authentication web service can include custom attributes, such as user roles or permissions, in the response to Salesforce. These attributes can be used to update user records or trigger workflows in Salesforce2.
The authentication web service can include custom attributes, such as user roles or permissions, in the response to Salesforce. These attributes can be used to update user records or trigger workflows in Salesforce2. Delegated authentication can be used to authenticate API clients and mobile apps that use the SOAP API or REST API login() methods. However, it does not support OAuth 2.0 flows or other authentication methods2.
Delegated authentication can be used to authenticate API clients and mobile apps that use the SOAP API or REST API login() methods. However, it does not support OAuth 2.0 flows or other authentication methods2. Delegated authentication does not require trusted IP ranges at the User Profile level. However, you can use them to restrict access to Salesforce from specific IP addresses or ranges2.
Delegated authentication does not require trusted IP ranges at the User Profile level. However, you can use them to restrict access to Salesforce from specific IP addresses or ranges2. Salesforce servers receive but do not validate a user’s credentials. Instead, they pass the credentials to the external authentication service, which validates them and returns a response to Salesforce2.
Salesforce servers receive but do not validate a user’s credentials. Instead, they pass the credentials to the external authentication service, which validates them and returns a response to Salesforce2. Just-in-time provisioning can be configured for new users who log in with delegated authentication. Thi
Just-in-time provisioning can be configured for new users who log in with delegated authentication. Thi
feature allows Salesforce to create or update user accounts based on the information provided by the external authentication service3.
References: Delegated Authentication
Delegated Authentication Delegated Authentication Single Sign-On
Delegated Authentication Single Sign-On Just-in-Time Provisioning for Delegated Authentication
Just-in-Time Provisioning for Delegated Authentication
NEW QUESTION 4
Universal Containers (UC) has a Desktop application to collect leads for marketing campaigns. UC wants to extend this application to integrate with Salesforce to create leads. Integration between the desktop application and salesforce should be seamless. What Authorization flow should the Architect recommend?
- A. JWT Bearer Token flow
- B. Web Server Authentication Flow
- C. User Agent Flow
- D. Username and Password Flow
Answer: A
Explanation:
The JWT Bearer Token flow is an OAuth flow in which an external app (also called client or consumer app) sends a signed JSON string to Salesforce called JWT to obtain an access token. The access token can then be used by the external app to read and write data in Salesforce1. This flow is suitable for UC’s scenario because it allows seamless integration between the desktop application and Salesforce without requiring user interaction or login credentials2. The other options are not valid authorization flows for this scenario. The Web Server Authentication Flow and the User Agent Flow both require user interaction and redirection to the Salesforce OAuth authorization endpoint, which is not seamless3. The Username and Password Flow requires the external app to store the user’s login credentials, which is not secure or recommended3.
References: OAuth 2.0 JWT Bearer Flow for Server-to-Server Integration, OAuth Authorization Flows, Salesforce OAuth : JWT Bearer Flow
NEW QUESTION 5
A pharmaceutical company has an on-premise application (see illustration) that it wants to integrate with Salesforce.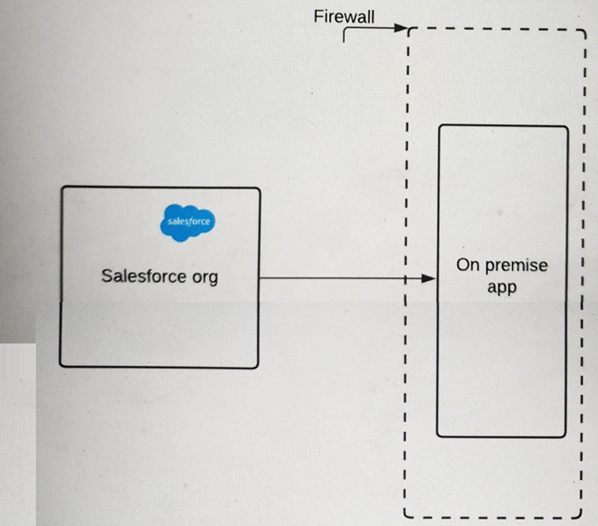
The IT director wants to ensure that requests must include a certificate with a trusted certificate chain to access the company's on-premise application endpoint.
What should an Identity architect do to meet this requirement?
- A. Use open SSL to generate a Self-signed Certificate and upload it to the on-premise app.
- B. Configure the company firewall to allow traffic from Salesforce IP ranges.
- C. Generate a certificate authority-signed certificate in Salesforce and uploading it to the on-premise application Truststore.
- D. Upload a third-party certificate from Salesforce into the on-premise server.
Answer: C
Explanation:
To ensure that requests must include a certificate with a trusted certificate chain to access the company’s
on-premise application endpoint, the identity architect should generate a certificate authority-signed certificate in Salesforce and upload it to the on-premise application Truststore. A certificate authority-signed certificate is a certificate that is issued by a trusted third-party entity, such as VeriSign or Thawte, that verifies the identity and authenticity of the certificate holder. A Truststore is a repository that stores trusted certificates and public keys. By generating a certificate authority-signed certificate in Salesforce and uploading it to the on-premise application Truststore, the identity architect can enable mutual authentication and secure communication between Salesforce and the on-premise application. The other options are not recommended for this scenario, as they either do not provide a trusted certificate chain, do not enable mutual authentication, or do not secure the communication. References: Create Certificate Authority-Signed Certificates, Mutual Authentication
NEW QUESTION 6
Universal Containers (UC) uses Salesforce to allow customers to keep track of the order status. The customers can log in to Salesforce using external authentication providers, such as Facebook and Google. UC is also leveraging the App Launcher to let customers access an of platform application for generating shipping labels. The label generator application uses OAuth to provide users access. What license type should an Architect recommend for the customers?
- A. Customer Community license
- B. Identity license
- C. Customer Community Plus license
- D. External Identity license
Answer: D
Explanation:
D is correct because External Identity license is designed for customers who need to log in to Salesforce using external authentication providers, such as Facebook and Google. External Identity license also supports App Launcher, which allows customers to access other applications from Salesforce using OAuth or OpenID Connect .
A is incorrect because Customer Community license is designed for customers who need to access data and records in Salesforce, such as cases, accounts, and contacts. Customer Community license does not support App Launcher or external authentication providers.
B is incorrect because Identity license is designed for employees who need to access multiple applications from Salesforce using SSO and App Launcher. Identity license does not support external authentication providers or customer data access.
C is incorrect because Customer Community Plus license is designed for customers who need to access data and records in Salesforce, as well as collaborate with other customers and partners. Customer Community Plus license does not support App Launcher or external authentication providers.
References: : Salesforce Licensing Module - Trailhead : Free Salesforce
Identity-and-Access-Management-Architect Questions … : Salesforce Licensing Module - Trailhead : Salesforce Licensing Module - Trailhead : Salesforce Licensing Module - Trailhead
NEW QUESTION 7
Which two security risks can be mitigated by enabling Two-Factor Authentication (2FA) in Salesforce? Choose 2 answers
- A. Users leaving laptops unattended and not logging out of Salesforce.
- B. Users accessing Salesforce from a public Wi-Fi access point.
- C. Users choosing passwords that are the same as their Facebook password.
- D. Users creating simple-to-guess password reset questions.
Answer: BC
Explanation:
Enabling Two-Factor Authentication (2FA) in Salesforce can mitigate the security risks of users accessing Salesforce from a public Wi-Fi access point or choosing passwords that are the same as their Facebook password. 2FA is an additional layer of protection beyond your password that requires users to verify their identity with another factor, such as a mobile app, a security key, or a verification code. This can prevent unauthorized access even if the user’s password is compromised or guessed by a malicious actor. The other options are not directly related to 2FA, but rather to user behavior or password policies.
NEW QUESTION 8
Northern Trail Outfitters (NTO) leverages Microsoft Active Directory (AD) for management of employee usernames, passwords, permissions, and asset access. NTO also owns a third-party single sign-on (SSO) solution. The third-party party SSO solution is used for all corporate applications, including Salesforce.
NTO has asked an architect to explore Salesforce Identity Connect for automatic provisioning and deprovisioning of users in Salesforce.
What role does identity Connect play in the outlined requirements?
- A. Service Provider
- B. Single Sign-On
- C. Identity Provider
- D. User Management
Answer: D
Explanation:
Salesforce Identity Connect is a tool that synchronizes user data between Microsoft Active Directory and Salesforce. It allows automatic provisioning and deprovisioning of users in Salesforce based on the changes made in Active Directory. Therefore, Identity Connect plays the role of user management in the outlined requirements. References: Identity Connect Implementation Guide, Identity Connect Overview
NEW QUESTION 9
Northern Trail Outfitters (NTO) is planning to roll out a partner portal for its distributors using Experience Cloud. NTO would like to use an external identity provider (idP) and for partners to register for access to the portal. Each partner should be allowed to register only once to avoid duplicate accounts with Salesforce.
What should a identity architect recommend to create partners?
- A. On successful creation of Partners using Self Registration page in Experience Cloud, create identity in Ping.
- B. Create a custom page m Experience Cloud to self register partner with Experience Cloud and Ping identity store.
- C. Create a custom web page in the Portal and create users in the IdP and Experience Cloud using published APIs.
- D. Allow partners to register through the IdP and create partner users in Salesforce through an API.
Answer: B
Explanation:
To create partners using an external identity provider (IdP) and avoid duplicate accounts with Salesforce, the identity architect should recommend creating a custom page in Experience Cloud to self register partner with Experience Cloud and Ping identity store. Ping is an IdP that supports OpenID Connect protocol, which allows users to sign in with an external identity provider and access Salesforce resources. By creating a custom page in Experience Cloud, the identity architect can use a custom registration handler to link the partner’s Ping identity with their Salesforce identity and prevent duplicate accounts. The custom page can also provide a seamless user experience for the partners. References: OpenID Connect Authentication Providers, Social Sign-On with OpenID Connect, Create a Custom Registration Handler
NEW QUESTION 10
which three are features of federated Single Sign-on solutions? Choose 3 answers
- A. It federates credentials control to authorized applications.
- B. It establishes trust between Identity store and service provider.
- C. It solves all identity and access management problems.
- D. It improves affiliated applications adoption rates.
- E. It enables quick and easy provisioning and deactivating of users.
Answer: ABD
Explanation:  It federates credentials control to authorized applications. This means that users can access multiple applications across different domains or organizations using one set of credentials, without having to share their passwords with each application1. The applications rely on a trusted identity provider (IdP) to authenticate the users and grant them access.
It federates credentials control to authorized applications. This means that users can access multiple applications across different domains or organizations using one set of credentials, without having to share their passwords with each application1. The applications rely on a trusted identity provider (IdP) to authenticate the users and grant them access. It establishes trust between Identity store and service provider. This means that the IdP and the service provider (SP) have a mutual agreement to exchange identity information using standard protocols, such as SAML, OpenID Connect, or OAuth2. The IdP and the SP also share metadata and certificates to ensure secure communication and verification.
It establishes trust between Identity store and service provider. This means that the IdP and the service provider (SP) have a mutual agreement to exchange identity information using standard protocols, such as SAML, OpenID Connect, or OAuth2. The IdP and the SP also share metadata and certificates to ensure secure communication and verification. It improves affiliated applications adoption rates. This means that users are more likely to use applications that are connected to their existing identity provider, as they do not have to create or remember multiple passwords3. This also reduces the friction and frustration of logging in to different applications, and enhances the user experience.
It improves affiliated applications adoption rates. This means that users are more likely to use applications that are connected to their existing identity provider, as they do not have to create or remember multiple passwords3. This also reduces the friction and frustration of logging in to different applications, and enhances the user experience.
The other options are not features of federated single sign-on solutions because: It solves all identity and access management problems. This is false, as federated single sign-on solutions only address the authentication aspect of identity and access management, not the authorization, provisioning, governance, or auditing aspects. Federated single sign-on solutions also have some challenges, such as complexity, interoperability, and security risks.
It solves all identity and access management problems. This is false, as federated single sign-on solutions only address the authentication aspect of identity and access management, not the authorization, provisioning, governance, or auditing aspects. Federated single sign-on solutions also have some challenges, such as complexity, interoperability, and security risks. It enables quick and easy provisioning and deactivating of users. This is not necessarily true, as
It enables quick and easy provisioning and deactivating of users. This is not necessarily true, as
federated single sign-on solutions do not automatically create or delete user accounts in the service provider applications. Users still need to be provisioned and deprovisioned manually or through other mechanisms, such as just-in-time provisioning or SCIM.
References: Federated Identity Management vs. Single Sign-On: What’s the Difference?, What is single sign-on?, Single Sign-On (SSO) Solution, [Identity Management vs. Access Management: What’s the Difference?], [Federated Identity Management Challenges], [Just-in-Time Provisioning for SAML], [SCIM User Provisioning]
NEW QUESTION 11
Universal Containers (UC) built an integration for their employees to post, view, and vote for ideas in Salesforce from an internal Company portal. When ideas are posted in Salesforce, links to the ideas are created in the company portal pages as part of the integration process. The Company portal connects to Salesforce using OAuth. Everything is working fine, except when users click on links to existing ideas, they are always taken to the Ideas home page rather than the specific idea, after authorization. Which OAuth URL parameter can be used to retain the original requested page so that a user can be redirected correctly after OAuth authorization?
- A. Redirect_uri
- B. State
- C. Scope
- D. Callback_uri
Answer: A
Explanation:
Threedirect_uri parameter is used to specify the URL that the user should be redirected to after OAuth
authorization1. The redirect_uri should match the one that was registered with the OAuth client application2. By using the redirect_uri parameter, the user can be redirected to the original requested page instead of the Ideas home page.
NEW QUESTION 12
Universal Containers (UC) has an existing Salesforce org configured for SP-Initiated SAML SSO with their Idp. A second Salesforce org is being introduced into the environment and the IT team would like to ensure they can use the same Idp for new org. What action should the IT team take while implementing the second org?
- A. Use the same SAML Identity location as the first org.
- B. Use a different Entity ID than the first org.
- C. Use the same request bindings as the first org.
- D. Use the Salesforce Username as the SAML Identity Type.
Answer: B
Explanation:
The Entity ID is a unique identifier for a service provider or an identity provider in SAML SSO. It is used to differentiate between different service providers or identity providers that may share the same issuer or login URL. In Salesforce, the Entity ID is automatically generated based on the organization ID and can be viewed in the Single Sign-On Settings page1. If you have a custom domain set up, you can use https:// [customDomain].my.salesforce.com as the Entity ID2. If you want to use the same IdP for two Salesforce orgs, you need to use different Entity IDs for each org, otherwise the IdP will not be able to distinguish them
and may send incorrect assertions. You can also use different certificates, issuers, or login URLs for each org, but using different Entity IDs is the simplest and recommended way3.
NEW QUESTION 13
Universal Containers (UC) has a desktop application to collect leads for marketing campaigns. UC wants to extend this application to integrate with Salesforce to create leads. Integration between the desktop application and Salesforce should be seamless. What Authorization flow should the Architect recommend?
- A. JWT Bearer Token Flow
- B. Web Server Authentication Flow
- C. User Agent Flow
- D. Username and Password Flow
Answer: B
Explanation:
This is an OAuth authorization flow that allows a web server application to obtain an access token to access Salesforce resources on behalf of the user1. This flow is suitable for integrating a desktop application with Salesforce, as it does not require the user to enter their credentials in the application, but rather redirects them to the Salesforce login page to authenticate and authorize the application2. This way, the integration between the desktop application and Salesforce is seamless and secure. The other options are not optimal for this requirement because: JWT Bearer Token Flow is an OAuth authorization flow that allows a client application to obtain an access token by sending a signed JSON Web Token (JWT) to Salesforce3. This flow does not involve user interaction, and requires the client application to have a certificate and a private key to sign the JWT. This flow is more suitable for server-to-server integration, not for desktop application integration.
JWT Bearer Token Flow is an OAuth authorization flow that allows a client application to obtain an access token by sending a signed JSON Web Token (JWT) to Salesforce3. This flow does not involve user interaction, and requires the client application to have a certificate and a private key to sign the JWT. This flow is more suitable for server-to-server integration, not for desktop application integration. User Agent Flow is an OAuth authorization flow that allows a user-agent-based application (such as a browser or a mobile app) to obtain an access token by redirecting the user to Salesforce and receiving the token in the URL fragment4. This flow is not suitable for desktop application integration, as it requires the application to parse the URL fragment and store the token securely.
User Agent Flow is an OAuth authorization flow that allows a user-agent-based application (such as a browser or a mobile app) to obtain an access token by redirecting the user to Salesforce and receiving the token in the URL fragment4. This flow is not suitable for desktop application integration, as it requires the application to parse the URL fragment and store the token securely. Username and Password Flow is an OAuth authorization flow that allows a client application to obtain an access token by sending the user’s username and password to Salesforce5. This flow is not recommended for desktop application integration, as it requires the user to enter their credentials in the application, which is not secure or seamless. References: OAuth Authorization Flows, Implement the OAuth 2.0 Web Server Flow, JWT-Based Access Tokens (Beta), User-Agent Flow, Username-Pass Flow
Username and Password Flow is an OAuth authorization flow that allows a client application to obtain an access token by sending the user’s username and password to Salesforce5. This flow is not recommended for desktop application integration, as it requires the user to enter their credentials in the application, which is not secure or seamless. References: OAuth Authorization Flows, Implement the OAuth 2.0 Web Server Flow, JWT-Based Access Tokens (Beta), User-Agent Flow, Username-Pass Flow
NEW QUESTION 14
A web service is developed that allows secure access to customer order status on the Salesforce Platform. The service connects to Salesforce through a connected app with the web server flow. The following are the required actions for the authorization flow:
* 1. User Authenticates and Authorizes Access
* 2. Request an Access Token
* 3. Salesforce Grants an Access Token
* 4. Request an Authorization Code
* 5. Salesforce Grants Authorization Code
What is the correct sequence for the authorization flow?
- A. 1, 4, 5, 2, 3
- B. 4, 1, 5, 2, 3
- C. 2, 1, 3, 4, 5
- D. 4,5,2, 3, 1
Answer: B
Explanation:
The web server flow is an OAuth 2.0 authorization code grant type, which follows this sequence of steps: The client app requests an authorization code from Salesforce by redirecting the user to the authorization endpoint.
The client app requests an authorization code from Salesforce by redirecting the user to the authorization endpoint. The user authenticates and authorizes access to the client app.
The user authenticates and authorizes access to the client app. Salesforce grants an authorization code and redirects the user back to the client app.
Salesforce grants an authorization code and redirects the user back to the client app. The client app requests an access token from Salesforce by sending the authorization code to the token endpoint.
The client app requests an access token from Salesforce by sending the authorization code to the token endpoint. Salesforce grants an access token and a refresh token to the client app. References: OAuth Authorization Flows, Authorize Apps with OAuth
Salesforce grants an access token and a refresh token to the client app. References: OAuth Authorization Flows, Authorize Apps with OAuth
NEW QUESTION 15
An identity architect has built a native mobile application and plans to integrate it with a Salesforce Identity solution. The following are the requirements for the solution:
* 1. Users should not have to login every time they use the app.
* 2. The app should be able to make calls to the Salesforce REST API.
* 3. End users should NOT see the OAuth approval page.
How should the identity architect configure the Salesforce connected app to meet the requirements?
- A. Enable the API Scope and Offline Access Scope, upload a certificate so JWT Bearer Flow can be used and then set the connected app access settings to "Admin Pre-Approved".
- B. Enable the API Scope and Offline Access Scope on the connected app, and then set the connected app to access settings to 'Admin Pre-Approved".
- C. Enable the Full Access Scope and then set the connected app access settings to "Admin Pre-Approved".
- D. Enable the API Scope and Offline Access Scope on the connected app, and then set the Connected App access settings to "User may self authorize".
Answer: A
Explanation:
JWT Bearer Flow is an OAuth 2.0 flow that allows a client app to obtain an access token without user interaction. It requires a certificate to sign the JWT and the API and Offline Access scopes to access the Salesforce REST API and refresh the token. The connected app must also be pre-approved by the admin to avoid the OAuth approval page. References: OAuth 2.0 JWT Bearer Flow for Server-to-Server Integration, Authorize an Org Using the JWT Flow
NEW QUESTION 16
Universal containers (UC) is building a mobile application that will make calls to the salesforce REST API. Additionally, UC would like to provide the optimal experience for its mobile users. Which two OAuth scopes should UC configure in the connected App? Choose 2 answers
- A. Refresh token
- B. API
- C. full
- D. Web
Answer: AB
Explanation:
The two OAuth scopes that UC should configure in the connected app are: Refresh token. This scope allows the mobile app to obtain a refresh token from Salesforce when it obtains an access token. A refresh token can be used to obtain a new access token when the previous one expires or becomes invalid. This scope enables UC to provide an optimal experience for its mobile users by reducing the number of login prompts and authentication failures.
Refresh token. This scope allows the mobile app to obtain a refresh token from Salesforce when it obtains an access token. A refresh token can be used to obtain a new access token when the previous one expires or becomes invalid. This scope enables UC to provide an optimal experience for its mobile users by reducing the number of login prompts and authentication failures. API. This scope allows the mobile app to make REST API calls to Salesforce using the access token.
API. This scope allows the mobile app to make REST API calls to Salesforce using the access token.
The REST API allows the mobile app to access or manipulate data and metadata in Salesforce using HTTP methods. This scope enables UC to build a custom mobile app that can connect to Salesforce and perform various operations on Salesforce resources. References: [OAuth Scopes], [Connected Apps], [Refresh Token], [REST API]
References: [OAuth Scopes], [Connected Apps], [Refresh Token], [REST API]
NEW QUESTION 17
Universal Containers want users to be able to log in to the Salesforce mobile app with their Active Directory password. Employees are unable to use mobile VPN.
Which two options should an identity architect recommend to meet the requirement? Choose 2 answers
- A. Active Directory Password Sync Plugin
- B. Configure Cloud Provider Load Balancer
- C. Salesforce Trigger & Field on Contact Object
- D. Salesforce Identity Connect
Answer: AD
Explanation:
Active Directory Password Sync Plugin allows users to log in to Salesforce with their Active Directory password without using a VPN. Salesforce Identity Connect synchronizes users and groups between Active Directory and Salesforce and enables single sign-on. References: Active Directory Password Sync Plugin, Salesforce Identity Connect
NEW QUESTION 18
A manufacturer wants to provide registration for an Internet of Things (IoT) device with limited display input or capabilities.
Which Salesforce OAuth authorization flow should be used?
- A. OAuth 2.0 JWT Bearer How
- B. OAuth 2.0 Device Flow
- C. OAuth 2.0 User-Agent Flow
- D. OAuth 2.0 Asset Token Flow
Answer: B
Explanation:
The OAuth 2.0 Device Flow is a type of authorization flow that allows users to register an IoT device with limited display input or capabilities, such as a smart TV, a printer, or a smart speaker1. The device flow works as follows1: The device displays or reads out a verification code and a verification URL to the user.
The device displays or reads out a verification code and a verification URL to the user. The user visits the verification URL on another device, such as a smartphone or a laptop, and enters the verification code.
The user visits the verification URL on another device, such as a smartphone or a laptop, and enters the verification code. The user logs in to Salesforce and approves the device.
The user logs in to Salesforce and approves the device. The device polls Salesforce for an access token using the verification code.
The device polls Salesforce for an access token using the verification code. Salesforce returns an access token to the device, which can then access Salesforce APIs.
Salesforce returns an access token to the device, which can then access Salesforce APIs.
References: OAuth 2.0 Device Flow
OAuth 2.0 Device Flow
NEW QUESTION 19
Universal Containers (UC) would like to enable self-registration for their Salesforce Partner Community Users. UC wants to capture some custom data elements from the partner user, and based on these data elements, wants to assign the appropriate Profile and Account values.
Which two actions should the Architect recommend to UC1 Choose 2 answers
- A. Configure Registration for Communities to use a custom Visualforce Page.
- B. Modify the SelfRegistration trigger to assign Profile and Account.
- C. Modify the CommunitiesSelfRegController to assign the Profile and Account.
- D. Configure Registration for Communities to use a custom Apex Controller.
Answer: CD
Explanation:
To enable self-registration for partner community users, UC should modify the CommunitiesSelfRegController class to assign the Profile and Account values based on the custom data elements captured from the partner user. UC should also configure Registration for Communities to use a custom Apex controller that extends the CommunitiesSelfRegController class and overrides the default registration logic3.
References: Customize Self-Registration
Customize Self-Registration
NEW QUESTION 20
Universal Containers (UC) has Active Directory (AD) as their enterprise identity store and would like to use it for Salesforce user authentication. UC expects to synchronize user data between Salesforce and AD and Assign the appropriate Profile and Permission Sets based on AD group membership. What would be the optimal way to implement SSO?
- A. Use Active Directory with Reverse Proxy as the Identity Provider.
- B. Use Microsoft Access control Service as the Authentication provider.
- C. Use Active Directory Federation Service (ADFS) as the Identity Provider.
- D. Use Salesforce Identity Connect as the Identity Provider.
Answer: D
Explanation:
The optimal way to implement SSO with Active Directory as the enterprise identity store is to use Salesforce Identity Connect as the identity provider. Salesforce Identity Connect is a software that integrates Microsoft Active Directory with Salesforce and enables single sign-on (SSO) using SAML. It also allows user data synchronization between Active Directory and Salesforce and profile and permission set assignment based on Active Directory group membership. Option A is not a good choice because using Active Directory with reverse proxy as the identity provider may not be supported by Salesforce or may require additional configuration and customization. Option B is not a good choice because using Microsoft Access Control Service as the authentication provider may not be available, as Microsoft has retired this service in 2018. Option C is not a good choice because using Active Directory Federation Service (ADFS) as the identity provider may not allow user data synchronization or profile and permission set assignment based on Active Directory group membership, unless it is combined with another tool such as Salesforce Identity Connect.
References: Salesforce Identity Connect Implementation Guide, Single Sign-On Implementation Guide
NEW QUESTION 21
......
Thanks for reading the newest Identity-and-Access-Management-Architect exam dumps! We recommend you to try the PREMIUM DumpSolutions.com Identity-and-Access-Management-Architect dumps in VCE and PDF here: https://www.dumpsolutions.com/Identity-and-Access-Management-Architect-dumps/ (246 Q&As Dumps)
- Real Salesforce Identity-and-Access-Management-Architect Preparation Labs Online
- Salesforce ADM-201 Exam Dumps 2021
- How Many Questions Of Marketing-Cloud-Email-Specialist Exam Price
- [2021-New] Salesforce Sales-Cloud-Consultant Dumps With Update Exam Questions (71-80)
- [2021-New] Salesforce Sales-Cloud-Consultant Dumps With Update Exam Questions (131-140)
- The Secret Of Salesforce Identity-and-Access-Management-Architect Practice
- Salesforce ADM-201 Dumps Questions 2021
- [2021-New] Salesforce Sales-Cloud-Consultant Dumps With Update Exam Questions (1-10)
- The Secret Of Salesforce PDII Test Question
- The Most Recent Guide To Marketing-Cloud-Email-Specialist Questions Pool

